Win32.CoinMiner (virus) - updated Jul 2021
Win32.CoinMiner Removal Guide
What is Win32.CoinMiner?
CoinMiner virus is an infection that uses resources of the machine and affects the performance significantly

CoinMiner is a type of malicious software that abuses computer resources (such as CPU and, most recently, GPU) in order to mine digital currency such as Bitcoin or Monero by performing complicated mathematical calculations. These funds are directly transferred to malicious actors' wallets over the internet. While cybercriminals profit from this activity, victims have to suffer from lag, errors, system crashes, overheating issues, as well as increased electricity bills. To make matters worse, the Coin Miner virus can also be used as a means to install other malware on the host machine.
The miner is a broad term that describes multiple different malicious activities on infected machines. There are several different ways cybercriminals can make the host PC to start mining crypto for them they can use standalone programs, browser-based miners, or malware that executes malicious payload within memory (fileless malware). Due to different principles of operation, there are also a variety of ways how users can get infected with malware, such as via fake updates, third-party software installers, torrent sites, etc.
One of the latest versions of the Coin Miner virus, which was observed in the wild, is Application.Coinminer.ge. This browser-based threat replicates itself within the browser caches as soon as it is terminated by anti-malware software. As a result, trojan, malware, or a virus removal might become tricky.
| Name | CoinMiner |
|---|---|
| Type of malware | Cryptojacking malware, Trojan |
| Symptoms | High CPU usage, Internet speed reduction, crashes, freezes, unresponsive apps, etc. |
| AV detection |
|
| Associated risks | While the impact of coin mining malware might be considered as a nuisance for some, it will often prevent users from performing high-resource required tasks, such as viewing 4K videos or playing video games. However, the main risks that are involved with cryptomining activities on the device are data theft as well as a computer security compromise |
| Distribution |
Several different ways can be used to distribute cryptocurrency miners, including:
|
| Elimination | CoinMinder malware removal depends on many factors, such as whether the infection is browser-based, or it is installed as a standalone application. In some cases, it is enough to leave a website that is set to mine currency in the background, while other times advanced malware might be difficult to get rid of even with anti-malware software |
| System Recovery | CoinMinder might seriously damage several Windows processes or even corrupt some system files, especially if it has been running for a while. Upon successful elimination, we highly advise using PC repair tools like FortectIntego in order to fix underlying issues after virus infection |
Because of the Application.CoinMiner requires a significant amount of computer resources to calculate mathematical equations, users who get infected with cryptojackers can usually notice that something is wrong right away, as their computers begin to lag significantly. Once the Task Manager is opened, victims may see a suspicious executable running and using a significant amount of CPU (can go up to 100%).
Fortunately, the trojan can be detected with the help of majority of security applications, including Windows Defender.[2] Typically, it is reported as a trojan infection indication. If this malware happens to infiltrate your operating system, it should be blocked within seconds. However, outdated security tools may fail to recognize and neutralize it.
Since its appearance of the original version, malware has shown up under different versions. Here are just a few of them[3]:
- Win32/CoinMiner.EE
- Win32/CoinMiner.DV
- Win32/CoinMiner.BB
The miner might also execute cgminer.exe[4] command on the system. Though the miner does not leave any visible traces on the PC desktop, you can suspect its presence when the device starts underperforming. System programs may start lagging to open or become non-responsive. You might also detect the trojan task in the Task Manager.

Certainly, the slow computer system is one of the main issues related to cryptocurrency miners. To improve your computer's functionality and start using it as previously, you need to remove the CoinMiner virus without wasting your system's resources. If you want to make sure that this threat doesn't hide on your computer anymore, you can rely on SpyHunter 5Combo Cleaner or Malwarebytes.
Browser-based cryptojackers can be a pain to get rid of
Cryptocurrency jacking malware was extremely prevalent when the Bitcoin value went up drastically at the end of 2017. Once the digital currency prices went down, ransomware took over crypto-malware, although that does not mean that it dissipated from the cyber-criminal world, and they keep reappearing. One of such examples is Application.coinminer.ge, which emerged in mid-February 2020.
Application.coinminer.ge virus can reside in the cache of various web browsers, including Internet Explorer, MS Edge, Google Chrome, Mozilla Firefox, etc. The cache is located in a sub-folder of C:\Users\USER\AppData\Local, and users need to find it and delete it in order to remove the threat from their machines. Unfortunately, even anti-malware software might fail to do that automatically, so the best solution would be clearing the Temporary Internet files, website data, history, and other files via the browser settings.
Additionally, users might want to clean other temporary files located on their Windows computers. For more details of how to terminate these caches, please check the instructions provided in the bottom section below.
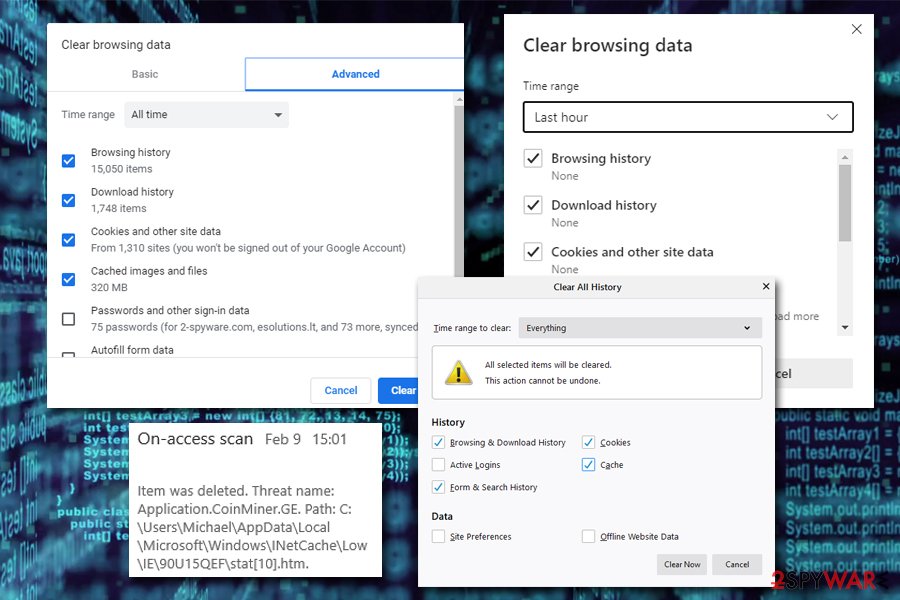
Miners – under the cover of browser extensions
Mining cryptocurrency is a new wave among malware developers. Discovered ample browser plug-ins in the Chrome Web Store, apps in Google Play and Apple stores prove such a statement.[5] Fortunately, you may ward off such unwanted software by using specific anti-coin-mining browser add-ons. However, choose wisely before installing one.
Furthermore, if you update your anti-virus tool, it will also be able to block such infections. Since some hackers are shifting their focus on crypto-currency miners rather than ordinary malware, it would be a fatal mistake to disregard the possibility that such miners might be delivered alongside ransomware – to double the perpetrator's profits.
Therefore, it is of utmost importance to keep your system updated. In addition, pay attention to what and where you download new apps from. Note that free sound editing utilities, media players, and file converters often bear unwanted attachments under “Recommended” or even “Custom” settings. Inspect the stages of installation stages before hitting the “Install” button.
CoinMiner removal steps that you need to follow thoroughly to eliminate the trojan
Updated anti-virus utility will block the threat before it settles on the system, so make sure you install reliable security software before it gets onto your computer without your approval and starts mining cryptocurrency for your money. According to some users[6], Windows Defender and other third-party software did not help them remove the virus. In that case, you may run the scan with SpyHunter 5Combo Cleaner, Malwarebytes, or similar malware removal software. FortectIntego will help you fix virus damage.
In case the crypto-coin miner infiltrated your PC system together with another Trojan or backdoor, restart the computer in Safe Mode and run a full scan with your anti-virus to find hidden trojan components.
In case you are dealing with a browser-based infection, regular CoinMiner removal steps might not be effective. During the operation of your PC, a multitude of files are created on your system to access them quickly, and these files can be used by malicious programs as well – in this case, cryptocurrency mining.
Therefore, you need to make sure you delete the following from your web browsers:
- Temporary files from websites
- History
- Download History
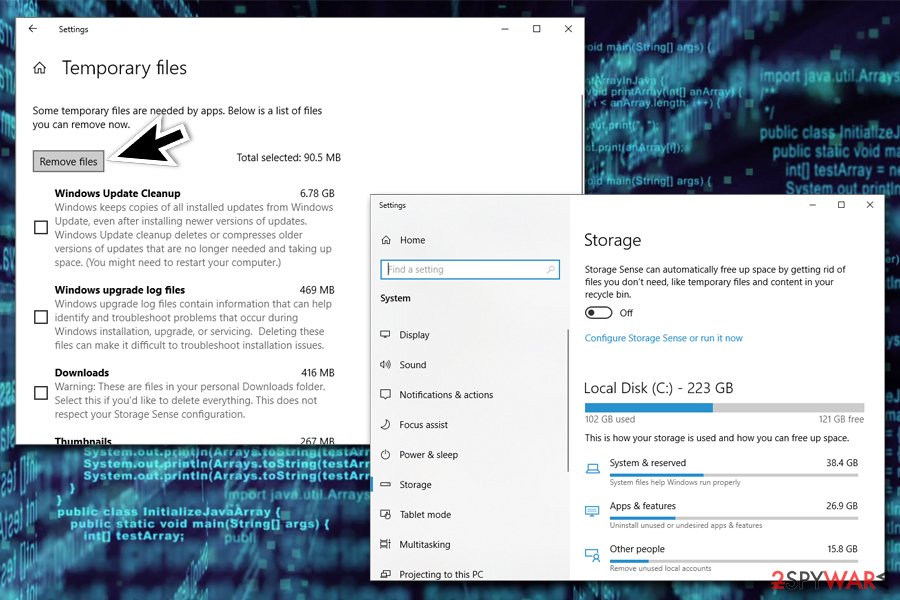
Additionally, you might want to use a built-in feature in Windows – can also help you get rid of temporary files from the system, not only web browsers:
- Type in Delete temporary files into Windows search box and hit Enter
- Go to Temporary files
- Mark appropriate categories (like Temporary files and Temporary Internet Files) and pick Remove files
Getting rid of Win32.CoinMiner. Follow these steps
Isolate the infected computer
Some ransomware strains aim to infect not only one computer but hijack the entire network. As soon as one of the machines is infected, malware can spread via network and encrypt files everywhere else, including Network Attached Storage (NAS) devices. If your computer is connected to a network, it is important to isolate it to prevent re-infection after ransomware removal is complete.
The easiest way to disconnect a PC from everything is simply to plug out the ethernet cable. However, in the corporate environment, this might be extremely difficult to do (also would take a long time). The method below will disconnect from all the networks, including local and the internet, isolating each of the machines involved.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
If you are using some type of cloud storage you are connected to, you should disconnect from it immediately. It is also advisable to disconnect all the external devices, such as USB flash sticks, external HDDs, etc. Once the malware elimination process is finished, you can connect your computers to the network and internet, as explained above, but by pressing Enable instead.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Win32.CoinMiner and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Cedric Pernet, Vladimir Kropotov, and Fyodor Yarochkin. Advanced Targeted Attack Tools Found Being Used to Distribute Cryptocurrency Miners. Trend Microt. Security Intelligence Blog.
- ^ Trojan:Win32/CoinMiner. Microsoft Official Site.
- ^ Win32/CoinMiner. ESET Virus Radar. Information on current virtual threats.
- ^ cgminer.exe. File. Windows 7/8/10 file forum.
- ^ Joon Ian Wong. North Korea could be secretly mining cryptocurrency on your computer. Quartz. IT news and insights.
- ^ Trojan.win32/CoinMiner.AQ not removing. Microsoft Support Forum.
