Whoisablet.com ads (scam) - Free Instructions
Whoisablet.com ads Removal Guide
What is Whoisablet.com ads?
Whoisablet.com shows fake requests to make people subscribe to push notifications
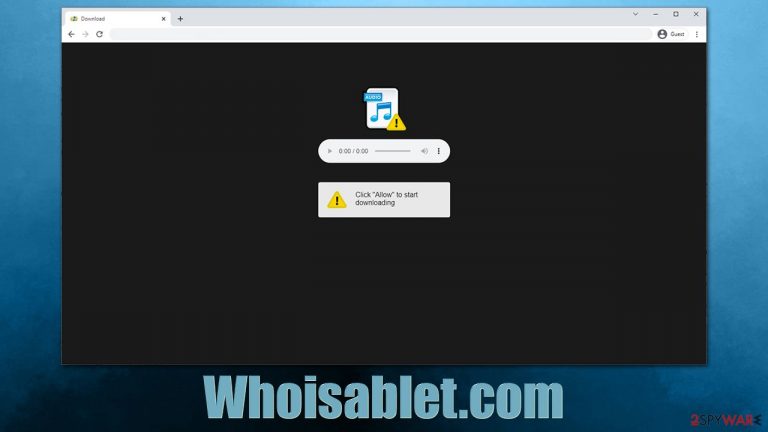
Most users see the Whoisablet.com web address after an encounter with strange pop-ups showing up at random times whenever they are doing something on a computer. This strange phenomenon is often initially treated as some type of computer infection – suspicious pop-up ads are often associated with adware.[1]
However, Whoisablet.com ads are something entirely different, as they are sent by the website only after acquiring permission to do so from users. Of course, most people are tricked into doing so after they are shown phishing messages, so they don't initially suspect anything strange.
Only sometime later do users notice push notifications from the site – they can show up at any time, as long as the browser is being used or is running in the background. Having the browser switched off at all times is not the correct solution for Whoisablet.com ads removal, so we will explain how to get rid of them easily and effectively instead.
| Name | Whoisablet.com |
|---|---|
| Type | Push notifications, ads, pop-ups, scam |
| Distribution | Intrusive pop-ups can start showing up at some point after the “Allow” button is pressed within the notification prompt |
| Symptoms | Pop-up notifications are shown on a desktop at random times |
| Risks | You might suffer from monetary losses, install malware or potentially unwanted programs, or disclose sensitive data to cybercriminals |
| Removal | To get rid of notifications, you should access your web browser settings – check the below paragraphs for more information. You should also scan your system with SpyHunter 5Combo Cleaner to check for adware and other infections |
| Other steps | You should remove caches and other web data after the elimination of adware to prevent data tracking with the FortectIntego repair and maintenance tool. You can also repair damaged system components with it |
How you end up on malicious websites
In order for push notifications scams to be successful, users need to access them in the first place. For that, scammers employ insecure advertising networks, malicious redirects, as well as adware.
Most commonly, users end up on Whoisablet.com after they click a link on high-risk websites (torrents, gambling, illegal video streaming, X-rated, etc.). These sites are often poorly regulated and serve as perfect means for cybercriminals to spread malware and insert malicious ads. In some cases, people don't even need to click anything – automatic scrips are used to redirect users to suspicious websites.
In order to avoid this, make sure you never access high-risk websites intentionally. You can also employ an ad-blocking browser extension to prevent the execution of most malicious scripts.
Adware is another reason why you encounter suspicious or malicious websites and see an increased number of ads while browsing the web. This potentially unwanted software is often spread using deceptive methods, hence people are not even aware they have it installed. Thus, we recommend checking the system for adware and malware infections.
While removal of malicious and suspicious software can be done manually, we recommend simply scanning the system with SpyHunter 5Combo Cleaner or Malwarebytes security software, which would guarantee that all malware is removed from the system at once. To repair damaged system components and clean browser caches, we recommend using FortectIntego.
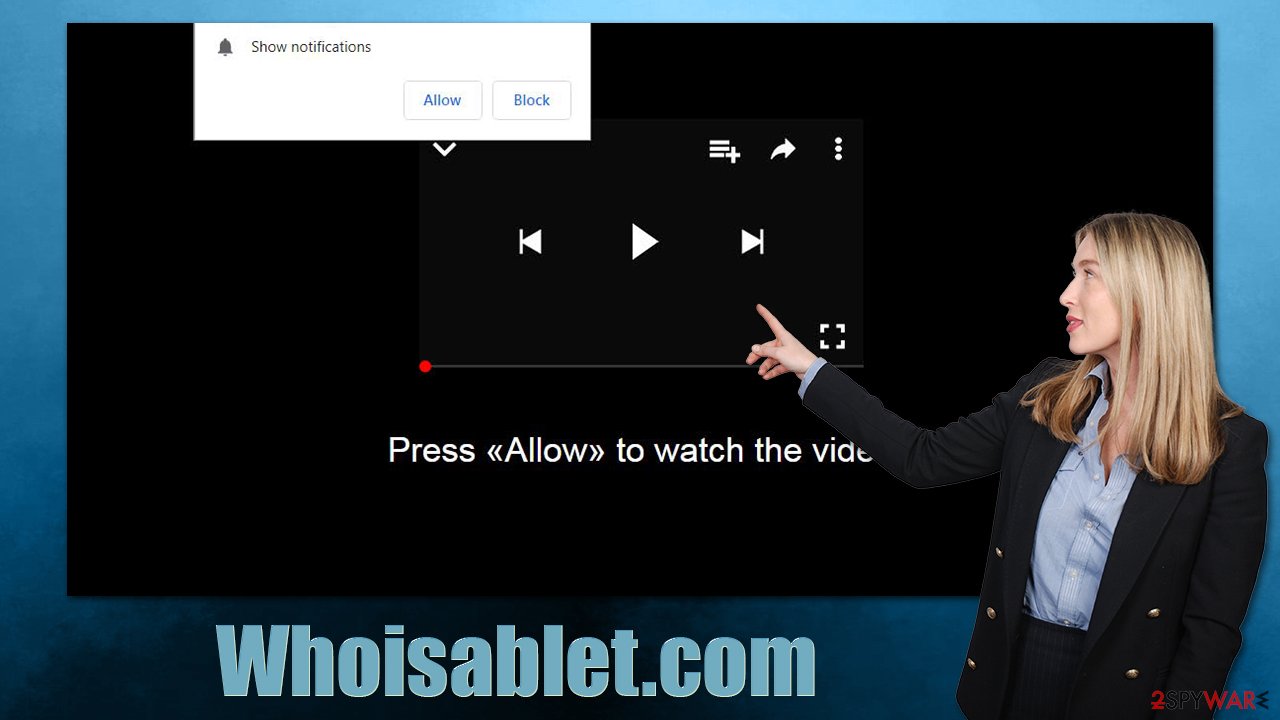
Scam scheme
Users would not subscribe to Whoisablet.com notifications considering that the site later delivers all sorts of unwanted and even malicious advertisements. The unexpected access to these fake websites is one of the main reasons why so many users get tricked – the element of surprise is very powerful in social engineering[2] schemes.
Upon the site entry, people are usually told that the “Allow” button within the notification prompt has a completely different purpose. These examples show how visitors might misinterpret the meaning of the prompt in the first place:
- Click Allow to confirm you are not a robot
- Just one more step! “Allow” to continue
- Your file is ready to download. Press Allow to continue
- If you are 18+, click Allow
- Click Allow to win a prize and get it in our shop!
If scammers convince users to click the “Allow” button, they are likely to be redirected to a similar website, e.g., Go0s.biz, Protectorofpower.xyz, or Colloredtheme.top, where they would be asked for the same thing. We recommend not interacting with these websites and ignoring all the requests to enable push notifications.
Remove annoying pop-ups
Push notifications can't be removed, as they are embedded as the API (Application Programming Interface).[3] Thus, the only way to stop a certain website from sending you notifications is to access browser settings and disable the access through there. If you haven't done this before, we provide all the required information below.
Google Chrome
- Open Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.

Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.

Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.

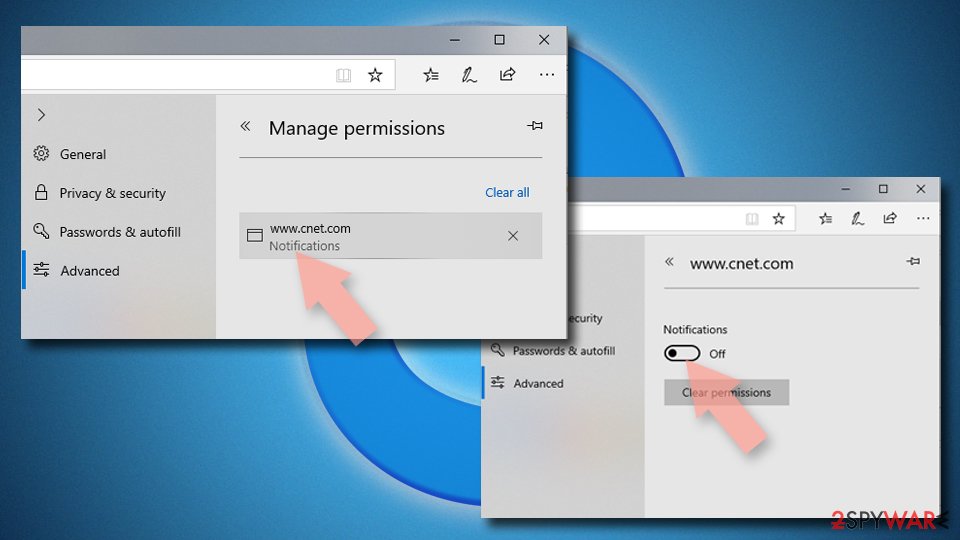
MS Edge
- Open Microsoft Edge, and click the Settings and more button (three horizontal dots) at the top-right of the window.
- Select Settings and then go to Advanced.
- Under Website permissions, pick Manage permissions and select the URL in question.
- Toggle the switch to the left to turn notifications off on Microsoft Edge.
MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.

Internet Explorer
- Open Internet Explorer, and click on the Gear icon at the top-right of the window.
- Select Internet options and go to the Privacy tab.
- In the Pop-up Blocker section, click on Settings.
- Locate web address in question under Allowed sites and pick Remove.
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
