Volume Extra adware (spam) - Free Guide
Volume Extra adware Removal Guide
What is Volume Extra adware?
Volume Extra is a fake browser extension created by crooks to make money
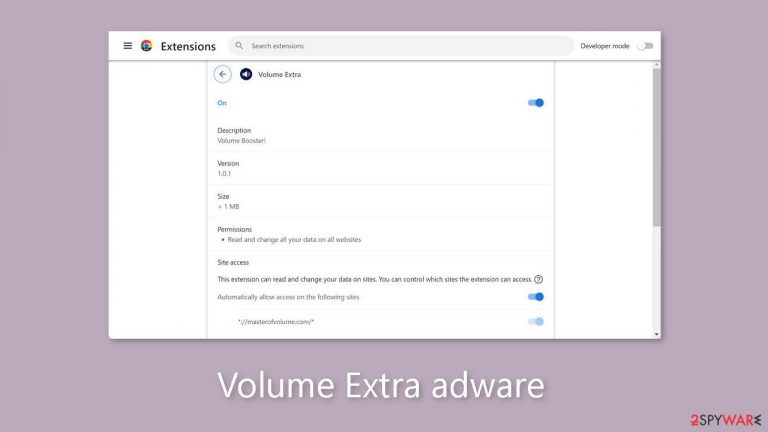
Volume Extra is marketed as a useful tool for increasing volume, but it is actually a deceptive browser extension that displays advertisements. This means that it has the potential to bombard users with a high volume of commercial content, such as pop-ups, banners, and redirects. Scammers use such applications to generate profits.
The claimed ability to increase volume has not been proven to be effective. Scammers primarily use these programs to generate passive income because they frequently fail to deliver the promised benefits. It is never a good idea to install unnecessary third-party applications on your computer.
Furthermore, the extension may be linked to rogue advertising networks that display advertisements that lead to dangerous websites. Users may unintentionally land on fraudulent pages designed to trick them into disclosing personal information, downloading potentially unwanted programs (PUPs),[1] or infecting their systems with malware.
| NAME | Volume Extra |
| TYPE | Adware |
| SYMPTOMS | Pop-ups and other types of advertisements begin to appear on the screen |
| DISTRIBUTION | Shady websites, deceptive ads, freeware installations |
| DANGERS | Links embedded in advertisements may lead to dangerous websites |
| ELIMINATION | Remove the extension through your browser settings; anti-malware software should be used to scan the machine. |
| FURTHER STEPS | To remove any remaining damage and optimize the machine, use FortectIntego |
Distribution methods
To protect yourself from criminals' deceptive tactics, it is critical to exercise caution when evaluating software programs marketed as “useful” tools. We strongly advise using official app stores as a reliable source. Applications listed on these platforms are thoroughly reviewed before they are made available to users. Nonetheless, before downloading an app, it is prudent to read reviews, consider ratings, and assess its popularity.
Scammers may even go so far as to create deceptive “official” promotional websites for their apps. Their goal is to make these websites appear very appealing, luring people to download the software themselves. It is critical to remember that if something appears to be too good to be true, it most likely is.
Fake downloader pages are also a source for harmful browser extensions. Random websites may prompt users to download a plugin in order to access the site's content. Such requests must never be complied with. Legitimate websites should never require visitors to download additional software in order to view them.
Protect your privacy
In today's world, nearly all web-based applications use cookies[2] to track user behavior. In general, this practice is not malicious because it helps to personalize the user experience. Cookies are small data files that can be used to store information such as websites visited, links clicked, and online purchases made.
However, it is critical to recognize that cookies can be used for profit by unscrupulous individuals. Without your permission, they may be sold to advertising networks and other third parties. To address this issue, we recommend using a trustworthy repair tool such as FortectIntego. This tool can clear your browser's cookies and cache, free up storage space, repair corrupted files and system errors, and optimize the performance of your device.
Remove Volume Extra adware
Volume Extra adware[3] can be removed by accessing the browser settings and checking the extension list. We recommend removing plugins one at a time to see if any changes occur.
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Potentially unwanted program. Wikipedia, the free encyclopedia.
- ^ Dusan Vasic. What Are Cookies? The Good and the Bad of Browser Cookies. Dataprot. Security Solutions.
- ^ Adware. Malwarebytes. Cybersecurity Basics.










