1500dollars ransomware (Virus Removal Guide) - Recovery Instructions Included
1500dollars virus Removal Guide
What is 1500dollars ransomware?
1500dollars ransomware – a data-locking and blackmailing virus that provides in-depth payment instructions
1500dollars ransomware is a file-locking virus that encrypts data on a targeted computer and then tries to extort money for a promised decryption tool. This particular virus derives from the Phobos ransomware family. Viruses from this lineage have been terrorizing computer users since October of 2017.
Its previous variants (Eking, Acuff) are very similar in some ways. For example, the way they append files. 1500dollars ransomware virus appends a complex three-part extension to all non-system files, which consists of appointed victim ID (in brackets), criminal email address(also in brackets) and .1500dollars appendix.
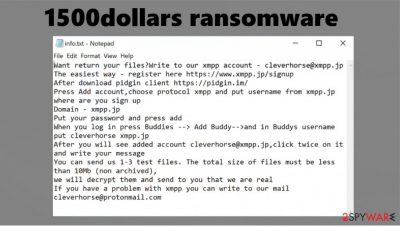
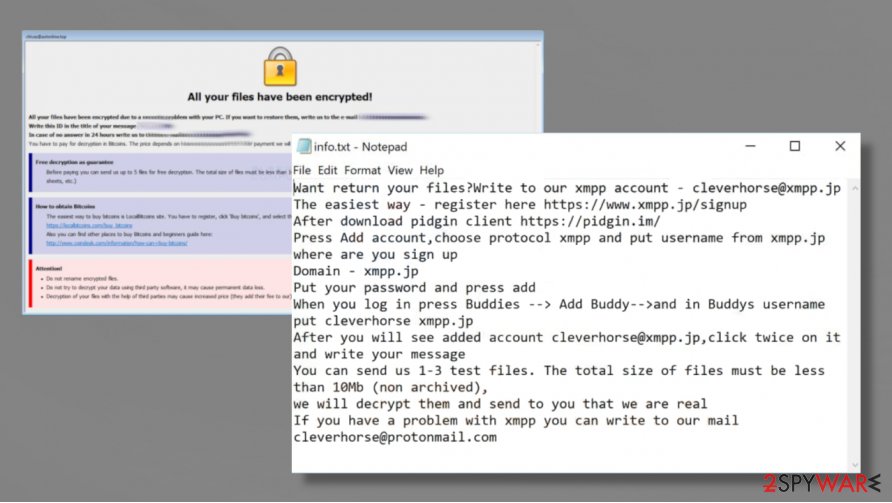
When all personal files (documents, archives, pictures, etc.) are renamed and encrypted, two types of ransom notes are created – a pop-up window and info.txt text files (both messages from the cybercriminals can be seen at the bottom of this paragraph). Unlike other ransomware (like SWP or Dex), ransom notes from the creators of 1500dollars ransomware are very informative.
| name | 1500dollars ransomware |
|---|---|
| type | Ransomware/ cryptovirus |
| family | Phobos ransomware |
| Appended file extension | A tricky triple extension is appended to all non-system files: 1. appointed victim ID in brackets; 2. criminal email in brackets; 3. .1500dollars appendix |
| Ransom note | A pop-up window (info.hta) and text files (info.txt) |
| Criminal contact details | One email address – cleverhorse@protonmail.com, and one Jabber ID – cleverhorse@xmpp.jp, are provided to establish contact |
| Virus removal | 1500dollars ransomware should be eliminated from an infected system ASAP with the help of professional anti-malware software |
| System health check | After 1500dollars ransomware removal, computer users should tweak the system with a powerful system tune-up tool like the FortectIntego app |
In the pop-up windows, creators of 1500dollars ransomware explain to the victims what has happened – that all their files are encrypted because of security issues. They provide two contact options, one email address (cleverhorse@protonmail.com), and one instant messaging service Jabber ID (cleverhorse@xmpp.jp).
As a gesture of good faith, the cybercriminals are offering to send them no more than three files for free 1500dollars ransomware virus decryption, thus proving that they really possess the necessary tool. Each victim is appointed with a unique ID which should be sent to them upon establishing contact.
The rest of the message is instructions on how to acquire cryptocurrency Bitcoins (preferred payment method of the developers of 1500dollars ransomware). Then a very detailed instruction on how to register and install Jabber. And lastly, the cybercriminals warn the victims not to rename the files or try any third-party decryption software as that might lead to permanent data loss.
The ransom message in the text files (info.txt) is all bout how to register and install Jabber software on a computer or mobile phone. It seems that the criminals are trying their best to convince victims to contact them via this software by offering alleged tools of 1500dollars ransomware file recovery.
Contacting the criminals and paying them off could seem like the easiest way out, but the FBI thinks otherwise[1]. Each victim that pays the ransom fuels future attacks of cybercriminals. When they get paid they get motivated to attack more innocent people and create more sophisticated malware than 1500dollars ransomware virus.
Instead, people should focus on malware removal. We advise using a trustworthy SpyHunter 5Combo Cleaner or Malwarebytes apps to remove 1500dollars ransomware from their infected computers. Both of these apps are time-tested and will do the dirty work for you.
When 1500dollars ransomware removal is done with, and your device is virus-free it's time to take care of its overall health. Malware is known to change system settings and its files to help it with its purpose. Using the FortectIntego tool might help restore any changes done to the system.
Creators of 1500dollars ransomware send this message with the ransom note pop-up window:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail cleverhorse@protonmail.com
Write this ID in the title of your message –
If there is no response from our mail, you can install the Jabber client and write to us in support of cleverhorse@xmpp.jp
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 1-3 files for free decryption. The total size of files must be less than 10Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
hxxps://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins/
Jabber client installation instructions:
Download the jabber (Pidgin) client from hxxps://pidgin.im/download/windows/
After installation, the Pidgin client will prompt you to create a new account.
Click “Add”
In the “Protocol” field, select XMPP
In “Username” – come up with any name
In the field “domain” – enter any jabber-server, there are a lot of them, for example – exploit.im
Create a password
At the bottom, put a tick “Create account”
Click add
If you selected “domain” – exploit.im, then a new window should appear in which you will need to re-enter your data:
User
password
You will need to follow the link to the captcha (there you will see the characters that you need to enter in the field below)
If you don't understand our Pidgin client installation instructions, you can find many installation tutorials on youtube – hxxps://www.youtube.com/results?search_query=pidgin+jabber+install
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Here's the message from the text file ransom note:
Want return your files?Write to our xmpp account – cleverhorse@xmpp.jp
The easiest way – register here hxxps://www.xmpp.jp/signup
After download pidgin client hxxps://pidgin.im/
Press Add account,choose protocol xmpp and put username from xmpp.jp where are you sign up
Domain – xmpp.jp
Put your password and press add
When you log in press Buddies –> Add Buddy–>and in Buddys username put cleverhorse xmpp.jp
After you will see added account cleverhorse@xmpp.jp,click twice on it and write your message
You can send us 1-3 test files. The total size of files must be less than 10Mb (non archived),
we will decrypt them and send to you that we are real
If you have a problem with xmpp you can write to our mail cleverhorse@protonmail.com
Guidelines to add some security to your computer system and evade ransomware
Nowadays, the internet is full of all kinds of malware.[2] But we're here to help you so if you stick to our shortlist of suggestions you might dodge it:
- Backups, backups, backups. All computer users should have backups of all their essential data. In other words, keep backups in at least two separate locations, like cloud, USB drives, etc.
- Keep your Operating System updated with the latest updates.
- Acquire, regularly scan the whole system and constantly update a trustworthy anti-malware software.
- Purchase a powerful system tune-up tool so your device's health is looked after.
- Don't visit shady sites.
- Don't use file-sharing platforms like The Pirate Bay.
- Don't open spam emails. Don't download any email attachments without scanning them first.
Removal instructions for 1500dollars ransomware
Removing malware manually can be a challenging task even for tech-savvy computer users, so we're advising leaving the dirty work for professionals. Use SpyHunter 5Combo Cleaner or Malwarebytes antimalware software to perform a full system scan and automatically remove 1500dollars ransomware.
Experts[3] advise using the FortectIntego app following a successful 1500dollars ransomware removal to check if the system files and settings are intact. Malware can change these settings and files to help it with its purpose. If left unattended these changes might lead to computers exhibiting abnormal behavior.
Getting rid of 1500dollars virus. Follow these steps
Manual removal using Safe Mode
Remove 1500dollars ransomware virus when using Safe Mode with Networking
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove 1500dollars using System Restore
Removing the virus with System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of 1500dollars. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove 1500dollars from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by 1500dollars, you can use several methods to restore them:
Data Recovery Pro might recover lost data
This third-party app might be able to restore some of your lost data.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by 1500dollars ransomware;
- Restore them.
Using Windows Previous Version for file recovery
Windows Previous Version is a useful tool that might help to retrieve some files one at a time.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer might be the answer you seek
If the ransomware didn't delete Shadow Copies stored on your PC, then Shadow Explorer might recover some data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryption tool is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from 1500dollars and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Ransomware. FBI. The federal bureau of investigations.
- ^ Julia Sowells. 8 Different Types of Malware. Uscybersecurity. United states cybersecurity magazine.
- ^ Odstranitvirus. Odstranitvirus. Spyware and security news.





















