Repl ransomware (Virus Removal Instructions) - Decryption Steps Included
Repl virus Removal Guide
What is Repl ransomware?
Repl is a ransomware-type virus that aims at locking people's files and collecting ransom payment for a decryptor
Repl ransomware is the latest strain of the Djvu and STOP ransomware family that keeps attacking Windows users since 2017. This cyber infection is dangerous for any OS versions, including Windows 10, Windows 8, Windows 8.1, and Windows 7[1], though the latter is by far the most frequently affected due to the end of Windows support.
The virus is most actively spread via cracks and keygens on P2P sites and other sources where people can get pirated software unrestricted. Once the payload is launched, the Repl virus launches the payload and starts scanning the machine for files compatible with the AES cipher. Consequently, personal files get a .repl file marker and a _readme.txt note inform about an expected $980 ransom payment. Crooks may try to pretend compassionate by offering a 50% discount ($480) if the user is in 72 hours' time of payment.
| Name | Repl |
|---|---|
| Type | Ransomware/crypto-malware |
| Family | Djvu/STOP |
| OS | Windows OS exceptionally |
| Appendix | .repl |
| Text note | _readme.txt |
| Price | $980 or $490 if the payment is transferred with 72 hours |
| Contacts | helpmanager@mail.ch; restoremanager@firemail.cc |
| Removal | A full scan with a robust anti-virus program |
| post-ransomware steps | Removing the ransomware is not the end of the system's repair. Malicious software leaves its footprint within Windows Registry, startup processes, and system files. Damaging such components can lead to crashes eventually, so prevent this from happening with the help of FortectIntego |
| REPL fILE DECRYPTION | The official decryption tool is not available, though users can use in-built Windows features or third-party software for data recovery. A full guide on how to recover the data is provided at the end of this article |
Repl virus is a cyber threat that is extremely unpleasant to discover on the system. It completely restricts access to the personal files and features the audacity to demand the payment in exchange for those personal photos, documents, databases, and videos. For this purpose, people should take precautionary measures and mind all security recommendations to avoid downloading such and similar infections.
Once the Repl ransomware lands on the target machine, it runs the AES cipher (or another) and uses a sophisticated mathematical structure to completely lock detected files. In addition, it starts placing malicious executables to ensure persistence and prevent removal.
Some malicious components of the Repl file virus can be detected within the Windows Task Manager. Typically, they manifest themself by misusing CPU power, which abnormally jumps to extreme hight. Additionally, the malware may also be programmed to perform the following functions:
- run commands via Elevated Windows PowerShell to remove Shadow Copies;
- inject malicious scripts into the web browser and reroute the traffic to malware-laden sites to make people download malware like AzoRult;
- disable anti-virus programs. It can do it by compromising the settings on the Service Manager;
- the ransomware may inject suspicious registry keys, which may eventually trigger BSODs or other system errors. For this reason, experts recommend scanning the system with FortectIntego tool after Repl removal.
As for the Repl removal, practically it's impossible to detect all the malicious entries that it is responsible for running. Therefore, to stop dangerous activities that it is performing behind your back, arm yourself with the most powerful anti-virus program, restart the machine into Safe Mode, and run a full system scan.
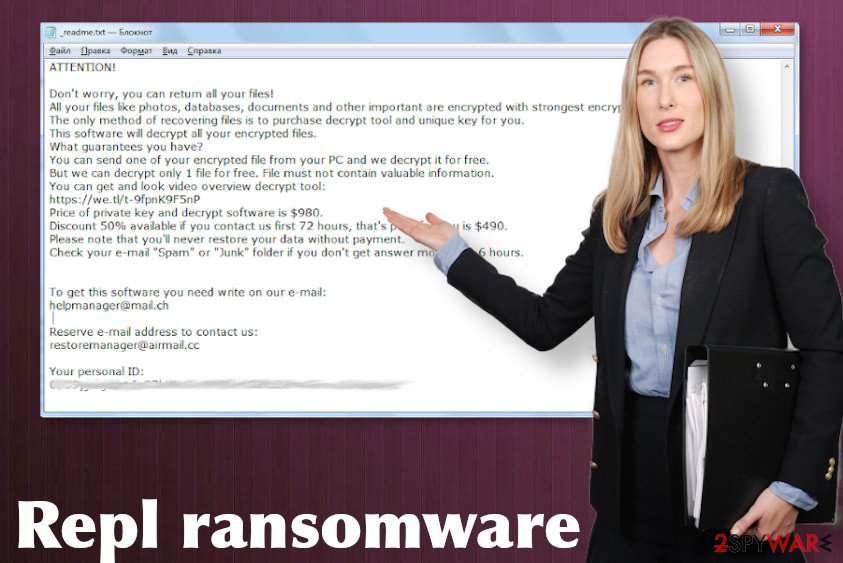
Do not pay for the Repl decryptor
If the unsuspecting PC user runs a ransomware-infected file, the malicious script is activated and the wheel turns up. First of all, the virus runs in the background to ensure a smooth launch of all malicious files. The most malicious processes of the Repl ransomware is the encryption algorithm. Typically, it uses the AES cipher, though no one knows when other algorithms can be used.
If the encryption is successfully launched, the ransomware drops a _readme.txt note, which contains such information:
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-BTtULebL7F
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch;Reserve e-mail address to contact us:
restoremanager@firemail.cc
Your personal ID
The next obvious symptom indicating that the attack has been successfully initiated is the Repl files. All of the personal files will contain such extension leaving them completely inaccessible.
Locked personal files can be a miserable experience. However, paying the ransom to unlock Repl virus files is not recommended. Not only because the support for criminals stimulates them to proceed with cybercrimes. Not paying is recommended because this move does not ensure that you'll get a functional decryption software.
Instead of paying, remove Repl ransomware virus from the system using a professional anti-virus. Then copy the locked files to the cold storage, e.g. external hard drive or cloud. Finally, try an alternative .Repl file recovery methods, for example, download Data Recovery Pro or try the previous Windows version.
Unfortunately, the official STOP/Djvu decryptor is not likely to work in this case. The Repl virus is using online IDs, meaning that all IDs a unique and the malware transmits them to criminals by contacting them via the C2 server. Besides, DO NOT download other free Djvu decryption tools circulating freely on the Internet, as you can download another ransomware and get your files re-encrypted.
Instead of relying on any offers regardless of their safety, make sure to remove Repl virus completely. The sooner you get rid of it, the less damage it initiates to the system. Run a full scan with a professional anti-virus and then try file recovery methods listed below.
Intricate methods used to spread ransomware leave thousands as victims
Spam. Spam messages and their malicious attachments top the charts of the malware distribution methods used by criminals. According to NoVirus.uk[2] experts, people are still recklessly treating email messages that contain suspicious attachments or links. That's a problem, which then cost people nerves and money as they cannot access their own files right after downloading malicious ransomware.
Illegal software. As long as pirating exists, hackers will be sure that they have a medium to spread malware. Software cracks, keygens, games, and other software that is distributed in third-party sources, movie download sites, Torrenting sites, and domains like The Pirate Bay. They are frequently misused by hackers and the content, such as software updates, ads, links should be bypassed to keep the system safe.
Lack of a system's security. Millions of people are using outdated security software or not use it at all. The unprotected system is vulnerable to various cyber infections and a single click on script-infected commercial may end up with serious computer security issues.
A full guide on ransomware removal and Repl file recovery options
Repl ransomware removal should be performed as soon as you notice your files renamed. Any attempt to remove the file extension fails because the virus locks them using strong mathematical encryption, do the only way to recover them is to use a unique key.
Keep in mind that the Repl removal process can be done only by leaning on a reputable anti-virus program. Before launching a scan, make sure that it's fully up-to-date because outdated virus definitions[3] may be the culprit why your AV program fails to do the job.
To remove Repl ransomware virus completely, we recommend using SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful anti-malware solution. If the software is blocked by the virus and you cannot launch it no matter how hard you try, make an attempt to launch it while in Safe Mode or enable System Restore as explained below.
Getting rid of Repl virus. Follow these steps
Manual removal using Safe Mode
Repl virus removal can be denied if the virus blocks the process of AV tools within the Command Prompt. To run a scan, boot Windows into Safe Mode.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Repl using System Restore
Safe Mode did not work? Although that's a rare case, it may happen for unknown reasons. Thus, you should try to enable a System Restore point that has been created before the ransomware attacked it.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Repl. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Repl from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Appearance of .Repl extension indicates a dangerous infection that is lurking on your machine. Try the below-given data recovery steps as they might help you to restore some of your encrypted files.
If your files are encrypted by Repl, you can use several methods to restore them:
Download Data Recovery Pro
Use third-party software, such as Data Recovery Pro, to try to restore some of the Repl files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Repl ransomware;
- Restore them.
Enable Windows Previous Versions feature and recover some files
If you've been taking advantage of the System Restore feature before, then try to recover stand-alone files by exploiting their previous versions.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
There is not Repl decryption software
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Repl and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Danny Palmer. Windows 7 end of life: Security risks and what you should do next. ZDNet. Business security news.
- ^ SECURITY AND SPYWARE NEWS. NoVirus. Virus and spyware news.
- ^ Out of date and expired cybersecurity software almost as risky as no protection. Trend Micro. Cybersecurity experts.





















