TRAPGET ransomware (Free Instructions) - Decryption Steps Included
TRAPGET virus Removal Guide
What is TRAPGET ransomware?
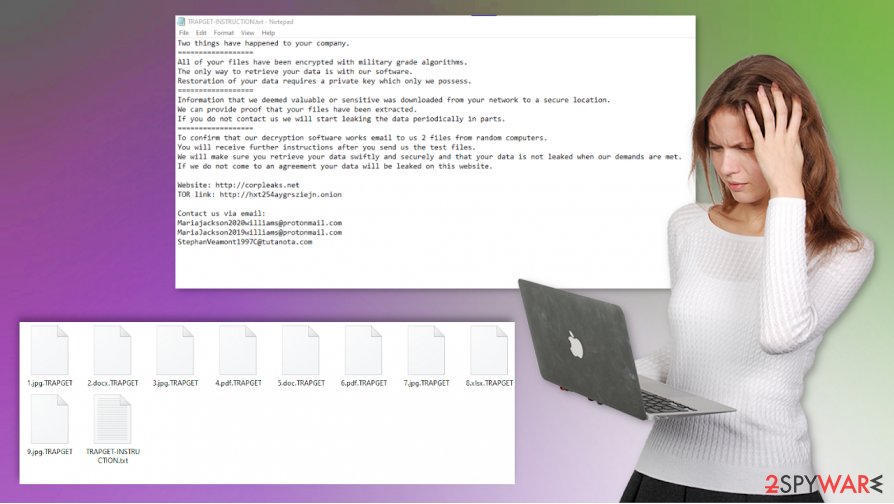
TRAPGET ransomware – cryptovirus that is designed to encrypt files and deliver TRAPGET-INSTRUCTION.txt file to inform victims
This TRAPGET ransomware virus steals valuable files and stores various documents or different information in a separate place, so claims about publications of these files can be made. It is a technique used to make people more eager to pay up in the given time to save their sensitive information and encoded files. The best solution to such infection is removal procedures. There are no experts that would recommend paying the ransom as the best option. You might lose your files permanently and suffer money losses if you pay these criminals. In most cases, decryption tools are not developed yet, and the test decryption is a trick. Criminals just sent you saved copies of some files to claim that this is how the decryptor works.
| Name | TRAPGET ransomware |
|---|---|
| Malware family | Nefilim ransomware is the initial version that TRAPGET virus is based on |
| File extension | .TRAPGET gets placed on every file that receives alterations with the encryption algorithm |
| Ransom note | TRAPGET-INSTRUCTION.txt – a file that contains particular instructions encouraging to pay up |
| Contact | mariajackson2020williams@protonmail.com, mariajackson2019williams@protonmail.com, stephanveamont1997C@tutanota.com |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Distribution | The threat can spread around using malicious links injected on various platforms, spam emails directly, or infect machines by attaching malware-laced documents as files on misleading emails from allegedly legitimate companies |
| Elimination | Perform a full system scan with powerful security software to remove TRAPGET ransomware |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with a PC repair tool or system optimizer like FortectIntego |
TRAPGET ransomware is the virus that aims to extort money from victims by encrypting data. The virus penetrates the targeted system and unnoticed can work for a while. The only symptom that is possible slowness of the machine due to processes running in the back. Unfortunately, until the encryption procedures get done, ransomware is not providing any indications about the happening infection.
Once those files that are commonly used and valuable get locked and encrypted, TRAPGET ransomware delivers a ransom-demanding message on the screen, places the particular file in various folders with affected data. This is the way criminals try to inform victims and encourage them to pay up.
The money-demanding message that TRAPGET ransomware creators compose states the following:
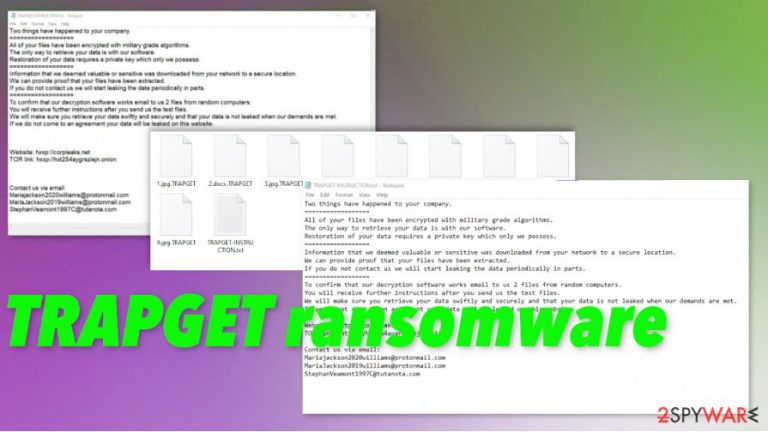
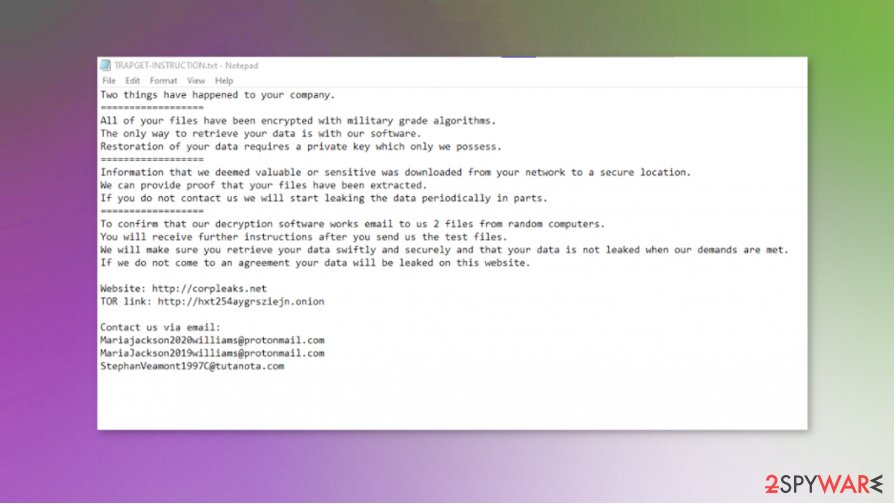
Two things have happened to your company.
==================
All of your files have been encrypted with military grade algorithms.
The only way to retrieve your data is with our software.
Restoration of your data requires a private key which only we possess.
==================
Information that we deemed valuable or sensitive was downloaded from your network to a secure location.
We can provide proof that your files have been extracted.
If you do not contact us we will start leaking the data periodically in parts.
==================
To confirm that our decryption software works email to us 2 files from random computers.
You will receive further instructions after you send us the test files.
We will make sure you retrieve your data swiftly and securely and that your data is not leaked when our demands are met.
If we do not come to an agreement your data will be leaked on this website.
Website: hxxp://corpleaks.net
TOR link: hxxp://hxt254aygrsziejn.onion
Contact us via email:
Mariajackson2020williams@protonmail.com
MariaJackson2019williams@protonmail.com
StephanVeamont1997C@tutanota.com
This message is scary and can be convincing enough so victims decide to pay. However, TRAPGET ransomware removal is not starting with paying these hackers. You should ignore these claims, don't panic, and try to get rid of the threat properly with tools like SpyHunter 5Combo Cleaner or Malwarebytes that can find intruders and remove them from the computer.
It is not worth it to pay the ransom asked by TRAPGET files virus creators. You should take the infection rate and detection numbers[3] into consideration and try to remove it properly instead. The worst thing that can happen is the loss of money and data when you believe those claims about decryption.
There are no particular ransom amount statements but in most of the cases, threat actors that create such campaigns tend to ask for hundreds of dollars in the form of Bitcoin or another cryptocurrency. This amount can go up to thousands even, so you should remove TRAPGET ransomware instead and do not consider paying as the solution.
TRAPGET ransomware is damaging, so the sooner you remove it from your device, the better. There are many parts of the system that can get affected and altered to ensure the persistence of this intruder. When malware manages to change settings or alter/damage files in parts of the system, folders, Windows registry, your machine can get more affected by other threats. It is especially important when your files are in question. Repair virus damage with system tools like FortectIntego and then focus on restoring encrypted data.
Malware distribution relying on malicious files and websites
There are many ways that hackers can spread their products. Criminals rely on methods that allow them to scare people, manipulate into doing what the attacker needs. This is how malicious actors can achieve a higher rate of infections – by spreading malware all over the world.
The most common way of delivering ransomware-type infections is the spam email method. When email notifications get sent to various people all over the world, misleading headlines, subject-lines claim about typical issues like orders, invoices, so people open those notifications without thinking twice.
Unfortunately, these emails have either malicious links or files directly attached to the email. These Microsoft documents, PDFs, images, or executables have macro viruses or other scripts that trigger the direct drop of malicious payload on the system. You need to keep paying attention to such details like senders and file-types when you receive such notifications.
Removing TRAPGET ransomware virus is important before you can rely on file-recovery options
The proper TRAPGET ransomware removal process can change the performance of the previously infected machine because the main intruder can trigger various additional infections and damage parts of the system that control crucial functions and programs or security tools.
Since TRAPGET ransomware virus can control how particular security or antivirus programs work, you should reboot the machine in Safe Mode with Networking and then launch SpyHunter 5Combo Cleaner or Malwarebytes, or another tool that you can trust. This program selection step is crucial because not every AV detection engine can find and terminate this threat.
However, you can remove TRAPGET ransomware on your own when you choose a proper program for the job. Do not forget that databases differ for these programs, so detection rates can change. As for the file recovery, do not fall for false claims from third-party program promoters and rely on official sources that provide data recovery applications. Before continuing to work on the machine – run FortectIntego to find or even fix system issues.
Getting rid of TRAPGET virus. Follow these steps
Manual removal using Safe Mode
Reboot the machine in Safe Mode with Networking and then run the AV tool that can remove TRAPGET ransomware
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove TRAPGET using System Restore
System Restore feature can ensure that your device is ransomware-free when you recover the machine in a previous state before the infection
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of TRAPGET. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove TRAPGET from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by TRAPGET, you can use several methods to restore them:
Data Recovery Pro is the program that can restore files after infections like TRAPGET ransomware virus
The program can restore files after encryption or even deleted documents, images, other data
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by TRAPGET ransomware;
- Restore them.
Windows Previous Versions – a feature that gets used as an alternate method for data recovery
When the System Restore feature gets enabled, you can rely on Windows Previous Versions and repair individual files
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer – method recovering data after encryption procedures
When TRAPGET ransomware leaves Shadow Volume Copies untouched, you can rely on this feature and recover the affected data yourself
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption options are limited when there is no TRAPGET ransomware decryption tool in particular
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from TRAPGET and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Cryptocurrency. Wikipedia. The free encyclopedia.
- ^ Scammers favor malicious URLs over attachments in email phishing attacks. Thenextweb. Security news.
- ^ Detection rate of the ransomware. VirusTotal. Online malware scanner.







