S.O.V.A. Android trojan (virus) - Free Guide
S.O.V.A. Android trojan Removal Guide
What is S.O.V.A. Android trojan?
S.O.V.A. is malware that steals financial data from various Android devices

S.O.V.A. is a mobile banking Trojan that targets all types of Android devices to steal personal details from them. The malware steals user credentials used to access banking apps and can also steal other financial data while operational. It affects clients of numerous banks in countries like the USA, Spain, and Russia, although most recently, it has focused on banks mainly operating in India, including Canara Bank, PNB, SBI, and others.[1] It also targets other apps related to financing, including those related to cryptocurrency. In total, over 200 apps are targeted by SOVA.
If you have recently downloaded a banking app from unofficial sources, you may be infected, and you should immediately take action to remove the trojan. Those affected may suffer from the immediate loss of funds from various financial accounts, phishing[2] campaigns being launched against them, and even identity theft.
Common trojans that are focused on stealing details from users or acting as vectors for other threats can be spread via email attachments. On Gmail or OneNote systems, emails with document attachments can lead to malicious injections of the trojans that can lead to other serious infections of computer viruses. Do not open suspicious email on phones or computers to avoid this.
| Name | S.O.V.A. Trojan |
| Type | Malware, data-stealer |
| Target platform | Android |
| Purpose | Steals various personal and financial information from the phone or tablet, including bank login credentials, crypto-wallets, etc. |
| Distribution | Spreads via fake apps that imitate banking apps |
| Removal | Perform a full device scan with SpyHunter 5Combo Cleaner, Malwarebytes security software |
| Optimization | To make sure that all leftover and junk files are eliminated, use FortectIntego |
Infiltration
Since SOVA is Android-based malware, its infiltration methods are relatively limited. It is not surprising that the cybercriminals behind it chose the most commonly used technique for this platform – fake banking applications. Apps are made in a way that makes them look identical to the official ones, so users may not notice any initial differences.
While most users would not go to suspicious websites to install banking apps, crooks come up with ways to trick users regardless. Typically, people are redirected to phishing websites that look legitimate and often come with logos of legitimate companies such as Amazon or Chrome. Likewise, users may receive an SMS that includes a link urging users to download and install the alleged banking app.
To avoid such scenarios, it is recommended not to interact with websites that are not legitimate – all banks have listings of their apps via their official websites or Google Play Store and would never message you a link to download the app. Likewise, having reputable security software running may also stop most of the malware from being executed on the system.
Operation
During the installation, SOVA Trojan does not immediately ask for any special permissions, but immediately after, it enables Android Accessibility Services. With the help of these services, malware can control the device in various ways while imitating the gestures users would perform.
Very quickly, malware reads the list of the installed apps on the device and immediately sends it over to the attackers' Command & Control[3] server. This way, it can see which applicable applications are installed on the device – data can be exfoliated from them. At this stage, the C&C puts the list of addresses for each targeted app within an XML file and delivers it back to the virus. The malware and the remote server interactions are then used to control these targeted apps.
Soon after the connection is established, S.O.V.A. malware begins its malicious operations. It can perform the following actions while running on the affected system:
- read and steal keystrokes
- add overlays over existing apps
- bypass two-factor authentication by stealing its tokens
- mimic banking applications
- take screenshots and record video
- imitate gestures to control the device via Android Accessibility Services
- Copy and paste
- Steal cookies.
Looking at these capabilities, it becomes clear that the attackers are not joking about their operations, as the impact can be detrimental. Attackers may access users' online banking, withdraw or transfer funds or even steal their identities.
According to numerous reports, SOVA is still in development, as adverts for it claimed so. The creators said that they are planning to implement functionality for DDoS attacks, ransomware features, and more.
How to remove S.O.V.A. Trojan
It goes without saying that most users nowadays employ their Android phones to perform various daily tasks quickly and efficiently. This is precisely why cybercriminals target these devices more often, as they can make a maximum amount of profits via stealing sensitive user information or inserting ads into their devices illegally.
CapraRAT is another Android trojan that mainly targets Indian government officials, so it seems like India has become the recent target of cybercriminal groups. It is not surprising that it's the case, considering that India has extremely high population numbers.
It is imperative to remove malware from the device as soon as possible. However, those who try uninstalling the app in a regular way would not succeed, as it prevents users from tampering with it in any way. There are two ways out of this – either employing reputable anti-malware solutions such as SpyHunter 5Combo Cleaner or Malwarebytes or using a factory reset on the phone.
With the latter option, you would lose all your personal files, including photos, so we strongly recommend trying security apps instead. Note that instructions for performing factory reset differ depending on the phone model and Android version, so refer to the manufacturer instructions on the official websites.
If not going for a factory reset, you should also make sure you clean your browser caches from cookies and other data. For automatic option, you can choose FortectIntego, although manual solution is also available:
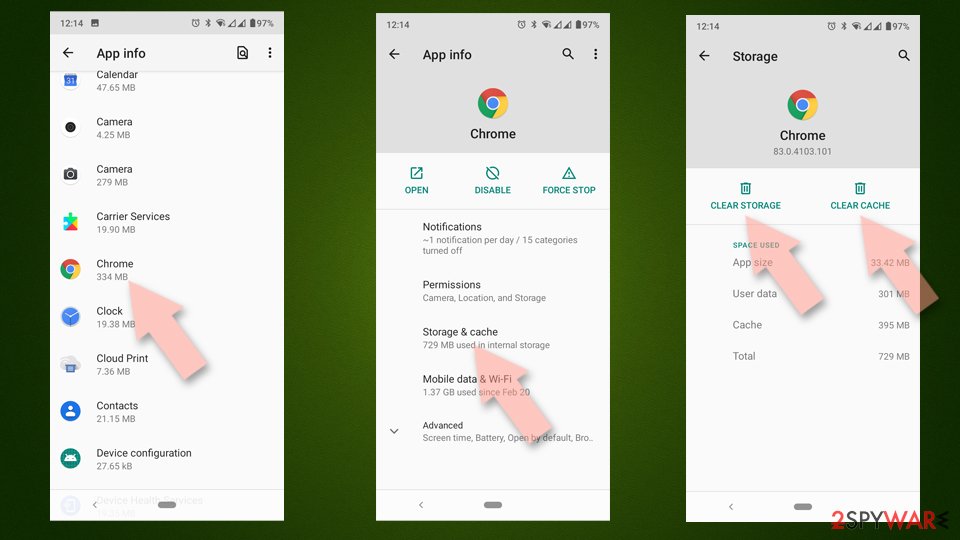
- Go to Settings > Apps/Applications.
- Expand the full list of the installed apps.
- Tap on Chrome and select Storage & cache.
- Clear storage and clear cache of the app.
How to prevent from getting trojans
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ What us SOVA virus: Banks warn customers of virus targeting banking apps. Economic Times. Business-focused site.
- ^ Phishing attacks. Imperva. Application and data security.
- ^ Command and control. Wikipedia. The free encyclopedia.
