This Build of Windows 7 is Corrupted (Microsoft Support Scam) - Easy Removal Guide
This Build of Windows 7 is Corrupted Removal Guide
What is This Build of Windows 7 is Corrupted?
This Build of Windows 7 Is Corrupted is a fake alert that mimics official Microsoft's warning
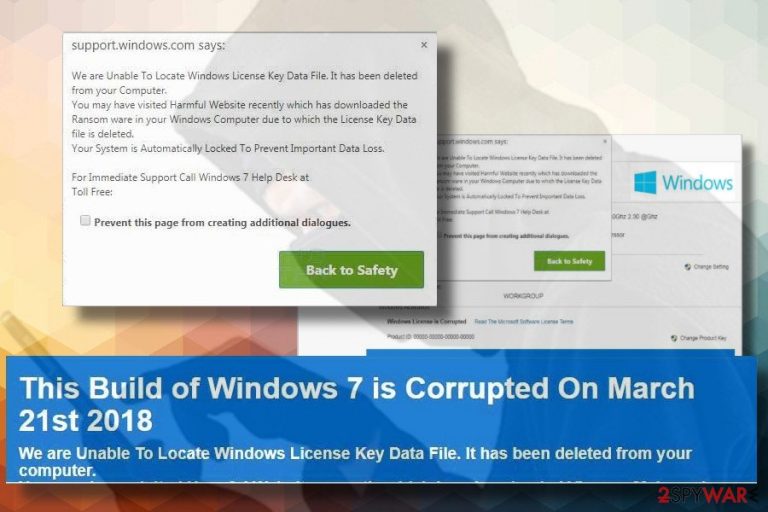
This Build of Windows 7 Is Corrupted is a hoax that falls into the categories of potentially unwanted program (PUP) and Tech-Support-Scam.[1] Typically it's triggered by recently installed adware, though hacked websites infected with cryptocurrency miners[2] might also cause it. The scam intimidates potential victims that the system has recently been infected with ransomware which encrypted the Windows License Key Data File. That's a catch to trick people into calling “certified Windows technicians” on “toll-free” number.
| Name | This Build of Windows 7 Is Corrupted |
| Type of malware | Technical Support Scam, PUP |
| Distribution | Bundling, spam emails with “unsubscribe” links |
| Symptoms | Web browser starts displaying This Build of Windows 7 Is Corrupted full page alerts that freeze the screen and urge to call supposed Windows support |
| Targeted web browser | Google Chrome, Mozilla Firefox, Internet Explorer, Microsoft Edge, Opera |
| Compatible OS | Windows 7 oriented, but altered versions can emerge on Windows 8, 8.1, and 10 |
| Actions required | Download FortectIntego and run a scan with it to eliminate malware. Reset web browser to disable This Build of Windows 7 Is Corrupted extension |
This Build of Windows 7 Is Corrupted will hardly earn the profit by attacking experienced PC users. However, less tech-savvy people might easily fall for believing that this pop-up is a genuine Windows Support Alert. At first glance, it does look legitimate. It contains Microsoft's logo, while the background exhibits similar design of Windows 7 Control Panel.
However, Windows License Key Data File corruption is an invented issue here. To scare people into thinking that the problem is real, crooks lock web browser's screen with this tech support scam and do not allow to close it normally. If the potential victim clicks the X button, the following pop-up window may appear:
The server license-key13.xyz is asking for your username and password. The server reports that it is from Windows 10.0.
Your Windows 10.0 License Has Been Corrupted. Enter User Name and Password Or Contact Windows 10.0 Help Desk at Toll-Free 1 (855) 622-0255.
Warning: Your username and password will be sent using basic authentication on a connection that isn't secure.
Do not fall for this trick because criminals will try to swindle your money. According to people's reports, the pretend-to-be Microsoft support member requires paying $200 for Windows License Key Data File recovery and the removal of supposed ransomware. Besides, crooks may also ask for your PC's records and your credentials to connect to your PC remotely.
Instead of communicating with tricksters, you should remove This Build of Windows 7 Is Corrupted scam from the system. Otherwise, this misleading pop-up alert will keep locking your web browser's screen on a regular basis.
This Build of Windows 7 Is Corrupted removal is also recommended to prevent third-parties from reading user's search data. The adware related to this scam can inject tracking cookies and web beacons to monitor people's web browsing activities and accumulate information needed for affiliate marketing.
You can remove This Build of Windows 7 Is Corrupted scam in two ways – manual and automatic. Since it may be difficult to identify the exact application that is triggering this fake warning, we recommend initiating a scan with FortectIntego to save your time and ensure proper malware elimination procedure.
Scam alerts can spread in many ways
Technical Support Scam Alerts can occur on the system out of nowhere. Crooks might inject malicious JavaScript codes to both legit and fake websites. Consequently, if the potential victim accidentally lands on a website, such as license-key13.xyz, he or she is very likely to receive a scam alert.
However, most frequently, people are tricked into installing the malware in the form of web browser's extension along with freeware. To prevent bundled installers, you must unpack each free application before installing it. For this purpose, opt for Advanced/Custom installation option and remove ticks marked next to extras like add-ons, plug-ins, toolbars, etc.
Cybersecurity researchers from udenvirus.dk[3] add that this particular malware can be distributed via spam email messages that contain links to unsubscribe unwanted email messages. Be aware that it's a trick and instead of unsubscribing some news you'll allow installing malware.
Get rid of This Build of Windows 7 Is Corrupted hoax
This Build of Windows 7 Is Corrupted removal is not as complicated as it might seem. The intrusive pop-up is dependent on adware type program, so to stop it from emerging in Chrom, Firefox or any other web browser, you have to remove This Build of Windows 7 Is Corrupted adware.
The problem is that it's currently unknown what particular apps are related to this scam. To avoid in-depth analysis of your system's tools, rely on a professional malware removal tool, say FortectIntego. It will eliminate PUPs and their components from system file, Windows registries, cache files, and similar.
Those who prefer manual This Build of Windows 7 Is Corrupted virus removal can use the tutorial provided below. Keep in mind that PUP removal is not the end of the task. You should also reset the web browser that keeps displaying the This Build of Windows 7 Is Corrupted pop-up.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of This Build of Windows 7 is Corrupted. Follow these steps
Uninstall from Windows
The following guide may be helpful to clean the web browser from intrusive technical support alerts. Make sure to check the list of installed apps and remove unknown or suspicious programs the install date of which coincide with the emergence of This Build of Windows 7 is Corrupted scam.
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
Google Chrome settings can be restored by following these steps:
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of This Build of Windows 7 is Corrupted registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting malware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Andy O'Donnell. How to Spot a Tech Support Scam. Lifewire.Tech related tips and tricks.
- ^ Thousands of websites infected by 'cryptocurrency mining' malware. The Strain Times. SPH Digital News.
- ^ Udenvirus. Udenvirus. Cyber security news oriented to Danish-speaking PC users.
