Webmail Manager email scam (fake) - Free Guide
Webmail Manager email scam Removal Guide
What is Webmail Manager email scam?
Webmail Manager email is a fake message disguised as an important letter from an email service provider
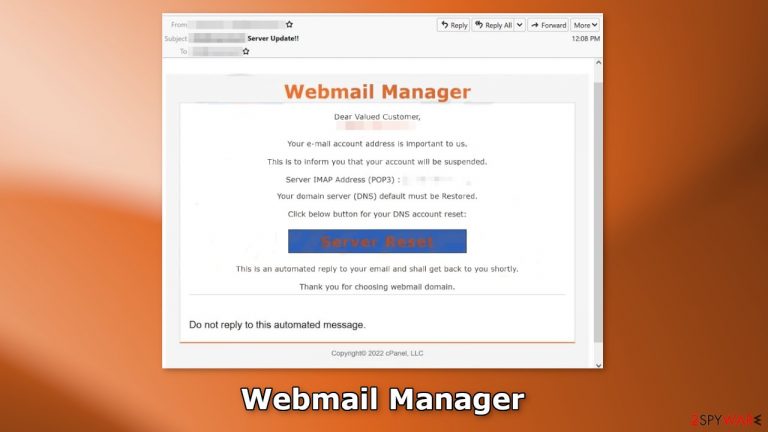
Webmail Manager email scam is a fake message crafted by crooks to lure out personal information. Their goal is to get the login details and gain access to multiple accounts. If they succeed, they can extract other personal data which could lead to serious privacy issues. Victims could suffer from monetary losses or even identity theft.[1]
| NAME | Webmail Manager email |
| TYPE | Phishing attempt |
| SYMPTOMS | Users receive an email saying their account will be suspended |
| DANGERS | Passwords and login details may be hijacked; users may suffer from financial losses and even identity theft |
| ELIMINATION | If you opened an email with a malicious link scan your computer with anti-malware tools |
| FURTHER STEPS | Use FortectIntego to clear your browsers and get rid of any remaining damage |
Webmail Manager email scam overview
The full message in the email reads as follows:
Subject: ******** Server Update!!
Webmail Manager
Dear Valued Customer,
********,Your e-mail account address is important to us.
This is to inform you that your account will be suspended.
Server IMAP Address (POP3) : ********,
Your domain server (DNS) default must be Restored.
Click below button for your DNS account reset:
Server Reset
This is an automated reply to your email and shall get back to you shortly.
Thank you for choosing webmail domain.
Do not reply to this automated message.
Copyright© 2022 cPanel, LLC
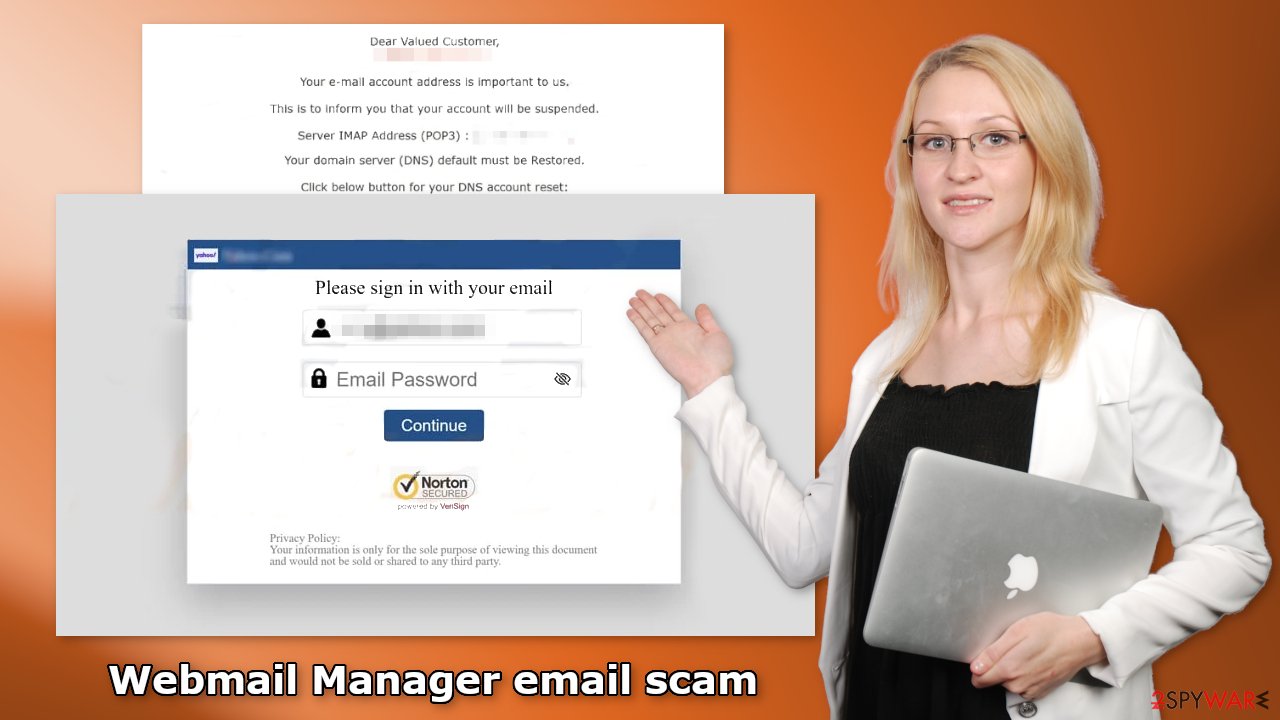
The email says that users have to restore their domain server, otherwise, the email address will be suspended. Below, there is a big “Server Reset” button provided. If users click on it, they will be redirected to a phishing[2] website that looks like a login window. Users are asked to enter their email and password.
Any information that users enter in that window, gets sent straight to fraudsters. By having the login details, they can take full control of the account. Usually, they will try to gain access to multiple accounts if people use the same password. The stolen information can also be sold to other third parties that will use it for malicious purposes.
Social engineering
Just like the Webmail Manager email, many other scammers make the emails look like important, urgent messages from well-known companies. Usually, users are asked to perform some kind of action if they do not want to suffer the consequences. The messages are created in a way to make people act immediately, without thinking.
The emails sometimes also contain infected attachments. People are asked to open them to review some kind of details, etc. However, such malicious attachments can launch malware[3] on the system so users should be very careful and not open any attachments from unknown senders.
If you think your login details could be in someone else's hands, you should change them immediately and you might manage to do it before crooks access the account. If you realized that you entered your banking information on a fake website, you should contact your bank and explain the situation. They will most likely be able to block the card and issue you a new one.
If you notice changes to the way your system operates after opening an email attachment, you should definitely scan your machine with professional security tools. Even the slightest changes, like a decrease in performance, can signal a virus infection.
Check your system for malware infections
If you suspect that you have opened an email with an infected attachment, you should take care of the threat. We recommend using SpyHunter 5Combo Cleaner or Malwarebytes security tools that will scan your machine, eliminate it, and prevent such infections in the future by giving you a warning before a malicious program can make any changes.
Crooks often disguise their malicious programs as “handy” tools so they would be more difficult to identify for the average user. People also often fail to eliminate all the related files and entries which could lead to the renewal of an infection. The program could have any name and icon, so this step is best performed by anti-malware tools.
However, if manual removal is what you prefer, we have instructions for Windows and Mac machines:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Repair the damaged operating system
Performance, stability, and usability issues, to the point where a complete Windows reinstall is required, are expected after malware infection. These types of infections can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not able to repair it.
This is why FortectIntego was developed. It can fix a lot of the damage caused by an infection like this. Blue Screen errors, freezes, registry errors, damaged DLLs, etc., can make your computer completely unusable. By using this maintenance tool, you could avoid Windows reinstallation.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
- The analysis of your machine will begin immediately
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

How to prevent from getting spam tools
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
