“Windows Defender Security Center” pop-up scam (fake) - Free Guide
“Windows Defender Security Center” pop-up scam Removal Guide
What is “Windows Defender Security Center” pop-up scam?
“Windows Defender Security Center” pop-up scam can cause monetary losses and damage to your system
“Windows Defender Security Center” pop-up is a fake message created by crooks to make a profit from innocent Windows users. The scam tries to convince people that their system is in danger because it was infected by spyware. Fraudsters use clever deception tactics to scare people into taking action.
Scammers want people to call the provided number. Once on the call, they try to gain remote access to the device by trying to convince users that they will solve the problem. Then they can start performing fake system scans, uninstall trustworthy security tools, and download fake antivirus software. Users' machines can get infected by malware, trojans, and ransomware.
People should also be aware that scammers are capable of installing RATs (Remote Access Trojans).[1] They provide the ability to access the machine without the users' knowledge for an unlimited amount of time. Fraudsters can gain control over users' personal files, like photos, videos, documents. The data can be sold on underground forums or used for blackmail.
| NAME | Windows Defender Security Center |
| TYPE | Phishing attempt; adware |
| SYMPTOMS | A fake message appears trying to convince users that their system is in danger |
| DISTRIBUTION | Shady websites; deceptive ads; freeware installations |
| DANGERS | Scammers can lure out personal information, convince victims to pay for bogus security software, or infect their systems with malware |
| ELIMINATION | Check your browser for malicious extensions and scan your machine with anti-malware tools |
| FURTHER STEPS | Use FortectIntego to get rid of any remaining damage and clear your browser |
Social engineering techniques
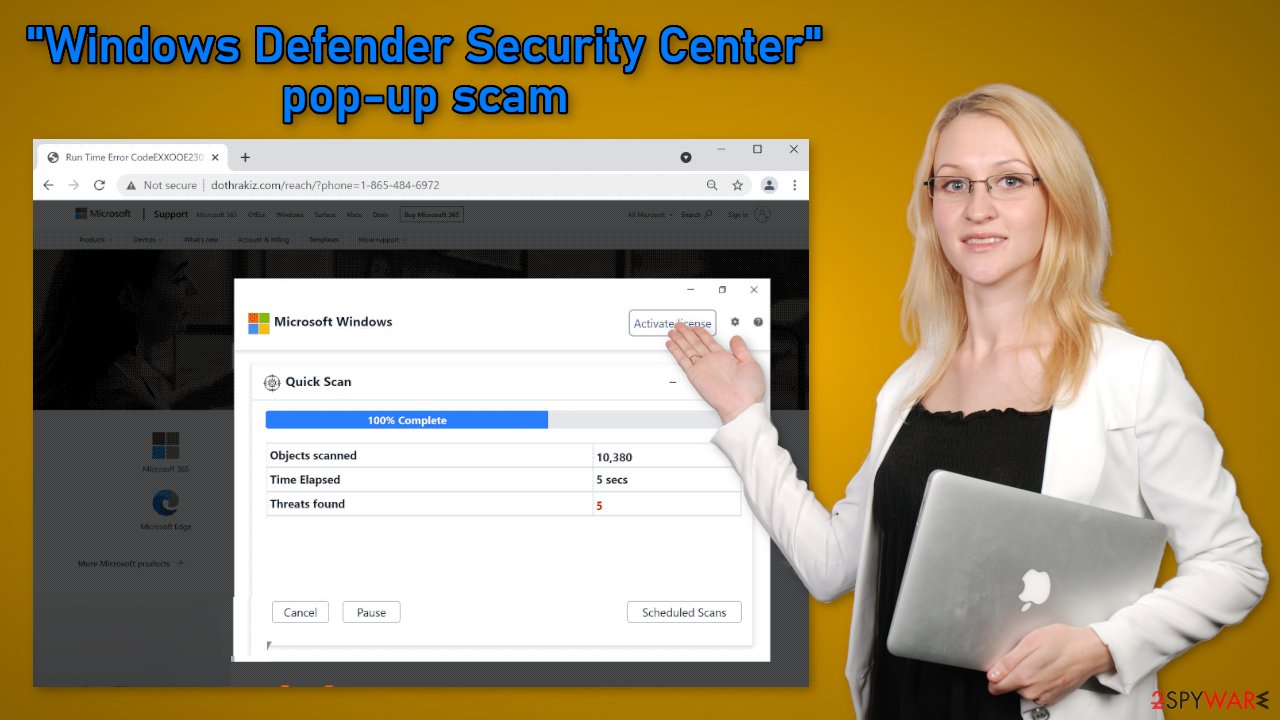
The “Windows Defender Security Center” pop-up scam displays this message:
Windows-Defender – Security Warning
** ACCESS TO THIS PC HAS BEEN BLOCKED FOR SECURITY REASONS **
Your computer has alerted us that it has been infected with a DOSAttack Spyware. The following data has been compromised.
> Email Credentials
> Banking Passwords
> Facebook Login
> Pictures & DocumentsWindows-Defender Scan has found potentially unwanted Adware on this device that can steal your passwords, online identity, financial information, personal files, pictures or documents.
You must contact us immediately so that our engineers can walk you through the removal process over the phone.
Call Microsoft Support immediately to report this threat, prevent identity theft and unlock access to this device.
Closing this window will put your personal information at risk and lead to a suspension of your Windows Registration.
Call Microsoft Support: 1-865-484-6972 (Toll Free)
The page is disguised to look like a legitimate Microsoft alert that warns about danger. Multiple banners show up on the screen to intimidate users even more. People may also see a supposed system scan in process. It is just a fake animation meant to make the pop-up look legitimate.
As you can see, the message gives the impression that users' computers have been blocked because they are infected by spyware. There should be no need to mention that this is not true. Microsoft will never randomly show alerts while you are browsing the web. If you see such a message, look for grammar and spelling mistakes, as crooks often make them. Also, inspect the URL and determine if it seems legitimate.
Distribution methods
Users rarely stumble upon Windows tech support scams through the search results. They hide in other shady pages that often engage in illegal activities. Unregulated sites can be full of deceptive ads and sneaky redirects so be careful while browsing the web and do not click on random links and buttons.
Another thing you should note is the danger of peer-to-peer file-sharing platforms, and torrent websites.[2] They are breeding grounds for all kinds of malware. The best you can do is get your software from official developer websites. Even though it might get costly, you will most likely save in the long run by keeping your system safe and healthy.
Your machine could also be infected by adware[3] which is causing this erratic behavior. It is a type of PUP (potentially unwanted program)[4] that can generate commercial content on your device. You may experience pop-ups, banners, and redirects. They can appear without any user input.
Adware is most often spread through freeware[5] distribution platforms. They include additional programs in the installers without clearly disclosing it. Usually, people just skip through the installation process to be able to test the new software as soon as possible and this is the biggest mistake.
To avoid PUPs from sneaking into your system, you should apply certain security measures. Always choose the “Custom” or “Advanced” installation methods, read the Privacy Policy and Terms of Use. The most crucial part is to inspect the file list and uncheck the boxes next to any suspicious or unrelated items.
Remove possible browser hijackers
The “Windows Defender Security Center” pop-up scam might have appeared because your browser is hijacked. You can learn more about how browser hijackers operate from the articles we wrote about the most recently detected ones, like Custom Search Bar, Clear Search, and Live-Secure. We recommend going to your browser settings and removing all the installed extensions one by one to see if you notice any changes:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the window's top-right).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
MS Edge (legacy)
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.
![Remove extensions from Edge Remove extensions from Edge]()
You should clear your browsers from cookies and cache. Cookies are small text files that can store information such as your IP address, geolocation, websites you visit, links you click on, and things you purchase online. Some websites and browser add-ons can collect this data and later sell it to advertising networks or other third parties.
Use a maintenance tool like FortectIntego for a quick and easy process. This powerful software can get rid of cookies and cache automatically. Besides, it can fix various system errors, corrupted files, and registry issues which is especially helpful after a virus infection.
Scan your machine with professional security tools
To ensure that your system is free from intruders that could be causing Microsoft tech support scams to appear we recommend scanning your system with security software. SpyHunter 5Combo Cleaner and Malwarebytes are great options because they are proven and trusted anti-malware tools. They can detect most threats hiding in your machine, and eliminate them completely. Security software can also warn users about potential threats before they can make any changes.
Manual removal can sometimes result in the renewal of infection as users fail to eliminate all the related files that are hidden in various folders. Besides, crooks often disguise PUPs as “handy” tools to not cause any suspicion. It can be difficult to identify threats if users do not know their exact names. A PUA can look like antivirus software, system optimizer, etc. However, if you still want to do this yourself, you can proceed with the guide below:
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till the uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ What is a Remote Access Trojan (RAT)?. Proofpoint. IT Services.
- ^ John Machay. What Are the Dangers of Torrents?. Smallbusiness. Security Blog.
- ^ Adware. Malwarebytes. Cybersecurity Basics.
- ^ Potentially unwanted program. Wikipedia, the free encyclopedia.
- ^ Tales From the SOC: Dealing with the Dangers of Freeware. Infosecurity. Cybersecurity Research.






