$100 Amazon Gift Card email virus (scam) - Free Guide
$100 Amazon Gift Card email virus Removal Guide
What is $100 Amazon Gift Card email virus?
$100 Amazon Gift Card email virus spreads malware that can record your keystrokes
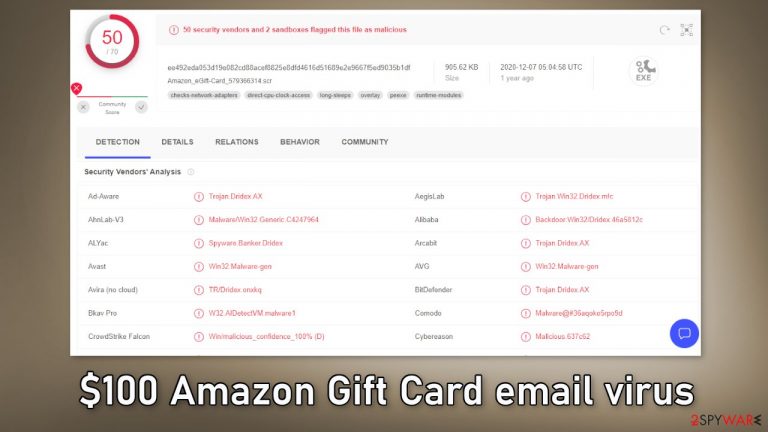
“$100 Amazon Gift Card email virus” is an email spam campaign meant to distribute Dridex malware. The deceptive message tries to convince users that they have received a gift card from Amazon. However, Amazon has nothing to do with this fraudulent campaign and it is entirely fabricated by cybercriminals.
The link embedded in the email downloads a malicious file (SRC file or Microsoft Office document) and when it is launched, it initiates the infection of Dridex. The malicious program can extract information that relates to finances and banking.
It mainly uses keylogging[1] for this purpose, which means that it can record users' keystrokes, allowing threat actors to access typed information. The infection may result in other system infections, serious privacy issues, financial losses, and even identity theft.
| NAME | $100 Amazon Gift Card |
| TYPE | Banking malware; spyware |
| SYMPTOMS | An email message encourages users to claim an Amazon gift card |
| DISTRIBUTION | Email; malspam; “cracked” software installations |
| DANGERS | Interacting with the email may result in malware infections, monetary losses, identity theft |
| ELIMINATION | Scan the system with professional security tools |
| FURTHER STEPS | Use a repair tool FortectIntego to fix any remaining damage and optimize the machine |
The malicious email campaign
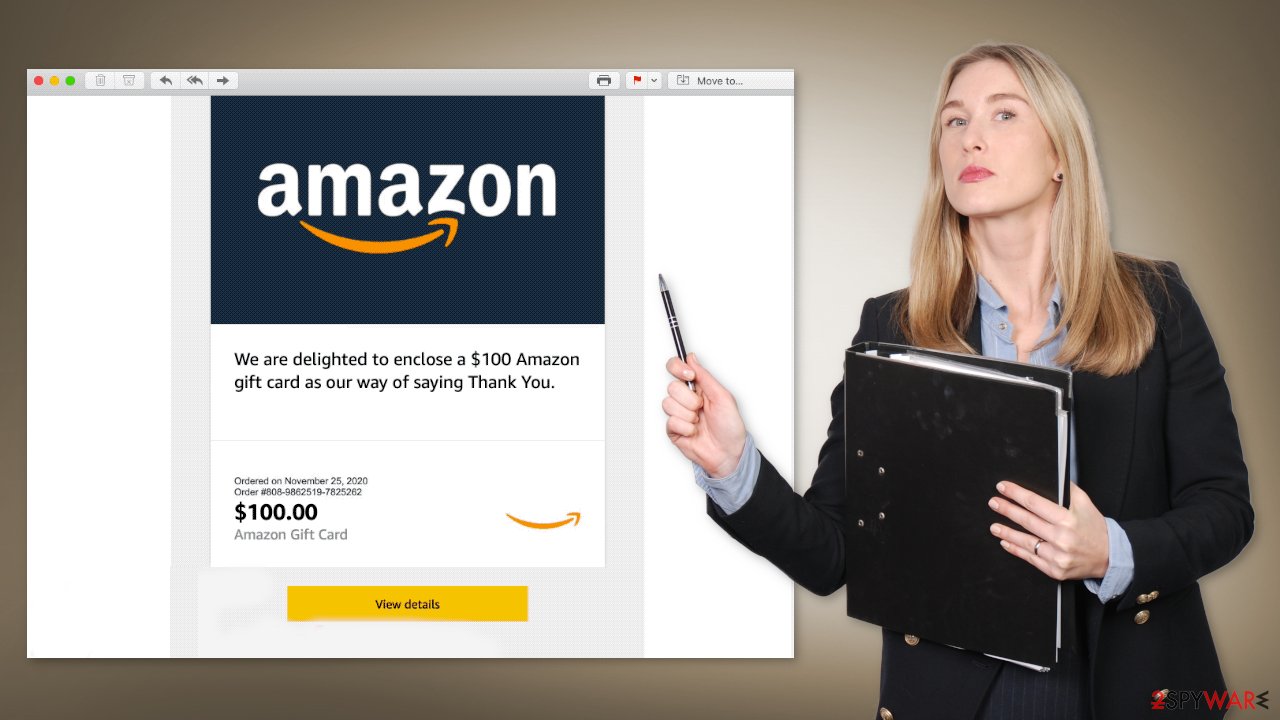
The full message of the “$100 Amazon Gift Card” rogue email reads as follows:
Subject: Amazon.com sent you an Amazon Gift Card!
We are delighted to enclose a $100 Amazon gift card as our way of saying Thank You.
Ordered on November 25, 2020
Order #808-9862519-7825262
$100.00
Amazon Gift CardView details
Don't have an Amazon account?
Sign up to redeem.
Once applied to your Amazon account, the entire amount will be added to your gift card balance. Your gift card balance can't be transferred to other accounts, used to buy other gift cards, or, except as required by law, redeemed for cash.
Your gift card balance will be applied automatically to eligible orders during the checkout process and when using 1-Click. If you don't want to use your gift card balance on your order, you can unselect it as a payment method in checkout.Amazon.com Logo
Share via FacebookTweet itPost to InstagramPin it on Pintrest
This email message was sent from a notification only address that cannot accept incoming email. Please do not reply to this message.
Sold by ACI Gift Cards LLC., an Amazon company. View Terms and Conditions.
Threat actors often use social engineering techniques[2] in their fraudulent campaigns. In this particular one, the branding of Amazon was chosen. It is a very well-known company around the world. Crooks use the trust that such companies build with their customers and exploit it.
Spam mail is not only used to deliver malicious programs – but it's also used for phishing and other scams. Fraudsters often create messages that offer various prizes, gifts, discounts, and deals. Crooks can also use scare tactics and make requests, demands, and even threaten users.
The main goal of such campaigns is always to generate revenue from innocent users. That is why you should always be extra careful opening emails from unknown senders, and downloading attachments you were not expecting.
How to avoid malware infections?
In the “$100 Amazon Gift Card email virus” specifically, the “View details” button is used to redirect people to a malicious website, from which either a dangerous SRC file or Microsoft Office document is downloaded. Some other files that cybercriminals include in their emails are Microsoft Office and PDF documents, executables (.exe), JavaScript, and archives (ZIP, RAR).
Malicious documents that are opened with Microsoft Office 2010 or newer versions install malicious software only if users enable macros commands (enable editing/content). That is why it is best to disable them completely and enable them only when needed.
These Microsoft Office versions also provide a “Protected View” mode, which does not allow opened malicious documents to install malware automatically. Older versions do not include this feature and install malicious software without asking permission. So you may also think about getting a newer version if you do not have it.
If you want to avoid virus infections through email, it is strongly suggested not to open suspicious emails, especially those with attachments or links embedded in them. Even if you receive an attachment from someone on your friend list, it is best to double-check with them through another communication platform.
You should also only use official web stores and developer websites whenever you want to install software. Pirated, or “cracked” software[3] is unsafe as the platforms distributing them are unregulated. Threat actors often include malicious programs in the installers.
Additionally, the operating system and all programs should be updated regularly to ensure device integrity and user safety. Cybercriminals also like to use software vulnerabilities to deliver malware, so it is extremely important to install the most recent security patches.[4]
Scan your system with anti-malware tools
If you opened the “$100 Amazon Gift Card” email, you should scan your system with professional security tools. They can scan the machine and detect suspicious processes running in the background. FortectIntego and SpyHunter 5Combo Cleaner can automatically eliminate intruders with all the related files and entries. If the Dridex malware is not letting you use antivirus in normal mode, access Safe Mode and perform a full system scan from there.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

Once you reach Safe Mode, launch SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable antivirus, update it with the latest definitions, and perform a full system scan to eradicate malware and all its malicious components.
Repair the damaged operating system
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstallation is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors,[5] freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
How to prevent from getting malware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Keystroke logging. Wikipedia, the free encyclopedia.
- ^ Cynthia Gonzalez. Top 8 Social Engineering Techniques and How to Prevent Them [2022]. Exabeam. Information Security.
- ^ Georgina Torbet. 5 Security Reasons Not to Download Cracked Software. Makeuseof. Technology Blog.
- ^ Why is it Important to Update Security Patches?. Netcov. IT Services.
- ^ Tim Fisher. Blue Screen of Death (BSOD). Lifewire. Software and Apps.
