CryptoMix ransomware / virus (Virus Removal Instructions) - Apr 2020 update
CryptoMix virus Removal Guide
What is CryptoMix ransomware virus?
CryptoMix ransomware developers keep releasing new versions: Lesli the latest danger
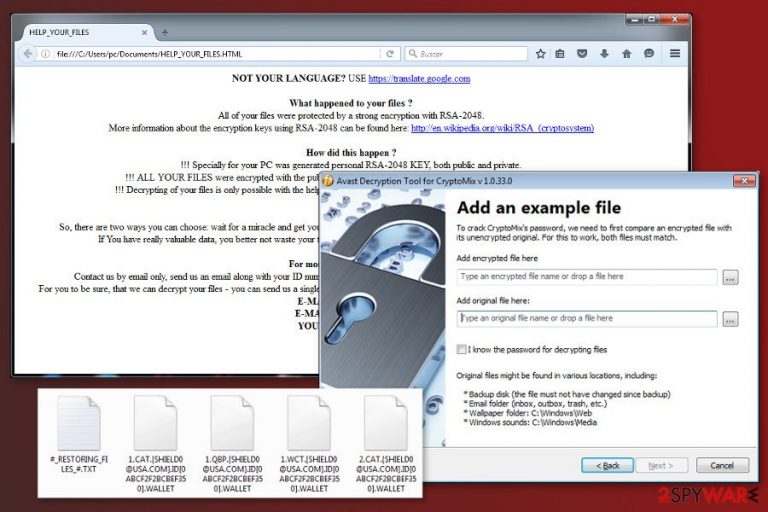
CryptoMix is a ransomware-type[1] computer infection that emerged in 2016. Throughout four years of existence, it has evolved and currently has a done of sub-categories. The latest CryptoMix ransomware variant is known as Lesli. Although different variants exhibit some distinctive features, such as file extensions or ransom notes, all of them render AES 256, RSA-2048 or ROT 13[2] encryption algorithms to lock non-system files, generate a Ransom.Cryptomix note and demand its victims to pay the ransom. The size of redemption that CryptoMix demands vary from $400 to $2000 in Bitcoin cryptocurrency.
The latest CryptoMix variant, known as Lesli ransomware has been spotted on the wild in April 2020. Victims reported on cybersecurity forum that their files were encrypted by .lesli file extension, which is also preceded by an email address supl0@post.com and a personal ID code, which differs in each case. The ransomware renders RSA-2048 cipher, which generates an “offline key” for each Lesli ransomware victim. Besides, it drops INSTRUCTION RESTORE FILE.TXT ransom note, which demands victims to send an email to sup10@post.com or sup10@iath.com emails within 72 hours.
Although each CryptoMix ransomware variant is extremely dangerous, white hats have already cracked some of them down and released a free decryption software. Available at Avast's official website[3], the software is said to be able to decrypt files encrypted by .lesli, .rdmk, .scl, .code, .rmd, .CRYPTOSHIELD, .rscl, and .MOLE variants.
| Name | CryptoMix |
|---|---|
| Type | Ransomware |
| Danger level | High |
| Versions | Exceeds 30 (the list provided below) |
| Distribution | Malicious email attachments, rogue software updates, exploit kits, malvertising |
| Detected in | 2016 (still active) |
| Ransom required | up to 2000 USD in Bitcoins |
| Decryptable | Yes. Some of the CryptoMix ransomware variants that have an offline key can be decrypted using. Free decryption software available |
| Removal | The only way to remove it is to scan the system with a professional antivirus |
| Repair damage | CryptoMix ransomware and its variants compromise Windows registries, drops the malicious files in the disguise of legitimate processes, and delete some of the core system executables. Consequently, Windows may experience crashes and other side effects even after ransomware removal. To fix any CryptoMix damage, use FortectIntego tool |
The CryptoMix ransomware family might append different extensions to audio, video, image, documents and other files in order to make them inaccessible. Currently, malicious programs can append these suffixes:
- .BACKUP
- .empty;
- .error;
- .ogonia;
- .dg;
- .zero;
- .ck;
- .exte;
- .code;
- .revenge;
- .scl;
- .rscl;
- .rdmk;
- .rmd;
- .wallet;
- .Mole03;
- .CNC;
- .azer;
- .lesli;
- .zayka;
- .noob;
- .cryptoshield;
- .mole02;
- .shark;
- .x1881;
- .XZZX;
- .0000;
- .TEST;
- .WORK;
- .tastylock;
- .SERVER;
- .System;
- .MOLE66
Following data encryption, all variants of CryptoMix virus deliver a ransom note where crooks provide instructions how victims can get back access to their files. After ransomware attack, people might find one of these files on the desktop or folders that include encrypted data:
- INSTRUCTION RESTORE FILES.TXT;
- _HELP_INSTRUCTION.TXT;
- !!!HELP_FILE!!! #;
- # RESTORING FILES #.HTML;
- _INTERESTING_INFORMACION_FOR_DECRYPT.TXT;
- # RESTORING FILES #.TXT;
- _HELP_INSTRUCTIONS_.TXT.
Despite the different names, the ransom payment scheme remains the same. Victims are asked to pay the ransom in Bitcoins, but first, they have to contact criminals via one of the email addresses. It’s known that malware uses these emails, but there are many more:
- backuppc@tuta.io
- backuppc@protonmail.com
- backuppc1@protonmail.com
- b4ckuppc1@yandex.com
- b4ckuppc2@yandex.com
- backuppc1@idr.com
- xoomx@dr.com;
- xoomx@usa.com;
- supl0@post.com;
- webmafia@asia.com;
- donald@trampo.info;
- exte1@msgden.net;
- exte2@protonmail.com;
- exte3@reddithub.com;
- admin@zayka.pro;
- error01@msgden.com;
- error02@webmeetme.com;
- errorout@protonmail.com;
- empty01@techmail.info;
- empty02@yahooweb.co;
- empty003@protonmail.com;
- zero@hook.work;
- x1881@tuta.io;
- x1883@yandex.com;
- x1881@protonmail.com;
- x1884@yandex.com;
- xzzx@tuta.io;
- xzzx1@protonmail.com;
- xzzx10@yandex.com;
- xzzx101@yandex.com;
- y0000@tuta.io;
- y0000@protonmail.com;
- y0000z@yandex.com;
- y0000s@yandex.com;
- test757@tuta.io,
- test757@protonmail.com,
- test757xz@yandex.com,
- test757xy@yandex.com,
- test757@consultant.com;
- t_tasty@aol.com;
- serverup@keemail.me;
- serverup@protonmail.com;
- serverup1@yandex.com;
- serverup3@yandex.com;
- sup10@post.com
- sup10@oath.com
- ann.c@iname.com;
- systempc1@keemail.me;
- systempc18x@protonmail.com;
- hashby@yandex.com;
- ashbyh@yandex.com;
- helen.a@iname.com;
- alpha2018a@aol.com.
However, it doesn’t matter which version of the ransomware infected your device, buying CryptoMix decryptor from cybercriminals is not recommended. Paying the ransom in Bitcoins will leave criminals undetected, while you will not only lose your money, but also expose yourself at risk of being scammed. Thus, you should remove CryptoMix immediately with SpyHunter 5Combo Cleaner or another security software and then try to recover encrypted files using alternative data recovery tools.
Cybercriminals are offering free technical support service
Usually the attackers try to convince their victims to pay the ransom in many different ways — threats to delete the decryption software or encrypted files, doubling the ransom, etc. Unfortunately, such techniques are highly successful and employed by the developers of other cyber threats as well. For example, CryptoWall 3.0, CryptoWall 4.0 and CryptXXX ransomware viruses. However, the attackers behind CryptoMix use a different method.

The ransomware developers, calling themselves the Cham Team, have also been offering a “Free tech support” for those who decided to pay up. Putting all these strange promises aside, you should remember that you are dealing with real cyber criminals, so there is no need to follow their commands and support their dirty business.
Even if you decide to pay the ransom in exchange for your files, you should take into account that you may not receive the access to the decryption key that you need or the key itself may be corrupted.[4]
Thus, we do not recommend following hackers’ orders provided in the INSTRUCTION RESTORE FILE.TXT file. This ransom-demanding message shows up in each folder that contains encrypted data. CryptoMix virus is said to encrypt the astonishing amount of file types – 862. Thus, it’s impossible to overlook it.
Speaking more about the content of the ransom note, cyber criminals inform a victim about two different emails, xoomx[@]dr.com and xoomx[@]usa.com, that should be used to contact the developers of Cryptomix ransomware and retrieve the affected files.[5]
After emailing the hackers, the victim is then sent a link and a password to a One Time Secret service website which can be used for exchanging anonymous messages with hackers. At first, the hackers may try to convince the victim to pay for the sake of charity. Of course, we won't find a person who is willing to pay the ransom of 1900 in USD in exchange for his or her files.
Besides, cyber criminals can start threatening you to double the ransom if it is not paid within 24 hours. The most interesting thing is that you can receive a discount after contacting these hackers[6]. In any case, we do not recommend going that far.
You should remove CryptoMix virus as soon as you notice you cannot access your files. However, you should remember that the removal of this virus will not recover your files. For that, you need to use data decryption steps given at the end of this post. If you are not infected yet, make sure your data is in a safe place before the ransomware hits your computer.
The list of versions of CryptoMix virus
CryptoShield 1.0 ransomware virus is another variant of the CryptoMix ransomware. The difference between these two cyber threats is that the latter version uses the combination of AES 256 and ROT 13 algorithms for data encryption.
However, the combination of both ciphers leads to the point where IT specialists aren't able to easily generate a decryption key and desperate users continue to pay enormous amounts of money to recover their corrupted files. However, note that there are alternative ways to get back access to your data, do not make thoughtless decisions.
Moreover, according to the experts, computer users can get infected on suspicious websites or downloading obfuscate files from peer-to-peer networks. Additionally, this variant of the ransomware uses RIG exploit kit to download the executables for the CryptoShield hijack.
Users are advised to pay close attention to the fake pop-ups since this malware imitates messages from legitimate computer processes. However, you can easily recognize an attempt to fool you by poorly written text.
.code virus. Malware is distributed via spam emails that have a malicious email attachment. Once users open the attached file, malware payload enters the system and starts the data encryption procedure. The virus uses the RSA-2048 encryption algorithm and appends .code file extension.
When all targeted files are encrypted, the ransomware drops a ransom note named “help recover files.txt” where victims are asked to contact developers via xoomx_@_dr.com or xoomx_@_usa.com email addresses. However, doing that is not recommended because cyber criminals will ask to transfer up to 5 Bitcoins for the decryption key.
Thus, it’s a huge sum of money, and you should not risk losing them. It’s better to remove .code virus first.
CryptoShield 2.0 ransomware virus. This version barely differs from earlier CryptoShield variant. After infiltration, it starts data encryption procedure using an RSA-2048 algorithm and appends .CRYPTOSHIELD extension to each of the targeted files.
Then malware creates two new files on the desktop called # RESTORING FILES #.txt and # RESTORING FILES #.html. These files include instructions how to recover encoded data. In the ransom note, cyber criminals provide few email addresses (res_sup@india.com, res_sup@computer4u.com or res_reserve@india.com) for those victims who are willing to pay the ransom.
However, doing that is not recommended. If you got infected with this version of CryptoMix, remove the virus from the computer and use data backups or alternative recovery methods to restore your files.
Revenge ransomware virus. This file-encrypting virus is distributed as a trojan via RIG exploit kits. After the infiltration, it scans the system looking for the targeted files and encrypts them using an AES-256 algorithm. Just like its name suggests, malware appends .revenge file extension to each of the corrupted file and makes them impossible to open or use.
However, cyber criminals provide instructions how to get back access to the encrypted files in the ransom not called # !!!HELP_FILE!!! #.txt. Here victims are asked to contact cyber criminals via provided email addresses: restoring_sup@india.com, restoring_sup@computer4u.com, restoring_reserve@india.com, rev00@india.com, revenge00@witeme.com, and rev_reserv@india.com.
If people decide to do that (not recommended), they are asked to transfer particular amount of Bitcoins in order to obtain Revenge Decryptor. We want to point out that this shady deal might end up with money loss or other malware attacks. Besides, encrypted files might still be inaccessible.
Mole ransomware virus. This version of CryptoMix travels via misleading emails that inform about USPS delivery issues. Once people click on a link or attachment provided in the email, they install Mole executable on the system. On the affected computer, malware immediately starts encryption procedure and locks files using an RSA-1024 encryption key.
In order to make the attack even more damaging, the malware also deletes Shadow Volume Copies. Thus data recovery without specific decryption software is nearly impossible if victims do not have backups. Following data encryption, CryptoMix Mole ransomware drops a ransom note “INSTRUCTION_FOR_HELPING_FILE_RECOVERY.TXT” where victims are told to contact cyber criminals within 78 hours.
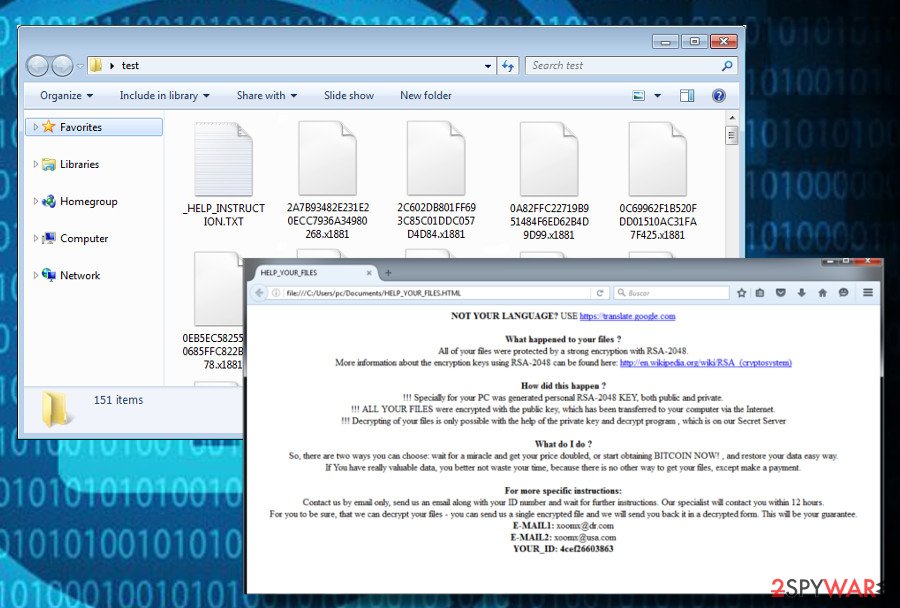
Victims are supposed to send their unique ID number either to oceanm@engineer.com or oceanm@india.com email address. However, Doing that is not recommended because people will be asked to transfer a huge sum of money and obtain a questionable decryption software. After ransomware attack, victims should focus on malware removal first.
CryptoMix Wallet ransomware virus. This variant of the ransomware uses AES encryption and appends .wallet file extension to the targeted files which resemble Wallet ransomware virus. However, the malware also renames files. The name of the encrypted file includes the email address of the cyber criminals, the victim’s ID number, and a file extension: .[email@address.com].ID[16 unique characters].WALLET.
Once all files are encrypted, victims receive a fake explorer.exe Application Error message which is supposed to trick victims into pressing OK button. Clicking OK triggers User Account Control prompt window. This alters won’t go away as long as users click “Yes” option. Since then malware starts deletion of Shadow Volume Copies.
Lastly, malware leaves a ransom note “#_RESTORING_FILES_#.txt” where victims are asked to send their unique ID number to one of these email addresses: shield0@usa.com, admin@hoist.desi, and crysis@life.com. Then, cyber criminals will provide the cost of decryption software.
However, trusting them is not recommended. Nevertheless, ransomware is still undecryptable; we do not recommend risking to lose the money or getting infected with other malware. After the attack, employ professional security software and remove it from the device.
Mole02 ransomware virus. Mole02 is yet another version of the described ransomware family, and it appends .mole02 file extensions to encrypted records. It utilizes RSA and AES encryption ciphers to securely lock victim's files. The virus first emerged in June 2017 and successfully infected thousands of computers worldwide.
The virus uses _HELP_INSTRUCTION.TXT as a ransom note. It saves this file on the desktop to inform the victim about the cyber attack and demand a ransom. However, victims do not need to pay the ransom any longer if they do not have data backups – malware experts have released a free Mole02 decryptor that restores corrupted files absolutely for free.
Azer ransomware virus. AZER Cryptomix virus is the latest version of this ransomware group that emerged right after the release of Mole02 decryptor. The new version uses either .-email-[webmafia@asia.com].AZER or .-email-[donald@trampo.info.AZER extension to mark encrypted data. The virus corrupts the original filename as well.
The ransom note dropped by this virus is called _INTERESTING_INFORMACION_FOR_DECRYPT.TXT. It is very short and it simply suggests writing to one of the provided emails to get data recovery instructions. Of course, the criminals are not planning to decrypt your files for free.
They usually demand a ransom, however, at the moment the size of it is unknown. Unfortunately, currently, there are no tools capable of decrypting .azer files.
Exte ransomware virus. This version of ransomware emerged in July 2017. The name of the virus reveals that it appends .EXTE file extension to the encrypted files. Once all targeted files are locked, malware downloads a ransom note called _HELP_INSTRUCTION.TXT. Here victims are asked to send their unique ID number to exte1@msgden.net, exte2@protonmail.com or exte3@reddithub.com and wait for the response with data recovery instructions.
Currently, the specific size of the ransom is unknown. It seems that authors of the ransomware decide on which victim individually based on the amount of the encrypted files. Despite the fact that official decryptor for Exte is not released, we do not recommend paying the ransom.
Zayka ransomware virus. Zayka ransomware is yet another version of CryptoMix. Although it works as a virtual extortion tool, it doesn't specify the size of the ransom it wants to receive from the victim. During the encryption, the virus adds .zayka file extensions to files and creates a ransom note – _HELP_INSTRUCTION.TXT.
The ransom note suggests testing the data recovery pro on three small files that can be transmitted to criminals via email. The victim can write to admin@zayka.pro to get instructions regarding data recovery. However, we do not advise you to communicate with cybercriminals or obey their demands. Instead, you should remove Zayka and start looking for your data backup.
Noob ransomware virus. CryptoMix Noob ransomware was spotted in July 2017, right after the appearance of Zayka virus. Victims should not confuse it with NoobCrypt ransomware, which is a completely different virus.
The Noob virus got its name based on file extensions it appends to encrypted files. The ransomware uses identically named ransom note like the previous versions – _HELP_INSTRUCTION.TXT. Just like Zayka, it doesn't specify the price of the ransom.
Unfortunately, at the moment we cannot provide you any good news regarding .noob file extension data decryption. As soon as the decryptor appears, the article will be updated. Until then, you need to complete Noob ransomware removal.
CK ransomware virus. Just a few days later after Noob's ransomware debut (on July 20) another version showed up. CryptoMix CK ransomware virus is a malicious program that marks encoded data with .ck file extensions. It also drops _HELP_INSTRUCTION.TXT as a ransom note, but the content of it is quite different. Instead of providing one contact email address, it leaves three of them – ck01@techmail.info, ck02@decoymail.com and ck03@protonmail.com.
It seems that it is not the latest version from this ransomware family. It is very likely that more versions will appear shortly. Although at the moment .ck files cannot be decrypted using any third-party tools, it doesn't mean that you should start negotiating with cybercriminals via email (and not only because they won't be willing to do that).
Paying the ransom doesn't mean that your files will be recovered. Therefore, it is recommended that you remove CK ransomware and try data recovery methods provided below the article.
Mole03 ransomware virus. Mole03 virus is another modification of the infamous ransomware known as Crypto Mix. It is also one of the Mole ransomware group. After infecting the system, it compromises data and adds .mole03 file extensions to them. Following that, it drops _HELP_INSTRUCTION.txt file in all compromised folders and of course, desktop. At the moment, none of the free decryption tools are capable of restoring these files.
This variant is known to be pushed via EiTest campaign and compromised websites that welcome victims with a bogus “The “HoeflerText” wasn't found” alerts. These pop-ups suggest that victim's browser doesn't have a certain font installed, and the victim needs to have it in order to view the content of the website. Sadly, the file contains the ransomware.
These compromised websites used in Mole03 campaigns are filled with script that detects what web browser the victim uses. If it detects Internet Explorer, it triggers redirect to a phishing website that belongs to tech support scammers. The website then suggests calling scammers for help regarding YahLover.worm removal.
DG ransomware virus. Also known as DG file extension virus, it is yet another variant of the infamous ransomware. The malware was first spotted on July 28, and just like previous Crypto Mix variants, it creates a _HELP_INSTRUCTION.TXT file to store the ransom note. The ransomware drops this file into several computer locations to make it more noticeable for the victim.
The ransom note discloses three criminals' email addresses – dg01@msgden.net,
dg02@armormail.net, and dg01@protonmail.com. In fact, apart from the extension used on encrypted files and different email addresses, there aren't many improvements to talk about.
The ransomware keeps playing with the details, and as always, it doesn't provide the exact ransom price – the victim has to email the victims and ask them about it. At the moment, no Cryptomix DG ransomware decryptors are available.
CNC ransomware virus. On August 7th, 2017, the cybercriminals added another update to CryptoMix which resulted in different file extensions that appear on compromised files. This time, the virus uses .CNC file extensions to mark encoded records. The name of the ransom note, however, remained the same, although its content differs slightly.
As usual, CNC ransomware virus' authors switched their contact emails. Now they suggest writing to cnc01@msgaden.net, cnc02@nerdmail.co or cnc03@protonmail.com. Frauds promise to “help you as soon as possible!” although we wouldn't name it as “help.” Remember – you are dealing with filthy cyber criminals here who seek to extort you. They will never provide you with data recovery tools if you refuse to pay them.
We heartily suggest that you think twice before paying the ransom. If you did, you would finance their future projects and motivate them to continue their illegal activities. The result of this will always be more ransomware victims.
ZERO ransomware virus. This variant first appeared at the end of July 2017. The malicious virus wasn't very prevalent if compared to other variants; however, it managed to affect quite a large number of computers worldwide.
The virus suggests writing to zero@hook.work email address for data decryption instructions. This command is written in a ransom note that is called the same way as in previous Crypto Mix variants.
The way this virus encrypts files is highly sophisticated and cannot be reversed without a unique decryption key. Unfortunately, there is no way to get this key without paying the ransom because it is securely stored in criminals' servers.
OGONIA ransomware virus. Ogonia virus is a new addition to CryptoMix virus' family. The first sample of this malicious virus was spotted on August 07, 2017. It is just another proof that ransomware developers are extremely greedy and despite all the ransoms they have already collected, they want more. The result of their greed is this new version – Cryptomix Ogonia virus.
After compromising victim's computer, the virus encodes files, adding .OGONIA file extensions on its way. It is worth mentioning that the virus completely corrupts filenames of files that it encrypts, too. This way, the victim can no longer recognize the files. The malware traditionally creates a ransom note called _HELP_INSTRUCTION.TXT, which barely contains any useful information.
Inside the text file, there is a short message: “All you files crypted. For decrypt write to: TankPolice@aolonline.top.” The decrypt ID provided in the note is used in victim's identification process – this way, the attackers know which decryption key to provide for him/her. Unfortunately, they are cyber extortionists, and they are going to ask you to pay a ransom in exchange for it.
ERROR ransomware virus. CryptoMix Error virus first emerged on August 18th, 2017. The virus continues using the same name for the ransom note, but adds .error file extension to encrypted files now. In this variant of the ransom note, cybercriminals suggest writing to error01@msgden.com, error02@webmeetme.com, error03@protonmail.com or errorout@protonmail.com for data recovery instructions. Not surprisingly, cyber criminals communicate via email to explain the conditions regarding data recovery.
The virus employs a set of 11 RSA-1024 encryption keys (public) which are used to encrypt the AES key (the one that encrypts files). This way, the victim cannot sort out what the decryption key is without cyber criminals' help.
They want the victim pay an enormous ransom to get access to corrupted files again. Unfortunately, researchers couldn't find a way to decrypt the files with .error file extensions yet. It is recommended to remove the virus without any hesitations using a proper anti-malware software for that.
EMPTY ransomware virus. It is a brand new creation from CryptoMix cyber crime gang. This new virus uses .empty extension on encrypted files and leaves three email addresses to contact victims in the _HELP_INSTRUCTION.TXT file.
The virus “kindly” suggests writing to empty01@techmail.info, empty02@yahooweb.co or empty003@protonmail.com to get a reply from cyber criminals with instructions on how to pay a ransom. The criminals promise to help the victim as soon as possible, although usually, it takes about 12 hours to get a response from them.
Since there is no way to recover .empty files for free and without having a data backup, we strongly recommend removing the ransomware from the system because it can silently drag even more malware to it.
CryptoMix Arena ransomware makes a diversion as it appends .arena file extension. Interestingly, it emerged at the same time as Crysis variant which also tends to attach .arena file extension. However, taking a closer look, the differences become obvious.
After CryptoMix Arena version finishes encoding files, it changes the file name into a hexadecimal series of numbers and characters with .arena at the end. It also launches its users' GUI with _HELP_INSTRUCTION.txt file. It briefly informs victims about the encode files and delivers ms.heisenberg@aol.com.
This version also presents vivid and complex data encryption techniques. The malware employs 11 different RSA-1024 encryption keys to encode the main key, AES, which encoded the data.[7] Thus, this feature enables the malware to function offline. In order to encourage victims to remit the payment, the perpetrators offer to decode one file for free.
However, there is no information on whether any received all files after paying the ransom. CryptoMix Arena may disguise under a random executable file so mere vigilance will not be sufficient.
Skark ransomware virus encodes data with the AES key which is again encrypted by 11 RSA-1024 public keys. This feature grants the virus the ability to function offline. This specification was introduced in the above-discussed sample.
Looking from a broader perspective, the version does not include major changes. The ransom note stays the same while it presents new email addresses for contact purposes: shark01@msgden.com, shark02@techmail.info, and shark003@protonmail.com[8]. At the moment, the decrypter for this version has not been released yet.
x1881 ransomware virus does not present any astonishing features. Changes are minimal. It mentions about encrypted data in the same ransom message. However, now it includes four email addresses for victims to contact them: x1881@tuta.io, x1883@yandex.com, x1881@protonmail.com, and x1884@yandex.com.
The threat continues using 11 RSA-1024 keys to which allows it to function offline. Users may try to use free CryptoMix decrypter to decode the files affected by this malware variation.
XZZX ransomware virus. On November 2017, developers of CryptoMix came back with a new version of malware that appends .XZZX file extension to the corrupted files. Following data encryption, cyber criminals ask victims to contact them via one of the provided emails (xzzx@tuta.io, xzzx1@protonmail.com, xzzx10@yandex.com or xzzx101@yandex.com) and wait for further instructions.
Just like the previous variant, XZZX CryptoMix ransomware also uses 11 RSA-1024 encryption keys to the corrupt files on the targeted device. Unfortunately, the sophisticated encryption method is not decryptable yet. However, users should remain patient and do not pay the ransom for criminals.
0000 ransomware virus. Following XZZX ransomware, developers presented the 0000 virus as well. It barely differs from the previous version and uses the same encryption algorithm. It locks files with .0000 file extensions and provides data recovery instructions in the _HELP_INSTRUCTION.TXT file. However, the document does not reveal any specific information.
Victims are asked to send their ID number to one of the provided email addresses: y0000@tuta.io, y0000@protonmail.com, y0000z@yandex.com or y0000s@yandex.com. However, contacting them and following their instructions is not recommended by security specialists.
Test ransomware virus. In December 2017, cyber criminals presented a new variant of CryptoMix which adds .TEST file extension to targeted files. Just like the previous two versions, it uses the same combination of RSA and AES cryptography to make data inaccessible. However, this time crooks use new email addresses for communicating with victims that are presented in the _HELP_INSTRUCTION.TXT file.
Victims are supposed to send their unique ID number to test757@tuta.io, test757@protonmail.com, test757xz@yandex.com, test757xy@yandex.com or test757@consultant.com addresses. Crooks are supposed to respond with data recovery instructions. However, doing that may lead to money loss.
Work CryptoMix ransomware. Recently, the experts have discovered a new version of the malicious program. While it has similarities with the original one, there are also slight differences. Firstly, the hackers have change en extension appended to the corrupted data — now it uses .WORK suffix.
Even though the file of the ransom note remains to be named as _HELP_INSTRUCTION.TXT, the victims are provided with new email addresses for contact purposes which are the following:
- worknow9@yandex.com;
- worknow@keemail.me;
- worknow@techie.com;
- worknow8@yandex.com;
- worknow@protonmail.com.
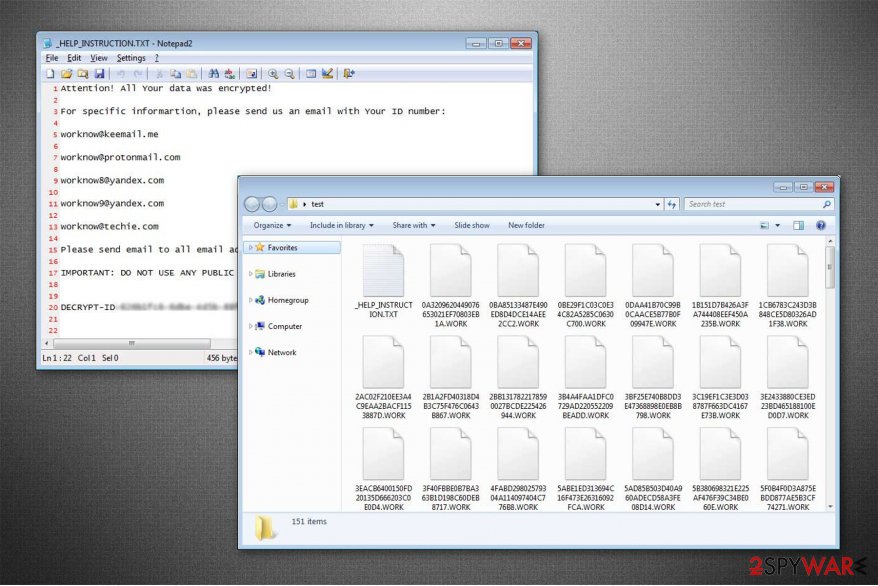
Tastylock ransomware. This crypto-virus is suspected to be another version of CryptoMix. However, it acts a little bit differently compared to the previously discussed malware. However, the virus uses the same name of the ransom note – _HELP_INSTRUCTION.TXT. However, here criminals provide a slightly altered message, but victims are still advised to send their ID number to the provided email address – t_tasty@aol.com.
However, security experts do not recommend trying to obtain a decryptor that will be able to restore files with .tastylock extension. Nevertheless, the virus is not decryptable whit third-party software; cyber criminals might only take your money and still leave you with a corrupted data.
Server ransomware. Server Cryptomix ransomware appends .SERVER file extension to the targeted files and renames them with a random string of characters. Once it makes them unable to use and open; malware delivers a ransom note in the _HELP_INSTRUCTION.TXT file. The only change in this version is that criminals use different email addresses:
- serverup@keemail.me
- serverup@protonmail.com
- serverup1@yandex.com
- serverup3@yandex.com
- ann.c@iname.com
Despite the fact that malware is currently undecryptable; it's advised to remove the Server ransomware virus. Paying the ransom and hoping for criminals' goodwill to restore your data may lead to financial loss.
System ransomware. This variant appends .System file extension to the targeted data. Just like the previous versions, this one is not decryptable too. Therefore, users are offered to take a shady hacker's deal presented in the _HELP_INSTRUCTION.TXT file. As usual, victim's are asked to send their ID number to one of the provided emails (systempc1@keemail.me, systempc18x@protonmail.com, hashby@yandex.com, ashbyh@yandex.com or helen.a@iname.com) and wait for further instructions. However, security experts recommend removing System CryptoMix ransomware instead of paying the ransom.
Mole66 ransomware. Detected at the end of March 2018, the ransomware has been spotted encrypting data with .MOLE66 file extension. When the ransomware payload is being executed, it runs BC2D64A077.exe executable and applies AES-256 cipher to corrupt the most popular file types. Mole66 CryptoMix ransomware won't initiate malicious activities if it detects Russian location settings.
Additionally, the virus runs scripts via Command Prompt to delete Volume Shadow Copies and block Windows Recovery and Restore functions. Currently, the decryptor is not available, though people are free to try a free CryptoMix decryptor after a complete Mole66 removal.
The virus creates a ransom note on the desktop, which provides hackers' email address alpha2018a@aol.com. The victim is supposed to indicate a unique identification number provided and then pay a ransom in Bitcoins within 72 hours. However, experts do not recommend paying the ransom since crooks might send you another malicious application instead a working decryptor.
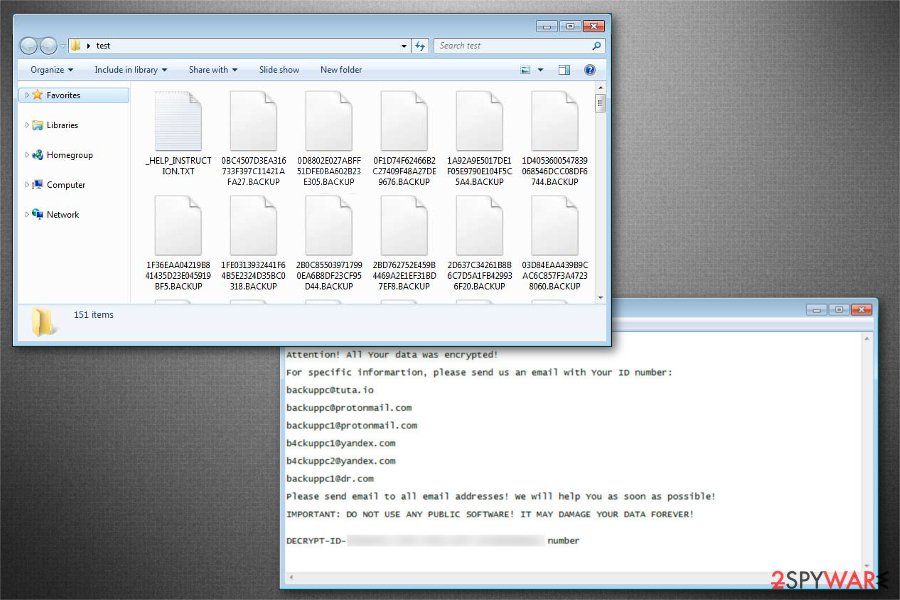
.BACKUP file extension virus. This is the newest version of CryptoMix ransomware which can be identified by .BACKUP extension at the end of the file name. Victims are encouraged to contact the criminals via email address if they want to recover compromised data.
Hello!
Attention! All Your data was encrypted!For specific information, please send us an email with Your ID number:
backuppcfltuta.iobackuppc@tuta.io
backuppc@protonmail.com
backuppc1@protonmail.com
b4ckuppc1@yandex.com
b4ckuppc2@yandex.com
backuppc1@idr.comPlease send email to all email addresses! We will help You as soon as possible!
IMPORTANT: DO NOT USE ANY PUBLIC SOFTWARE! IT MAY DAMAGE YOUR DATA FOREVER!
DECRYPT-ID-[redacted]number
Following the encryption, .BACKUP file extension virus leaves _HELP_INSTRUCTION.TXT note which provides all the necessary information for data decryption. However, we strongly advise you to never contact the criminals since there are no guarantees that you will regain access to your files.
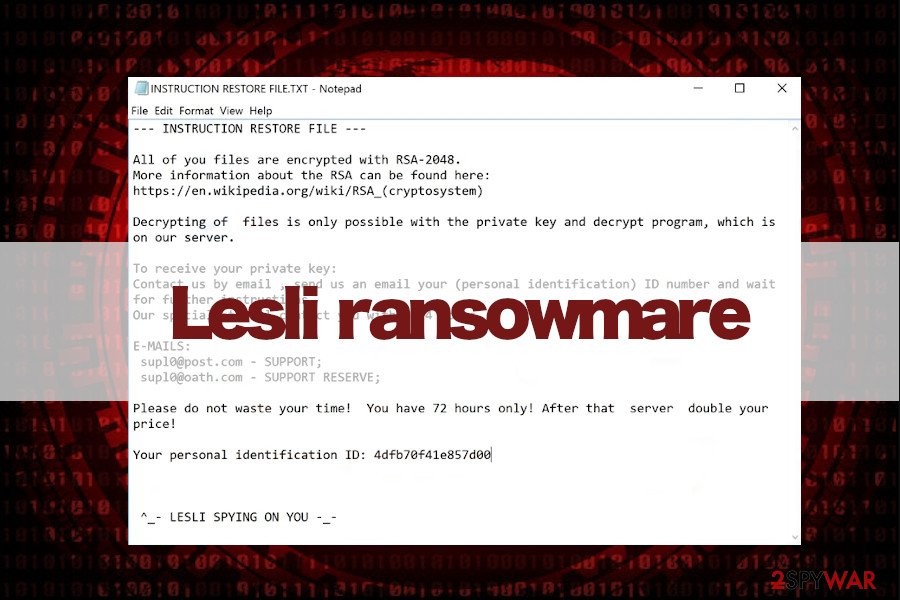
Lesli ransomware. Although some of the CryptoMix variants tend to append .lesli extension to encrypted files, it seems that the original Lesli ransomware built on a different base has been released in April 2020. It uses the RSA-2048 encryption algorithm and targets 156 file extensions on a host computer. It appends email[supl0@post.com]id[4dfb70f41e857d00].lesli file extension to each corrupted file and drops an INSTRUCTION RESTORE FILE.TXT ransom note in every folder, which contains encrypted files. The note contains the following information:
INSTRUCTION RESTORE FILE.txt
All of your files are encrypted with RSA-2048.
More information about the RSA can be found here:
hxxps://en.wikipedia.org/wiki/RSA_(cryptosystem)Decrypting of files is only possible with the private key and decrypt program, which is on our server.
To receive your private key:
Contact us by email, send us an email your (personal identification) ID number and wait for further instructions.
Our specialist will contact you within 24 hours.E-MAILS:
supl0@post.com – SUPPORT;
supl0@oath.com – SUPPORT RESERVE;Please do not waste your time! You have 72 hours only! After that server double your price!
Your personal identification ID: xxxxxxxxxxxxxx
^_- LESLI SPYING ON YOU -_-
We do not rush to pay the ransom. Experts claim that .lesli file extension is decryptable. Therefore, we highly recommend you to remove Lesti ransomware from the system immediately, make a copy of encrypted files, and then try to run decryption software to get your files back.
Multiple distribution techniques are employed to spread the infection
According to the analysis, criminals deliver file-encrypting malware in several different ways. This is because it increases the chances that more computers will be infected worldwide. Usually, they can place embed bogus scripts into ads or design legitimate-looking software to trick you into downloading ransomware.
However, most commonly it is downloaded to the system as an important email attachment, such as an invoice, business report or similar document. Some versions of malware are known for being distributed as fake package delivery notifications. Thus, you need to be careful with emails and always double-check the information before opening any attached files, links or buttons.
Therefore, it is important not only to obtain a powerful antivirus system and hope for the best but to put your effort to prevent Crypto Mix on your computer.[9] Various versions of malware using exploit kits and Trojans to infiltrate the system. To protect yourself or your business, make sure that you:
- Analyze all emails that you receive from unknown senders;
- Dedicate some time for extra research when dealing with the newly downloaded software;
- Check the reliability of the sites you decide to visit to prevent the infiltration of CryptMix ransomware.
- Taking time to install newly discovered software is also an important factor that may help you avoid the infiltration of Trojan horses used to carry this virus.
Uninstalling CryptoMix virus is a must
Those who believe that CryptoMix removal isn't necessary should rethink their option. Keep in mind that such cyber threats can be programmed to let other infections in at any time.
These malicious programs may try to block your antivirus from scanning the system. In such a case, you may have to manage the virus manually for your virus-fighting utility to be able to start. Once it's done, you can install FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes to clean up your PC.
You can quickly remove CryptoMix by following the instructions which are prepared by our team of experts at the end of this article. Also, do not hesitate to send us a message if you are encountering troubles related to the elimination of this virus.
We have received reports that the virus actively targets German-speaking countries. If your native language is German, you might want to check malware removal guidelines on DieViren.de site[10].
Getting rid of CryptoMix virus. Follow these steps
Manual removal using Safe Mode
Usually, ransomware tries to protect itself by blocking the installation of the security software. Likewise, you should start the removal procedure by rebooting your PC into Safe Mode. Get help from the guide below:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove CryptoMix using System Restore
In some cases, the previously mentioned method might not help. Hence, try another way to disable the virus.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of CryptoMix. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove CryptoMix from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by CryptoMix, you can use several methods to restore them:
Data Recovery Pro might bring back the damaged files
Experts have tried their best to develop a tool that would not only help victims after dangerous ransomware attacks but also recover files once they accidentally delete them. Likewise, we highly recommend you to try this professional data recovery tool:
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by CryptoMix ransomware;
- Restore them.
Use CryptoMix Decryptor
Experts have released a decryptor which helps to recover corrupted data. Those whose files were not encrypted using a unique key from the remote server should try this tool.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from CryptoMix and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ What is ransomware and how to remove it?. 2spyware. News and removal guides.
- ^ Gary C. Kessler. An Overview of Cryptography. Garry Kessler. online library.
- ^ CryptoMix (Offline). Avast. Cybersecurity experts.
- ^ Kacy Zurkus. Why you shouldn't pay the ransomware fee. CSO. News, analysis and research on security and risk management.
- ^ Tyler Moffitt. CryptoMix ransom note. Webroot threat blog.
- ^ Bradley Barth. Deal with the devil: Ransomware experiment proves you can negotiate price down. SC Media Magazine.
- ^ Lawrence Abrams. New Arena CryptoMix Ransomware Variant Released. BleepingComputer. News, reviews and tech support.
- ^ Lawrence Abrams. The Shark CryptoMix Ransomware Variant Smells Blood in the Water. BleepingComputer. News, reviews and tech support.
- ^ REPORT: Organizations must respond to increasing threat of ransomware. Symantec Connect. The Official Blog.
- ^ DieViren. DieViren. Malware and Security News.







