Tumblr virus 2019. 6 different versions revealed
Tumblr virus Removal Guide
What is Tumblr virus?
Tumblr virus is the cyber threat involving the legitimate social media platform in various scams and attacks
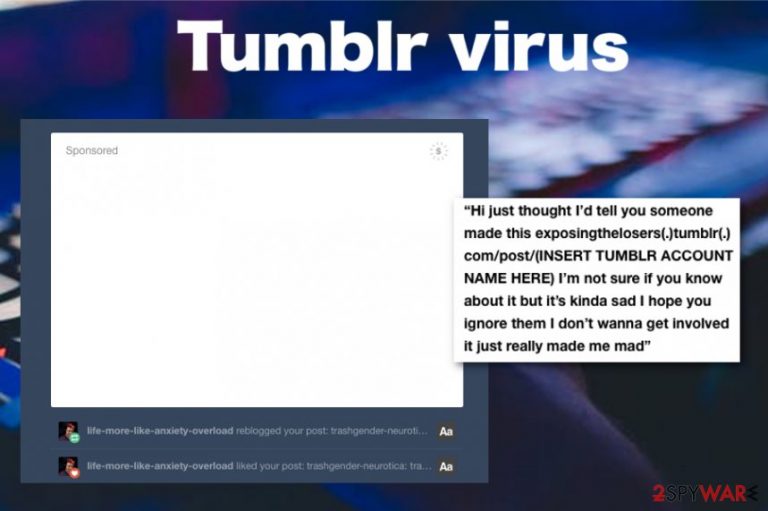
Tumblr virus is the type of malware affecting users who are using this service. This term has been used to describe various scams, pop-up redirects, and even more severe malware campaigns. Malicious actors are using different tactics, e.g. social engineering or even fake messages to swindle personal information to misuse it in further crimes. Since this network has millions of users from all over the world, and the platform is filled with various content, it is not hard to run into malicious or at least questionable link leading to the attack.
The more popular platform is, the more attractive for scammers it becomes. There are numerous types of Tumblr malware targeting separate accounts and aiming to steal personal information or infect the machine and gather details from the PC directly. In the article, we discuss all possible versions of Tumblr virus that can be delivered via the blogging platform.
| Name | Tumblr virus |
|---|---|
| Type | Malware/potentially unwanted program/scam/social engineering virus |
| tactics |
|
| Distribution | Emails, fake ads, malicious links, and redirects |
| Main danger | Can lead to the installation of suspicious programs, malware attacks, loss of personal details |
| Danger level | Can differ from low to especially high when it involves privacy issues, depends on the type of malware |
| Elimination | No matter the type, you need to get anti-malware tool to remove Tumblr virus |
Tumblr virus can include different campaigns because malicious actors typically aim for different goals. Aggressive phishing campaigns, saying that the account will be deactivated, target people who are actively using this platform for blogging. Scammers are either willing to steal users' credentials or even scare victims into paying a ransom. Unfortunately, such tactics work pretty well since people get scared.
Beware that Tumblr virus can also bring malware to the system. It is done with the help of spam misusing the name of this microblogging community. If you received an email asking you to download the attachment, you should scan it before downloading the file to the system because it can easily trigger the automatic installation of some rogue tool. These scams can even use compromised accounts to set up legitimate-looking pages and blogs.
You can run into Tumblr virus while visiting adult-related content, e.g. videos, or webpages with external malicious links. If you, out of nowhere, were asked to visit some Tumblr link to “see something interesting,” make sure you ignore this suggestion as there is almost 100 percent chance that you will be redirected to the dangerous site seeking to infect your system with Mac or Windows virus.
Finally, Tumblr virus can also be used for data tracking that involves gathering users' details about online activities and preferences, for example:
- computer's IP address
- PC's location
- victim's visited sites
- viewed content
- details revealed when visiting specific pages
As a result, people hiding behind Tumblr virus accumulate numerous amounts of sensitive information and sell it or use it in further crimes. They can easily set up personalized pop-up ads and banners, asking victims to take their part and win a specific prize or get some benefit in other way. However, this is how to whole malicious technique goes further and leads victims to malware.
Tumblr virus versions and possible tactics
Tumblr virus can be used by many different actors that aim to trick people into installing bogus software or visiting third-party pages. These are the more severe variants known to spread around:
Tumblr reblogging scam
Tumblr reblogging scams are using chain letter tactics.[1] In these scam campaigns, cybercriminals are expecting people to fall for the fake warning messages like “Your account will be deleted if you do not reblog this” or “Your account will be reactivated if you do not reblog”. These scams are typically spreading via emails and have become fairly common, in these cases.
Typically, such hoaxes redirect their victims to other pages, fake donation pages or foreign ad-supported websites where people can unwillingly get infected with unwanted programs or even malware. These particular scams can also target corporate accounts, so make sure you instruct your employees about this type of scams.
Bogus Tumblr accounts
Such Tumblr virus variant also is called sockpuppet attack because it involves malicious users hiding behind fake accounts targeting legitimate users. The purpose of such attacks is to make people follow bogus accounts back. Once the account gains followers, it can post gore pictures, chocking content, or material embedded with malicious links. This is not the content that you want to be exposed to, especially when the account you manage is a corporate blog.
Bogus Tumblr accounts are typically using random names, no avatar, and similar signs showing that something is wrong. In most cases, just pay attention to these red flags and avoid such accounts when they follow you. Just ignore them and wait until Tumblr team takes care of them.
Tumblr popup virus
Tumblr virus can also involve third-party content (usually, popups) delivered on the platform to redirect victims to questionable sites and sponsored pages. Third party campaigns typically include promotional content with “Tumblr IQ Test” messages or even fake links offering free updates, such as Flash Player update.
Profiles delivering such posts seem legitimate because they have avatars, normal-looking account names. However, once the link gets clicked, it typically redirects you to suspicious pages filled with promotional content, fake updates, and similar stuff. Do NOT click on these offers to prevent more serious malware on the system.
Tumblr scams misusing stolen/leaked information
The developers of Tumblr virus are also working on obtaining leaked data from breaches to misuse stolen email addresses and account credentials. Various vulnerabilities and bugs in such platforms can reveal personal data of users that is valuable when the criminal is expecting to use it in secondary scams.
Not so long ago we discussed the particular issue with Tumblr security and personal data[2] which is closely related to scams involving email notifications, messaging apps or even other social media. All the possible variants depend on stolen information since it can be an email address, the full name and other logins leading to serious issues.
Tumblr email virus
The more particular scam that can also involve stolen information affects people all over the world and aims to get personal details from victims with the purpose of getting their money or lead to identity theft. Email notifications claim to have your Tumblr account credentials and gathered pornographic or otherwise disturbing photos of you. Scammers claim to reveal such information if you restrain from paying them. In most cases, these people have one password of yours and aim to scare you by trying to guess that you use the same login info for more that one account. This is how criminals make people believe their claims.
Tumblr virus mobile version
Various users reported about such malware on their mobile devices when suspicious messages get sent from their accounts to other people.[3] It also involves messages about hacked account or pages not loading properly on the phone only. When your blog and account work normally on the PC, but issues appear on the mobile device, you can be sure that the particular machine has malware and your account is not hacked.

Tips to prevent Tumblr virus
You can avoid such infiltrations and those scary email scams if you pay closer attention to the content you visit and change your passwords to different and more complex ones. You can remove Tumblr virus no matter which campaign you got targeted by if you use professional anti-malware tools and clean the machine from malware automatically.
Tumblr virus removal process can be complicated if you are dealing with a few different versions or a more severe campaign. For that reason, we recommend rebooting the machine in the Safe Mode with Networking so your AV tool can gather all the malicious files and delete them. We also offer to scan the device with FortectIntego, so virus damage is cleaned entirely.
Many security experts[4] note that any social media malware can involve messages and campaigns on other platforms too target people via other channels. Tumblr virus can also send Facebook regarding messages or even scammer alerts like the FBI virus, as various people reported online.[5]
Virus delivery methods also depend on the developers' goal
In the cybersecurity world malicious files, infected sites, other online content can deliver different programs, or even allow the attacker to access your device remotely. When malware involves social media, blogging platforms, or other services, the main legitimate website is not the one that you get these malicious programs from. The main social network is safe to use, but content involved on the website can lead to infiltrations of cyber threats.
A few examples of how such a virus can be distributed:
- pop-up ads, banners, and redirects filled with malicious content;
- direct downloads from promotional content;
- software bundles;
- phishing emails or direct messages with hyperlinks, infected files.
The best tip you, as a social media user should take from this article is to create complex, long passwords for your accounts, choose different ones for all accounts, so there is no luck when malicious actors play the password guessing game. Keep anti-malware programs on your PC, so the tool can block PUPs and other malware before it enters the machine.
Get rid of the Tumblr virus with professional tools and clean your PC fully
You need to remove Tumblr virus no matter the particular type of malware that it is based on. The best tip we can give you as cybersecurity researchers – scan the machine thoroughly with an anti-malware program and clean the device by deleting any indicated threats or even system errors and issues.
Tumblr virus removal becomes difficult when malicious actors create a threat with the capability of changing registry entries, system preferences, adding programs or applications directly to the computer. For that purpose, we suggest rebooting the machine in the Safe Mode before cleaning the system with tools like FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes.
Getting rid of Tumblr virus. Follow these steps
Manual removal using Safe Mode
You can get the advantage of Safe Mode with Networking when removing Tumblr virus because AV engine can work properly in this mode without any virus interuption
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Tumblr using System Restore
When it is difficult to remove the Tumblr virus, you can rely on System Restore feature that can recover the device in a previous state before virus attack and damage
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Tumblr. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Tumblr and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Chain letter. Wikipedia. The free encyclopedia.
- ^ Julie Splinters. Bug in Tumblr possibly revealed personal users' data. 2spyware. Spyware related news.
- ^ iPhone with tumblr virus. Apple. Discussions community.
- ^ Bedynet. Bedynet. Spyware related news.
- ^ FBI virus/malware took over my computer via Tumblr photo I tried to open.. Norton. Community forum.







