TrustedInstaller - updated Jan 2021
TrustedInstaller Removal Guide
What is TrustedInstaller?
TrustedInstaller is original Windows process, but is often abused by malware
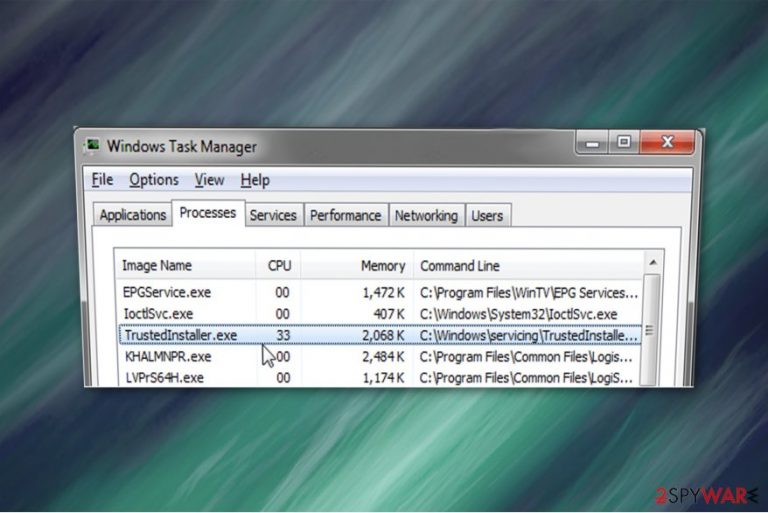
TrustedInstaller is a legitimate Windows process and is a part of Windows Resource Protection (WRP) technology. It runs under Windows Module Installer service, which is responsible for protecting unauthorized changes being made to .exe, .sys, .dll and other important files. For that reason, users cannot delete or modify certain files, even with Administrator's rights.
Nevertheless, TrustedInstaller, or TrustedInstaller.exe, is often abused by cybercriminals due to its functionality. It can be hijacked, replaced, or corrupted by malware, which can render the computer vulnerable to other severe infections and also compromise its operation by slowing down and crashing installed software. Besides, information tracking by recording keystrokes[1] or taking screenshots is likely as well.
In other cases, users are facing an issue with the process, as it prevents them from opening regular files, such as pictures or video clips. While it can also be malware's doing, it can be a simple bug. TrustedInstaller permission to modify files may be acquired by gaining ownership of them – we explain how to do that at the bottom of the article. Nevertheless, if you are having any type of problems with the file (like a high CPU usage), it is crucial to make sure it is not affected by a computer virus.
| Summary | |
| Name | TrustedInstaller |
| Type | Malware |
| Executable | TrustedInstaller.exe |
| Damage potential | Medium. Especially dangerous if not detected early |
| Distribution | Infected or hacked websites, malicious attachments, spam emails, etc. |
| Symptoms | High CPU usage, slowdown of the OS operation, crashes |
| Elimination | Use security software like SpyHunter 5Combo Cleaner or Malwarebytes |
| System fix | Malware may sometimes damage Windows system files and the registry database, which can result in stability and other issues. To fix virus damage after malware removal, scan it with FortectIntego |
TrustedInstaller.exe is an inbuilt user account used for all versions of Windows (starting from Windows Vista). Users would not even notice its presence most of the time. However, if malware replaced the mentioned file, it can cause problems. Nevertheless, you might see the following message if you try to edit/delete/install/uninstall specific files or folders on your OS:
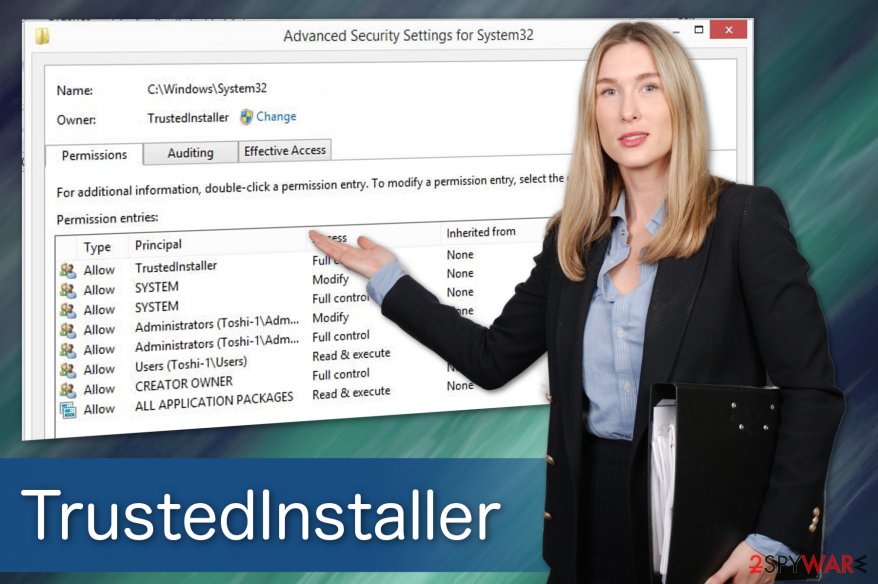
You Require Permission from TrustedInstaller
This happens because the built-in user account is in control of all your files and will overwrite your decisions. The primary goal of TrustedInstaller is to control user's ability to interact with the newest Windows updates, system files, and other essential programs. While it might be annoying sometimes, it is a useful feature for people without much computer knowledge, as it will prevent them from damaging system files.
The easiest way to identify if the running process is malicious program is by checking the CPU usage. If TrustedInstaller is using high amounts of your computer resources, it indicates that your system might be at risk. In spite of that, you might notice that your computer is significantly slower, it takes more time for programs to load or they continuously crash. Additionally, you should also check the location of TrustedInstaller, which should be located in C:\Windows\servicing\TrustedInstaller.exe.
Moreover, this dangerous TrustedInstaller malware can collect personally identifiable information, including:
- names;
- email addresses;
- home addresses;
- credentials[2].
Usually, it happens when the inexperienced computer user submits logins and passwords in the fake pop-up window. Additionally, be aware that TrustedInstaller virus might be able to let inside other dangerous cyber threats via backdoors. Likewise, to fix your computer, you will need to get rid of all of them. This procedure requires specific IT skills, and it might be challenging for a regular user.
Therefore, we suggest you remove TrustedInstaller virus right away if you do not want to suffer from financial losses. You can do that with the help of the instructions below. Be aware that the service is an important part of Windows if you delete or corrupt the original file you might damage the OS and the only way to repair it would be to reinstall it, resulting in personal data loss.
While you can start by checking CPU usage or the location of the file, the best way to make sure you perform Trustedinstaller removal on malware and not on legitimate file, you should install powerful anti-malware software and scan your system. The best environment for that would be Safe Mode[3] – the best place perform troubleshooting in.
After you terminate TrustedInstaller.exe virus, you should also scan your device with FortectIntego – it will fix Windows registry,[4] services, and other parts that were affected by malware.
Malware spreads via infected messages or hacker-controlled sites
According to DieViren.de[5] experts, a vast of malicious programs enter the computer systems via spam emails which contain the malware. They can disguise as the invoices or receipts from popular companies or even governmental authorities. Therefore, many gullible people are tricked to install the virus manually.
It might happen when you open the attachment in the spam email. Note that letter usually urges to open the added files for further information. Unfortunately, but the attachment downloads the malware once the person clicks on it. Likewise, you should never open emails which raise any suspicions.
Also, you can unconsciously download the malicious program from hacker-controlled sites. Typically, the user is redirected to such page by clicking on the malware-laden ad[6]. Since they are designed to look legitimate, it is hard to determine the origins. Therefore, it is one of the most popular ways to infiltrate malware.
We suggest you protect your system by avoiding any illegal downloads, advertising content and suspicious email letters. If you closely monitor your online activity and use a professional antivirus tool, you should be able to prevent malware from entering your system.
Take ownership of files controlled by TrustedInstaller
Warning: please be aware that TrustedInstaller account is there for a reason, and it prevents users and malicious actors from damaging important files that might corrupt the operation of Windows OS. Therefore, before you perform the following actions, make sure you do know what you are doing, as modifying system data might permanently corrupt it.
To gain Trustedinstaller permission, perform the following steps:
- Right-click on the folder you want to gain permission to and select Properties
- Select Security tab and click on Advanced
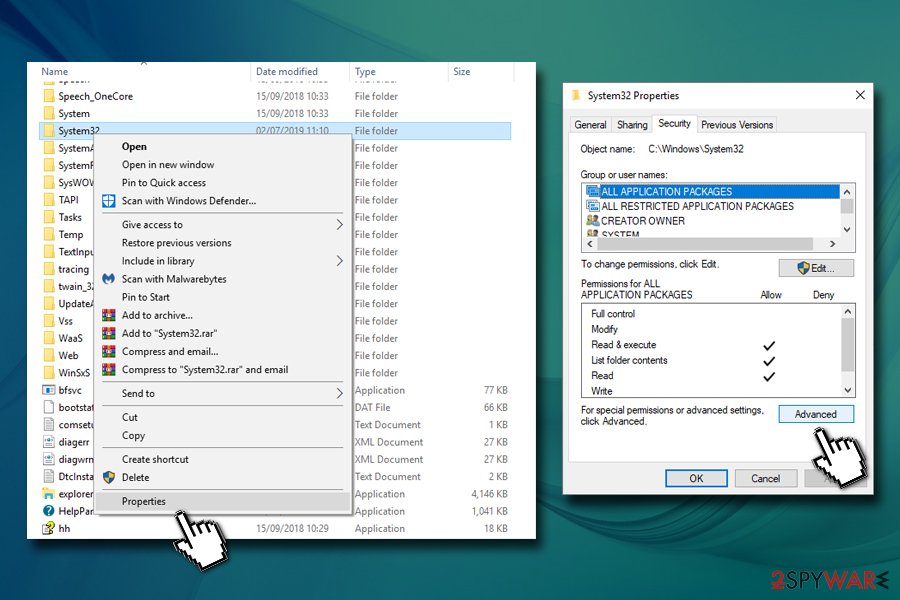
- In Advanced Security Settings, click Change next to the Owner
- Under Enter the object name to select, type in your username or Administrators and click on Check Names – Windows will fill in the name automatically
- Click OK
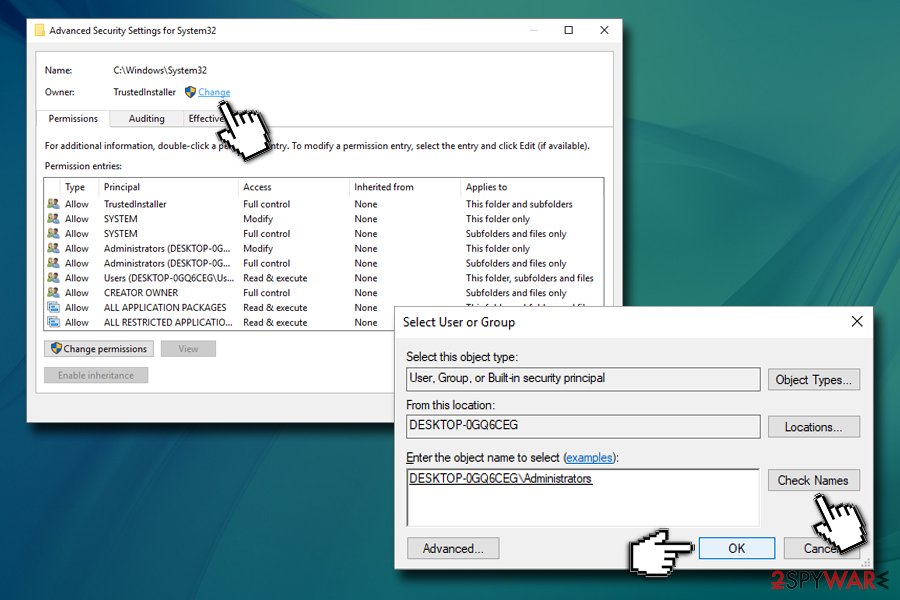
- Tick the Replace owner on subcontainers and objects box, and then click OK
- In the Properties window, select Edit
- Click on Administrators or Users (depending which option you chose previously)
- At the bottom of the window, make sure you tick Full control under Allow
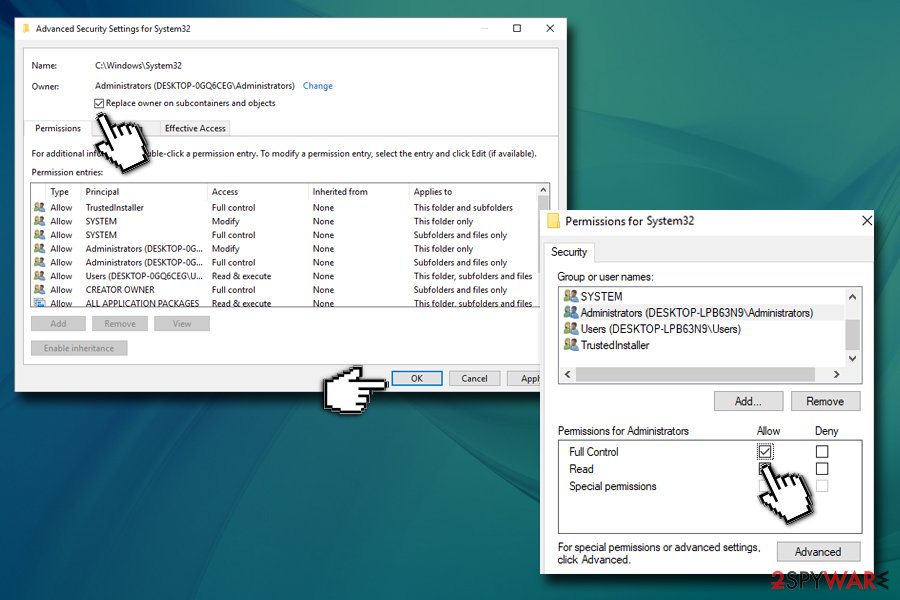
- Click Apply and then OK
After these actions, you should be able to overwrite Trustedinstaller's permission and be able to modify files under its control.
Remove TrustedInstaller virus automatically
We would like to warn you not to try to remove TrustedInstaller virus without any assistance. This malicious program is dangerous and might damage your computer permanently. However, you can use a powerful anti-malware software to eliminate the virus for you.
Download SpyHunter 5Combo Cleaner or Malwarebytes and run a full system scan. The security program will identify the malware together with other potentially dangerous computer threats and remove them. Note that this is the safest option you can choose to protect your system.
However, TrustedInstaller removal might require rebooting your computer into Safe Mode. If you are not aware of how to do that, make sure to check the instructions below.
Getting rid of TrustedInstaller. Follow these steps
Manual removal using Safe Mode
Firstly, you need to deactivate the malware since it might not allow you to install the security software. For that, reboot you computer to Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove TrustedInstaller using System Restore
If you are still unable to get the antivirus tool, try the System Restore method:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of TrustedInstaller. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from TrustedInstaller and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Mary Landesman. What Is a Keylogger Trojan?. Lifewire. Tech Untangled.
- ^ Margaret Rouse. personally identifiable information (PII). TechTarget. Computer Glossary, Computer Terms.
- ^ In Windows, what is Safe Mode used for and why?. How stuff works. Learn How Everything Works.
- ^ Gavin Phillips. What Is the Windows Registry and How Do I Edit It?. MakeUseOf. Technology, Simplified.
- ^ DieViren. DieViren. Security and Spyware News.
- ^ Malvertising. Wikipedia. The Free Encyclopedia.







