Victorysweepstakes.com ads (scam) - Free Guide
Victorysweepstakes.com ads Removal Guide
What is Victorysweepstakes.com ads?
Victorysweepstakes.com shows fake lottery messages to make users provide their personal information
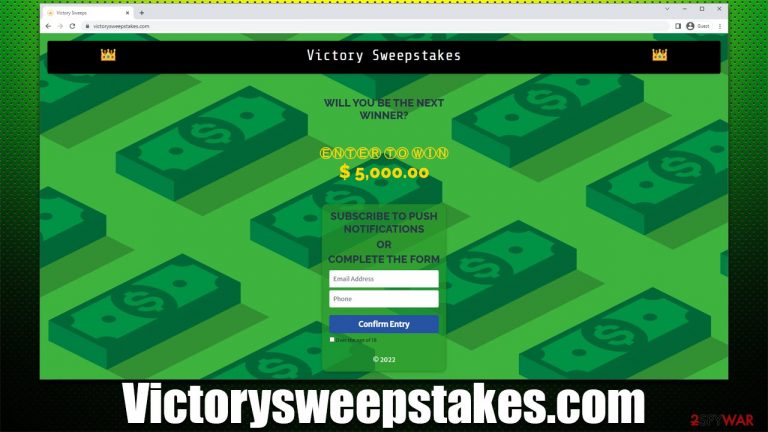
Victorysweepstakes.com is a scam website you might see when browsing the web on Google Chrome, Mozilla Firefox, MS Edge, or another web browser. The main goal of the scam is to fool users that they can win $5,000 by entering an alleged lottery – the only thing they have to do is disclose their phone and contact email.
In reality, there is no way to win anything on the site, as it is created by scammers. By entering your personal contact details into the Victorysweepstakes.com site, you provide this information directly to cybercriminals, who can later use it for various malicious purposes, such as follow-up phishing attempts via the said contact methods.
Victorysweepstakes.com also asks users to enable push notifications upon entry. This tactic is used in order to abuse the built-in API (Application Programming Interface)[1] so that commercial content would be shown to users later. In many cases, this results in even more spam and malicious ads being shown to people without a warning.
If you have encountered the scam website and wish to know what to do next, please read through the article below to ensure that your system is secure. We will also explain how to remove the unwanted push notifications from the system.
| Name | Victorysweepstakes.com |
| Type | Scam, phishing, redirect, adware |
| Operation | Promotes a fake lottery in order to make people provide their contact details – it can later be used for malicious purposes |
| Distribution | Redirects from other malicious websites, adware |
| Risks | Installation of PUPs or malware, sensitive information disclosure to malicious parties, financial losses |
| Removal | You should not interact with the contents shown by a scam website, check your system for adware or malware infections with SpyHunter 5Combo Cleaner security software |
| Other tips | Third parties can use cookies to continue tracking your online activities, so we recommended clearing browser caches and other leftover files with FortectIntego |
How scams spread
Malicious and dubious material online still exists despite the regulatory bodies trying to regulate the internet as much as possible. The truth is, the world wide web is simply too vast for it to be moderated fully, and malicious websites manage to stay active for some time before they are taken down in one way or another.
However, you are unlikely to encounter malicious ads or redirects when using legitimate search tools or entering websites directly. The unexpected redirects to malicious websites most commonly occur when visiting peer-to-peer networks,[2] YouTube video converters, software cracks, and similar places.
In order to avoid Victorysweepstakes.com redirects, you should stay away from the mentioned websites. Not only would you reduce the probability of being exposed to phishing material online, but you would also prevent the infiltration of dangerous malware, such as ransomware.[3] It is not a secret that Zfdv and other Djvu variants are spread via pirated software installers, and it remains one of the most successful malware strains out there.
I have entered my personal details. What to do now?
Unfortunately, nothing can be done to undo the disclosure of personal information. Once data is disclosed online, it is likely to prevail, and scammers behind Victorysweepstakes.com are likely to use it in malicious ways. For example, they might sell your phone number and email to advertisers so you would be constantly bothered by various offers.
In more sinister cases, scammers may sell the information on the underground forums – it can later be used to conduct targeted phishing attacks against you. This is why you should be prepared, as crooks may know a lot about you by now, and pretend to call on behalf of reputable institutions, claiming that some of your accounts have been terminated, or that you owe in tax payments.
Never trust these calls or emails. If in doubt, stop the communication immediately and then use the official contact number of the company or institution the unknown individual is claiming to be from. If there is a problem with your accounts or similar – it will be cleared up immediately.
Check your device for adware
Another problem you should tackle is adware infection. It is not a secret that those infected with adware are more likely to experience unexpected redirects, encounter more suspicious material online, and face ads everywhere they go.
The easiest way to check your system thoroughly is by performing a full system scan with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful anti-malware software. It can check all the third-party software and ensure that all suspicious and malicious components are eradicated immediately.
After that, we recommend you use the FortectIntego repair and maintenance utility to ensure that browser caches are cleared and system file damage is fixed. Otherwise, third parties could still track you undisturbed for a very long time. You can also clean browser caches manually if you prefer so:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

MS Edge
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Take care of unwanted push notifications
If you have enabled push notifications from Victorysweepstakes.com, you are likely to receive intrusive pop-ups regularly. These could promote dubious software, claim that your system is infected with viruses, or that you have won an expensive gift. These are all scams and you should not interact with the promoted links. Instead, you should block the website URL in the site settings section of your browser as explained below.
Google Chrome
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.

Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.

MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.

Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.

How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Application Programming Interface (API). IBM. Cloud Learn Hub.
- ^ Adam Hayes. Peer-to-Peer (P2P) Service. Investopedia. Source of financial content on the web.
- ^ Ransomware. Imperva. Application and data protection.
