Sality virus (Virus Removal Instructions) - updated Oct 2019
Sality virus Removal Guide
What is Sality virus?
Sality – is a self-propagating worm that was first introduced back in 2003 but is still prevalent today

Sality virus is a complex and multi-functional malware family that was first spotted in the wild back in 2003. Capable of spreading via infected removable drives and network shares, the worm operates by infecting all the .exe and .scr files on the host system – it is a typical functionality of a virus.
Security researchers believe that the Sality virus originated in Russia and evolved significantly over the years. Since 2010, the malware employed rootkit[1] capabilities, as well as used peer-to-peer network (botnet) to communicate with the infected computers. While different versions exhibit different symptoms and perform particular functions on the infected computer, most Sality variants are worms[2] that are capable of replicating themselves by using autorun[3] functionality.
Sality virus family is relatively old, but by no means, it is no longer a threat. It can use sophisticated evasion techniques like feeding its .dll files directly into memory and naming the main executables by using randomly generated names, which consequently prevents AV detection. Besides being able to send out spam, record keystrokes, steal sensitive information, etc., Sality is also continually communicating with its remote server to receive necessary updates and improve its functionality by implementing new modules (such as Trojan downloader, for example).
| SUMMARY | |
| Name | Sality virus |
| Type | In early stages, the virus was a relatively primitive file infector, but evolved into a self-propagating worm |
| Alternative names | SaILoad, SaliCode, Spamta, Kukacka, Kookoo, Vilsel |
| First spotted | The first sightings on the this virus family were spotted back in 2003 |
| Most affected countries | USA, India, Mexico, Russia, France, Ukraine, Romania, etc. |
| Related files | amsint32.sys (placed into Device folder) and wmdrtc32.dll (placed into %SYSTEM% folder) |
| Spread | Copies itself to remote and removable drives |
| Capabilities |
|
| Symptoms | Security software stops working, registry editor becomes unavailable, installation of unknown programs or files, the presence of amsint32.sys |
| Detection and elimination | Due to Sality virus capabilities, removing it might become extremely difficult. However, the infected users should access safe Mode with Networking in order to temporarely stop the functionality of malware and then perform a full system scan using security software like FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes |
For the infection process, Sality virus drops two different .dll files (wmdrtc32.dll and wmdrtc32.dl_) into %SYSTEM% folder, which are later executed. However, more advanced variants of the worm do not drop any DLLs into the system but instead use the memory, meaning, no files are written on the disk. During the infection process, Sality may create a random driver file and place it into the %SYSTEM%\drivers folder.
Sality virus executes several sets of commands that infect all the EXE and SCR files located on the Windows computer. The worm then quickly spreads to all the virtual and physical devices connected to the same network. It also modifies the original host code at the entry point to reroute the execution to the polymorphic[4] viral code – it runs mutated algorithms to perform the same tasks each time the computer is booted. Additionally, Sality worm makes several changes in Windows Registry to be able to start with every Windows boot. The affected keys include (nevertheless, there are also several other keys that the virus creates, modifies, and deletes):
HKEY_CURRENT_USER\Software\Microsoft\Windows\ShellNoRoam
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Sality virus works as a malware downloader, which uses a preset list of URLs that point to the source where additional files can be downloaded, decrypted, and then executed. The cyber threat uses an RC4 encryption algorithm to encrypt and decrypt data used in the host infection process.
After infecting the machine, Sality virus uses lists of predetermined URLs to establish multiple HTTP connections, which consequently feeds the payload with the newest updates and can also inject new modules into the affected computer.
To be able to remove Sality virus, it is important not to ignore signs of the infection, which include:
- The installed security software starts malfunctioning or is terminated;
- Security-related services and processes are stopped;
- Booting into Safe Mode becomes impossible;
- The malware starts sending malicious emails;
- The presence of a malicious file amsint32.sys located in %SystemRoot%\system32\drivers
Sality virus removal can be a complicated task because it can name its own executable by any name. Therefore, AV engines that use a preset list of malware names to detect it might fail to do so. Nevertheless, please check the last part of the article for full eradication instructions, and then you can clean all the malware traces using FortectIntego.
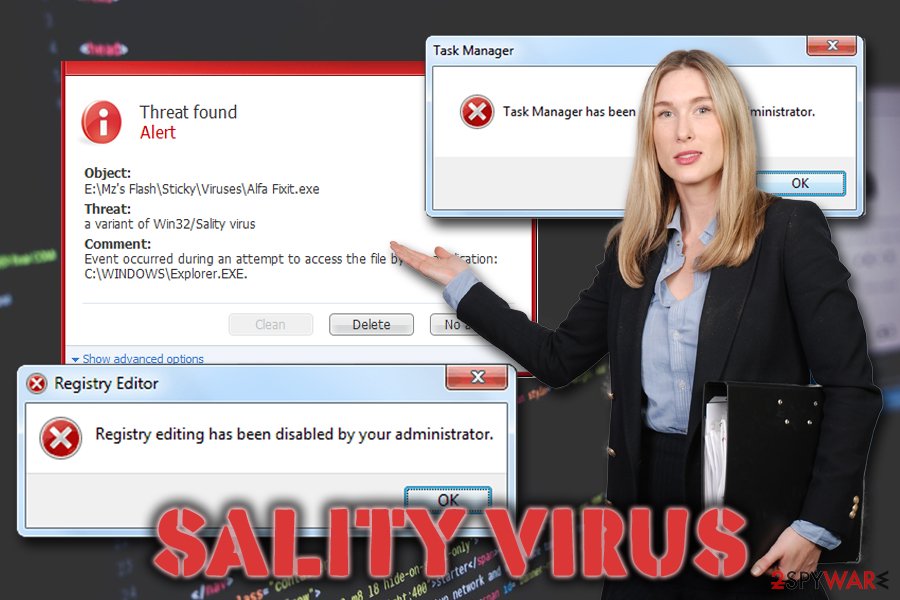
Computer infections via contaminated external drives and networks are still a huge risk
Users typically infect their computers with malicious software due to a lack of security measures. Some users are not aware of certain things that need to be done in order to protect themselves, while others simply neglect adequate security means and end up infecting their computers with dangerous malware.
One of the most important rules is to obtain reputable security software. While the Sality virus is old, security software developers implemented appropriate preventive measures to keep the malware away. However, you need to make sure that AV's database is continuously updated. Additionally, patching all the programs installed on the computer is vital as well. Software vulnerabilities are often used to infect malware automatically (that includes the operating system as well).
Finally, you should be aware that some files that look normal might be actually malicious. Therefore, you should never insert USB flash drives, SSD, or other external drives if you are not sure that they are safe to use. Unfortunately, you cannot be sure about that 100%, so you should let reputable anti-malware software to block such content before it manages to spread. Also, as a general rule, you should never open unknown files you download from the internet before you check them with tools like Virus Total (this includes pirated software, which is not recommended to download in the first place).
Sality virus removal steps
Sality virus removal is a complicated task, that is why preventing it is critical. Nevertheless, if you suspect that your computer is infected with this malware, you should perform several tasks to make sure that the cyber threat is gone.
There are different types of Sality viruses around. Therefore, in some cases, scanning your machine with robust security software will do the trick. Unfortunately, as we mentioned above, the malware typically stops the operation of multiple AV providers, and booting the system in Safe Mode might be impossible as well.
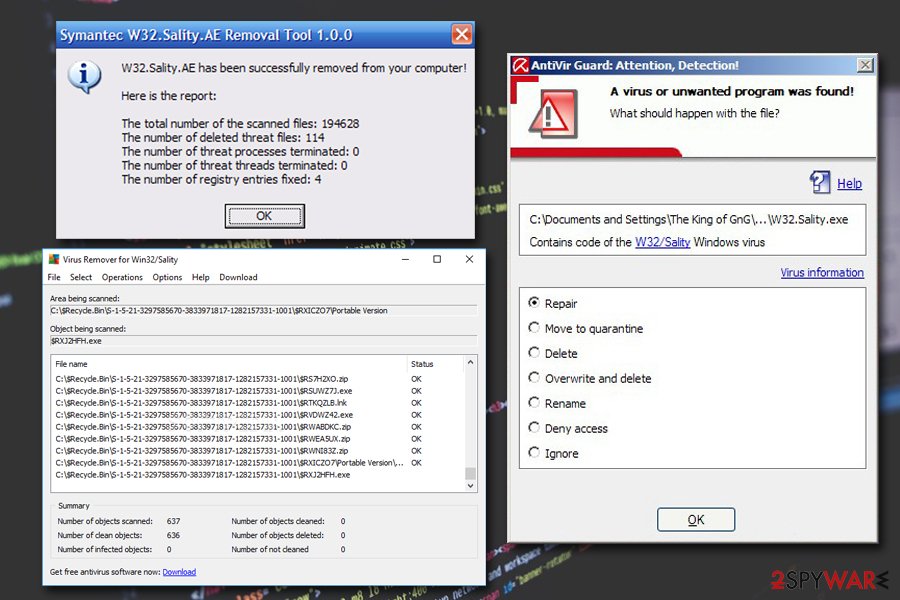
Some anti-virus vendors created tools that are specifically designed to remove Sality virus. AVG provides a Sality fix, and you can also make use of Kaspersky's Salitykiller. Once the malware is gone, you should make use of FortectIntego or SpyHunter 5Combo Cleaner to fix all the damage done to the machine – remember, the worm infects system files and anti-malware software typically can not repair the corrupted files. Therefore, use applications that can remediate your PC and restore Registry files.
Finally, security experts[5] do not recommend removing Sality manually, as the infection changes various parameters on the system. Thus, finding it and reverting the changes is an extremely complicated task that should only be practiced by trained IT specialists.
Getting rid of Sality virus. Follow these steps
Manual removal using Safe Mode
If Sality virus allows you to enter Safe Mode, proceed with the following:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Sality using System Restore
You can also try System Restore to get rid of malware:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Sality. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Sality and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Rootkits. Microsoft. Windows Defender Security Intelligence.
- ^ Margaret Rouse. Computer worm. SearchSecurity. Information Security information, news and tips.
- ^ What is Autorun and how to disable it?. Crystal Rich. Software developer.
- ^ Polymorphism (computer science). Wikipedia. The Free Encyclopedia.
- ^ VirusLer. VirusLer. Malware removal guides.







