Wacatac Trojan (virus) - 2022 update
Wacatac Trojan Removal Guide
What is Wacatac Trojan?
Wacatac is malware triggering the alert that can informal about security issues but also appears when there are no threats at all
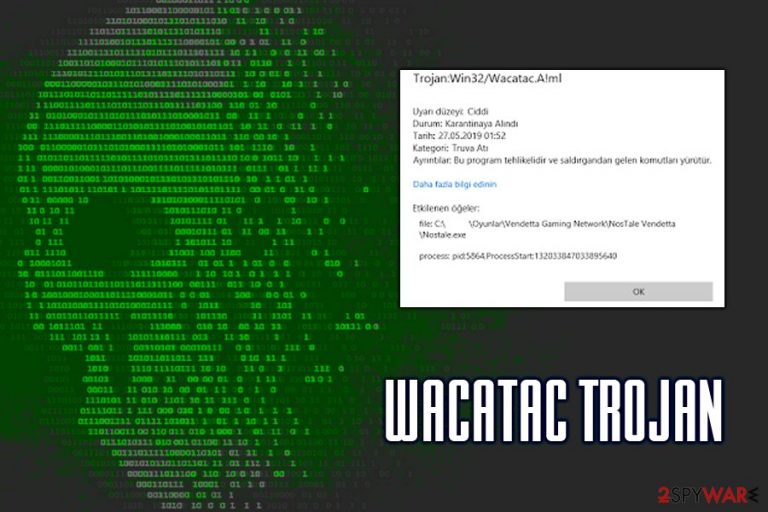
Wacatac Trojan is a threat that can affect the system significantly. Trojans diminish the security of the machine and can lead to more serious infections. This malware, once injected, performs a variety of system changes and starts its malicious activities immediately.
The detection of this malware is known as Trojan:Win32/Wacatac. The trojan enters machines primarily via the spam email attachments named “DHL Shipment Notification 3300777400-Delivery for 10 July 2019_pdf.gz”, or similar. Nevertheless, victims can also get infected when downloading pirated software or by visiting malicious sites that host drive-by downloads. Trojans easily spread around using malicious ages and deceiving links, and websites.
The particular malware is developed with various functionalities in mind and it can cause major issues, and lead to damage. The Wacatac trojan can collect details like passwords, usernames, banking details, and other personally identifiable information or data potentially used in later scams.
The Trojan seems to be spreading with a new wave in 2022 because multiple campaigns and samples got detected by researchers. It still shows chain infection functions and infiltrates machines to spread additional malware like ransomware or cryptocurrency miners.
You might not even see symptoms of the infection, but the Wacatac detection names appear on the screen when the computer detects questionable activities. It is better to react as soon as that happens and run anti-malware tools to clear any of the infections and terminate the intruder fully to avoid further damage on the machine.
Wacatac overview
This type of malware can be extremely dangerous – it can harvest personal information (login information, banking details, etc.) or proliferate other malware (ransomware, cryptominers, rootkits,[1] RATs, and other dangerous infections). The worst thing about its the fact that processes are silent and malware mainly works in the background. Additionally, the infected machines might be included in a botnet and help perform DDoS attacks against specific targets.
You need to thoroughly check the machine he the alert appears. It is possible that the detection is falsely positive, so you do not need t to eliminate any infection. Thus, check the article further, learn about potential symptoms, and make sure to clean the machine from any threats by running a trustworthy anti-malware program.
| Name | Wacatac |
| Type | Trojan, spyware |
| Related files | DHL Shipment Notification 3300777400-Delivery for 10 July 2019_pdf.gz, Unimpartial.exe |
| Related process | biddulphia9 |
| Infection means | Spam email attachments, although other methods can be used by hackers as well |
| Distribution | Typically reading using spam emails with malicious attachments or fake software and video game cracks |
| Risk factors | Infection of other malware, loss of money, identity theft |
| Symptoms | Rarely any. In some cases, users can experience high resource usage, program crashes, unknown processes running in the background |
| Termination | Employ reputable anti-malware software to see if there any real threats on the machine |
| Repair | If the trojan runs for a while it can affect performance, functions, and other serious system files, so run FortectIntego to find and fix the virus damage |
What Trojan.Script.Wacatac.B.ml detection means?
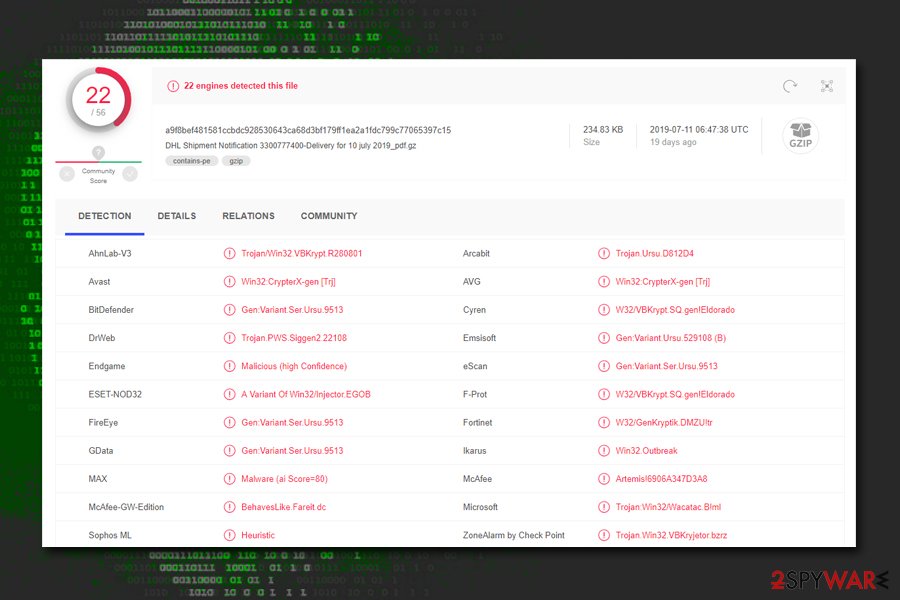
The detection of this trojan might also be a false positive,[2] as users reported that Microsoft Defender is also flagging legitimate installers like Thaiphoon Burner and Soulash video game. If that is the case, you should add an exclusion to the legitimate file; in the meantime, you should be extremely concerned if the detection is not a false positive – you should remove Wacatac Trojan as soon as possible.
So, how do you know if the virus-detection is verified and you are dealing with an actual trojan? The best way to check whether the detection is indeed a false positive is to upload it to sources like Virus Total. If the infection is real, you will be able to see detection from other vendors, such as:[3]
- Win32:CrypterX-gen [Trj]
- A Variant Of Win32/Injector.EGOB
- Artemis!6906A347D3A8
- Gen:Variant.Ursu.529108 (B)
- Gen:Variant.Ser.Ursu.9513
- Trojan.Win32.VBKryjetor.bzrz, etc.
Unfortunately, that is the only way you will know if you are infected with Wacatac Trojan. In most cases, real infection is programmed in a way that lets it hide its malicious activities in the background, meaning that infection symptoms are lacking.
What does the infection cause?
If the Trojan:Win32/Wacatac inserted other parasites, you will likely encounter frequent program crashes, slow operation of the device, BSoDs,[4] increased amount of advertisements when browsing, installed programs or files that you have never seen before, etc.
Unfortunately, the infection of any malware, including this trojan might result in severe consequences, including money loss, installation of other malware, corruption of credit score, or even identity theft/fraud. Silent pieces of infections often get used as vectors for additional malware.
Therefore, you should always make sure that your computer is virus-free by employing reputable anti-malware software with real-time protection features. Besides, you can also perform a full virus removal using security tools such as Malwarebytes, SpyHunter 5Combo Cleaner, or other reputable vendors.
The most common malware spreading methods – malicious email attachments
Malware authors are smart individuals who chose to use their skills for malicious purposes. Therefore, they usually employ a variety of sophisticated methods to deliver the malicious payload to thousands of users; for example, exploit kits, web injects, brute-force attacks, and other practices.
Nevertheless, possibly the most prominent malware delivery method is spam email attachments. From trojans to ransomware – the obfuscated files that are attached to phishing emails can deliver the nastiest viruses. In most cases, the message comes from a seemingly well-known company, such as DHL, Amazon, or Bank of America. Here's an example:
Track DHL Express Shipment
Dear Customer,
Your email address was found on package with unclear delivery address as per DHL policy, we will not fail to return the package if it remain unclaimed within the next 48 hours.
Kindly review the receipt and make necessary steps if the package belongs to you to avoid loss of property.
Please Click and Download attached receipt to review the package details.Best Regards,
DHL TEAM
Copyright 2019
As evident, the email is not coming from a real DHL shipment company. Nevertheless, it is easy to imagine how many people are actually awaiting a package by this carrier and could fall for the trick and download the malicious attachment.
Thus, never open suspicious spam email attachments; if you have doubts if the file is legitimate, you should always scan it with tools like Virus Total before opening it.
Check for virus detections and false positives before removing the Wacatac
Before you remove the trojan from your machine, you need to make sure that it is not a false positive. As we previously mentioned, you should scan the file with different security software or use tools like Virus Total. Once you are sure that it is actually malicious, you should proceed with its termination immediately.
While Wacatac Trojan removal can be performed manually, it can be hardly recommended for regular users. Trojans are serious infections that modify the Windows operating system, affecting its most vital parts. Therefore, you should instead use anti-malware software that would terminate the virus for you and also restore the normal system functions.
Be aware that the virus might interfere with security software or prevent its removal. If that is the case, you should access Safe Mode with Networking as we explain below. You should do that as soon as those alerts appear to avoid serious damage.
Getting rid of Wacatac Trojan. Follow these steps
Access Safe Mode to remove malware from Windows
If malware is not letting you use antivirus in normal mode, access Safe Mode and perform a full system scan from there.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

Once you reach Safe Mode, launch SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable antivirus, update it with the latest definitions, and perform a full system scan to eradicate malware and all its malicious components.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
How to prevent from getting trojans
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ How to remove remote administration tools. 2-spyware. Cybersecurity news and articles.
- ^ Pieter Arntz. Explained: False positives. Malwarebytes Labs. Security blog.
- ^ DHL Shipment Notification 3300777400-Delivery for 10 july 2019_pdf.gz. Virus Total. File and URL analyzer.
- ^ Blue Screen of Death. Wikipedia. The Free Encyclopedia.
