Smilebox Tab browser hijacker (Free Guide) - Chrome, Firefox, IE, Edge
Smilebox Tab browser hijacker Removal Guide
What is Smilebox Tab browser hijacker?
Smilebox Tab is a browser hijacker that changes the settings of your search preferences: it may impact your browsing in a negative way

Smilebox Tab is a potentially unwanted browser extension you may one day find on Chrome, Edge, Firefox, or another used browser. The presence of the app manifests as an altered homepage and new tab settings – this trait is likely what causes people to wonder what happened to their browsers all of a sudden, as smilebox.co is suddenly used as the start page URL.
Users are often unaware of where this app came from, as they don't remember installing it. This is because potentially unwanted programs are often distributed in freeware bundles or other deceptive methods, making a perfect opportunity for stealthy infiltration. Nonetheless, most PUPs are installed by users themselves, whether intentionally or not.
Smilebox Tab would bring in more ads than usual – they could be found on top of the search results every time the browser is used to search the web. Likewise, the generated results would be that of Yahoo or another provider, which may negatively impact how users find and look for information online.
| Name | Smilebox Tab |
| Type | Browser hijacker, potentially unwanted application |
| Distribution | Bundled software, third-party websites, misleading ads |
| Symptoms | The extension takes over your homepage and new tab address, placing promotional links as the top search results. It also displays intrusive ads on various websites you visit |
| Risks | Installation of other potentially unwanted programs/malware, personal data disclosure to unknown parties, monetary loss |
| Removal | To remove the unwanted browser extension, you should access your browser's settings. Checking the system with SpyHunter 5Combo Cleaner security software can also ensure that there is no adware or malware running in the background |
| Other tips | We recommend scanning the system with PC repair and maintenance utility FortectIntego to remove leftover files and ensure that trackers are eliminated from the browser |
Distribution of browser hijackers and how to avoid them
Often, users are surprised to find their homepage and new tab settings different from normal after unintentionally installing a potentially unwanted browser extension. This occurs when people install freeware from unreliable sources and agree to set up optional components without realizing it.
Commonly, important installation steps are often skipped by users due to them wanting to be done with the entire process quicker, so they press “Next” several times without reading what they agree to. Likewise, using “Recommended” or “Quick” settings is another common mistake that users make, as these allow the installer to implement apps automatically. When Selecting “Advanced” more, one could be much more in control of what is actually being installed on the system.
In other cases, users may install a potentially unwanted application after being tricked by a fake advertisement or a fake update. These often imply that something is missing from the computer and must be installed for various reasons (for example, a claim that viruses have been found). Ignore these requests and always refer to the official websites of the software whenever you see a suspicious claim.

Browser hijackers are not malicious, although they have plenty of unwanted traits
Although browser hijackers[1] are unlikely to infect your computer with malware, the top-of-the-page adverts might contain ads for potentially unwanted programs. Therefore, if a PUP is present on your computer, you can see adverts for other browser hijackers or adware.
Not only is Smilebox Tab highly invasive with its ads, but it also has the ability to monitor your data. This can include anything from search queries and visited websites to clicked links and technical device information. While this may not be a huge concern for some people, others may want to avoid using this type of software due to privacy issues.
Besides, brought-in changes can't be stopped unless the extension is removed or disabled via browser settings. We recommend uninstalling the app completely because there are little to no benefits to using it.
How to remove Smilebox Tab and check the system for other infections
Browser extensions are the most prevalent class of potentially unwanted applications. The extension is easy to create, update, and has the capacity to send advertisements to people who have it installed effectively. Therefore, you must open browser settings and take action in order to remove the browser hijacker.
Before proceeding, we recommend scanning the system with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful anti-malware software to ensure that there are no other potentially unwanted or malicious applications running in the background. Note that a robust security tool can also prevent attacks of dangerous malware, such as ransomware.[2]
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

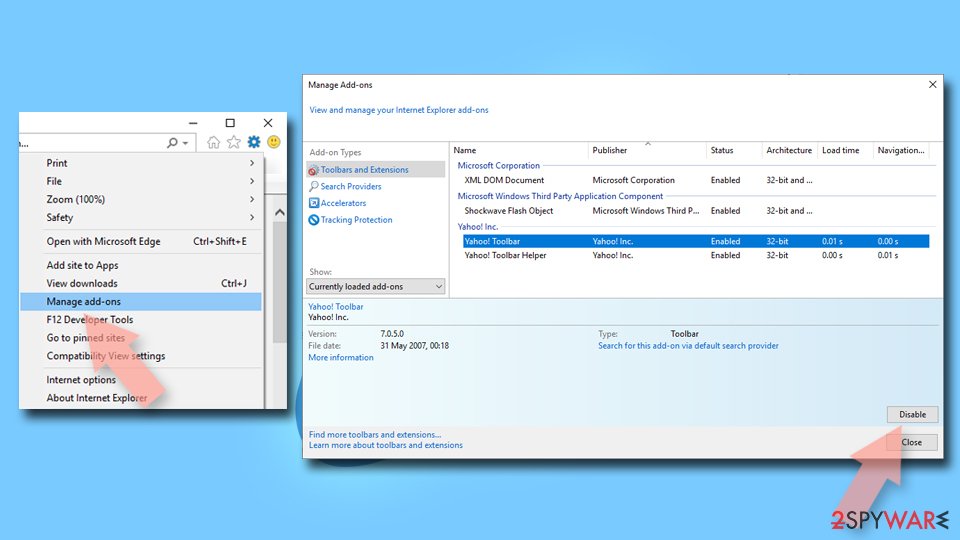
Internet Explorer
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
As was already stated, browser hijackers are well recognized for their ways of gathering data, which they use to share that data with other parties in order to generate more revenue. To achieve this, the program's developers set up a number of trackers on users' computers; these trackers continue to run even when the extension is removed. You should make sure to clear your system of cookies[3] and other site data as a result. You can either automate this using FortectIntego or do it by hand by following the instructions below:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

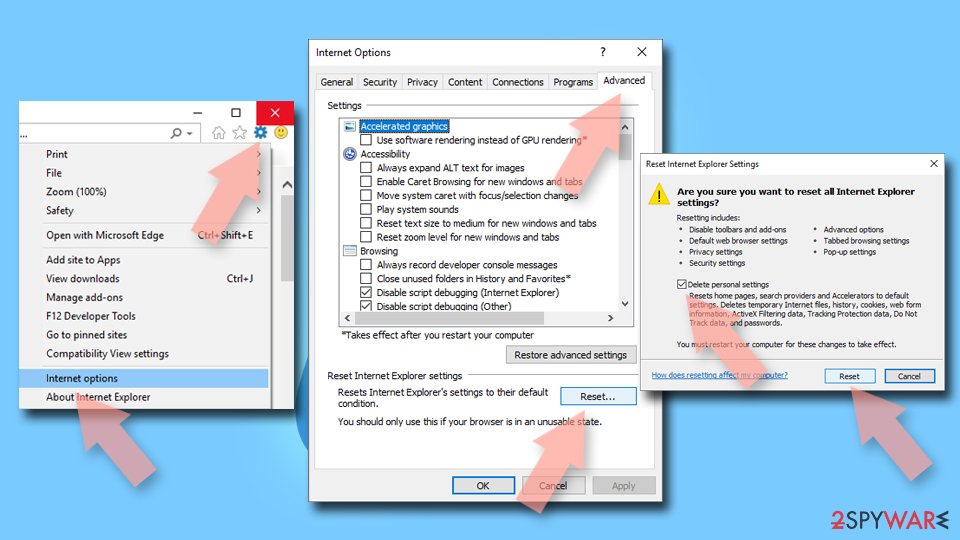
Internet Explorer
- Click on the Gear icon > Internet options and select the Advanced tab.
- Select Reset.
- In the new window, check Delete personal settings and select Reset.
How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Browser hijacking. Wikipedia. The free encyclopedia.
- ^ Ransomware. Imperva. Application and data protection.
- ^ What are cookies? | Cookies definition. Cloudflare. The Web Performance & Security Company.
