SearchHDConverter browser hijacker (virus) - Chrome, Firefox, IE, Edge
SearchHDConverter browser hijacker Removal Guide
What is SearchHDConverter browser hijacker?
SearchHDConverter won't show you any useful links
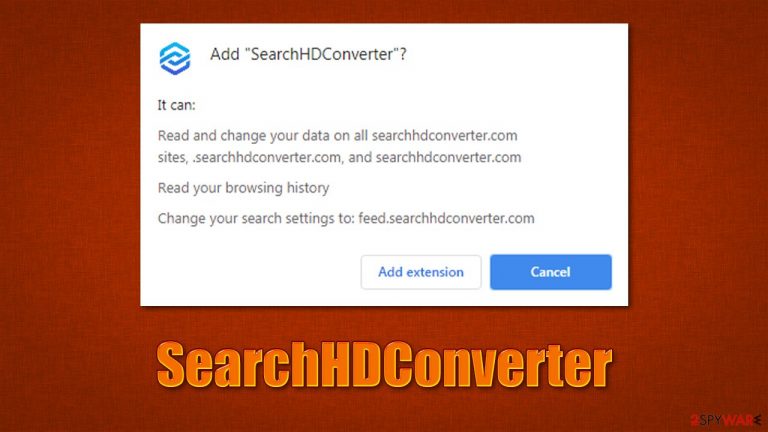
SearchHDConverter is a regular browser hijacker that most people install inadvertently, primarily because of deceptive distribution tactics. In some cases, people might install potentially unwanted apps themselves due to not being aware of their true purpose. And when it comes to browser hijackers, their usefulness is questionable at best.
Once installed, SearchHDConverter would immediately change the homepage URL and a new tab function, removing the previously used provider and using feed.searchhdconverter.com instead. It also uses a customized search that is allegedly meant to improve the web browsing experience somehow, although this is far from the truth.
In reality, all the searches performed while the hijacker is installed will no longer be forwarded through a default provider such as Google but rather something else. Typically the provider depends on the user's location. This alone can seriously compromise the web browsing experience as using a different search engine can be really inefficient and annoying to many.
However, the main issue with the hijacker is that it inserts sponsored links and ads at the top of the search results, which people are intuitively more inclined to click. This warrants that the promoted content is being visited by more people, increasing the revenue for all the parties involved. These links, in some cases, might be misleading and result in the installation of other potentially unwanted applications[1] or even malware, as well as privacy issues or monetary losses.
| Name | SearchHDConverter |
|---|---|
| Type | Browser hijacker, potentially unwanted program |
| Distribution | Software bundles, deceptive ads, fake updates |
| Symptoms | Unknown extension or application is installed on the system; homepage and new tab address are set to hijacker's one; a customized search engine is appended to the homepage; search results are filled with sponsored links and ads; “Managed by your organization” setting applied |
| Risks | You might be tricked into installing insecure software or pay for useless services; privacy issues might also arise due to information gathering practices |
| Removal | You can get rid of potentially unwanted programs manually, although performing a full system scan with SpyHunter 5Combo Cleaner or another security software can be much more efficient |
| Further steps | After getting rid of potentially unwanted programs, don't forget to clean your browsers accordingly – you can do it quickly and efficiently with FortectIntego |
The deceptive distribution methods
Potentially unwanted programs are called so for a reason – they have the “unwanted” word there because they are commonly installed unintentionally. This might be caused by one of the two reasons – freeware bundles downloaded on third-party websites or deceptive advertisements randomly encountered while browsing the web.
Bundled software is not something new. In fact, it has been around for many years and can be relatively useful for both parties -the developers and users. However, it is often implemented in an unfair way, especially by distributors that earn money from it. Various websites tend to compile several apps into a standalone package and deliberately hide optional components from users.
For that, they use various tricks, including pre-ticked boxes, fine print text, misleading button placements, and similar. Of course, all these tricks can be avoided by being more vigilant, which does not excuse such deceptive practices. Because the practice is widely accepted, you should be more careful when installing new software – never rush through steps, read the installation instructions carefully and, most importantly, always pick the Advanced/Custom installation mode when available.
It is worth noting that SearchHDConverter can also be advertised on various websites, which are reached after being redirected from a suspicious place. For example, clicking on links within torrents or similar websites can lead to insecure websites like that. In some cases, people might also be told that their computers are infected with a virus or that something needs to be updated – these messages should be ignored, as they commonly distribute malware.
Allegedly useful features
There are many ways users can customize their browsing experience by employing the functions of various applications and browser extensions. In fact, there are over 3.4 million apps in Google Play, 2.2 million in Apple's App Store,[2] and many more legitimate sources users can download from. The high number is understandable, considering how many people use the internet nowadays, and having a choice is always great.
Unfortunately, not all of the offered extensions or apps are useful. This is especially true when it comes to applications that are hosted on third-party websites, where a lot of the PUPs reside, as we explained already. There are plenty of browser hijackers that are presented as useful apps, and SearchHDConverter is no exception.
Judging by the name alone, it is meant to help people to convert files or videos in HD quality, although it does not possess such a function. The only “enhancement” it provides includes changes to the browser settings, redirects, and ads. While all of this benefits the developers, end-users get nothing worthwhile while being tracked by third parties.
To keep your browsing activities more secure and avoid being tracked online, you should remove the hijacker from your system. You can follow the steps below to uninstall the extension or do that automatically with SpyHunter 5Combo Cleaner or Malwarebytes security software. Besides, other PUPs or malware might be present on your device, so using anti-malware can help you eliminating everything malicious from your system at once. If malware is found, you should also repair any damaged system files with FortectIntego if required.
Get rid of SearchHDConverter
While some potentially unwanted applications can be installed on the system level, SearchHDConverter spreads as an extension for Google Chrome, Mozilla Firefox, or MS Edge. If you have already installed and uninstalled browser extensions, this process should not be difficult for you. If not, follow these steps:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Unfortunately, some users reported that SearchHDConverter also appended the “Managed by your organization” setting to the web browser, which can make its removal in a normal way almost impossible. If that is the case, we strongly recommend you stick to the automatic removal option as dealing with this might be quite complicated. You can refer to a separate guide if you would like.
Clean your browsers
Since most browser hijackers operate within the browser environment, they leave plenty of traces behind, even after they are removed. In general, security experts[3] advise cleaning web browser caches and cookies from time to time to avoid errors, crashes, and reduce the risk of privacy issues.
We strongly recommend you do that automatically with a FortectIntego PC repair and maintenance utility, although you can also follow the steps we provide below.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Chris Hoffman. PUPs Explained: What is a “Potentially Unwanted Program”?. How-To Geek. Site that explains technology.
- ^ Number of apps available in leading app stores as of 1st quarter 2021. Statista. Statistics portal.
- ^ Dieviren. Dieviren. Cybersecurity advice and malware insights.
