21btc ransomware (Virus Removal Guide) - Free Instructions
21btc virus Removal Guide
What is 21btc ransomware?
21btc ransomware – a file-locking cyberthreat that appends a complex triple extension to encrypted data
21btc ransomware is a cyberthreat to Windows computers that encrypts files on an infected device and then tries to extort cryptocurrency for a decryption tool. This cryptovirus belongs to one of the most prevalent file-locking viruses families – Dharma ransomware.
While encrypting data, 21btc virus appends an intricate three-part extension that looks like this – appointed unique user ID, criminals' contact email address in brackets [21btc@cock.li], and .21btc extension. All personal files are rendered useless until decrypted.
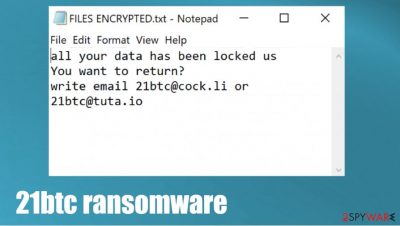
As all cryptoviruses from this lineage, when .21btc file virus is finished with file locking, it creates two kinds of ransom notes – a pop-up window and loads of text files named FILES ENCRYPTED.txt. These messages contain instructions and threats to the victims.
| name | 21btc ransomware |
|---|---|
| type | Ransomware |
| Family | Dharma ransomware |
| ransom note | FILES ENCRYPTED.txt and a pop-up window |
| Appointed file extension | victim ID.[21btc@cock.li].21btc |
| criminal contact details | 21btc@cock.li and 21btc@tuta.io |
| Virus removal | Cyber infections should be removed with reliable anti-malware software that would eliminate them correctly |
| System fix | System repair tools such as the FortectIntego app should be used to undo any damage that the 21btc ransomware virus might cause to system files and settings |
As we've mentioned before, this virus belongs to the Dharma ransomware family, which releases new versions practically every week. Here's a list of a few of the latest variants from this descent:
Ransom notes from this family's ransomware are almost identical. The text files contain mainly two email addresses to contact the criminals – 21btc@cock.li and 21btc@tuta.io. The pop-up window contains the same contact info and some threats to the victims, not to try to rename or decrypt the locked files with any third-party software as that could lead to permanent data loss.
A short message from the FILES ENCRYPTED.txt ransom note:
all your data has been locked us
You want to return?
write email 21btc@cock.li or 21btc@tuta.io
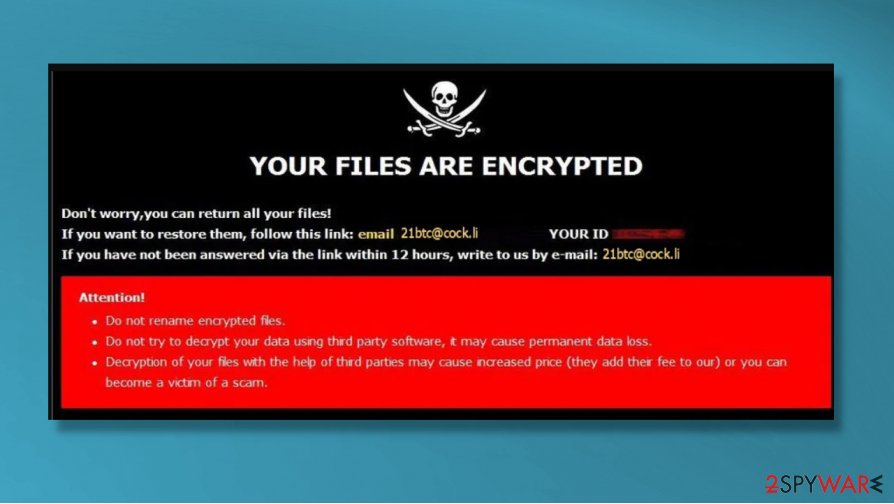
A bit longer note from the creators of 21btc virus in the pop-up window:
YOUR FILES ARE ENCRYPTED
Don't worry,you can return all your files!
If you want to restore them, follow this link:email 21btc@cock.li YOUR ID –
If you have not been answered via the link within 12 hours, write to us by e-mail:21btc@tuta.io
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Victims of cyberattacks should never pay the ransom to the cybercriminals for numerous reasons. First of all, the promised 21btc ransomware decryption key could never be delivered, or the tool could be not operational, as the criminals can never be trusted. Second, the forwarded payment motivates the hackers to expand their operations.
Third, the ransom money could be used to improve ransomware distribution methods. And last but not least, the ransom payments could finance the research of new, more sophisticated malware that would be more stealthy, more invasive, and more hazardous.
Victims shouldn't think for a second to contact the criminals or, even worse – meet the extortion demands. Instead, remove 21btc ransomware from all infected devices with trustworthy anti-malware software like SpyHunter 5Combo Cleaner or Malwarebytes that would do it automatically.
Once 21btc ransomware removal is finished, users should perform a system tune-up. Experts[1] recommend scanning the whole system with a powerful system repair tool such as the FortectIntego to fix any system issues that the file-locking computer threat might have caused.
Learn how to recognize phishing emails to evade one of the most common ransomware spreading techniques
Ransomware can be distributed in many ways, such as remote desktop protocol (RDP) attacks,[2] drive-by downloads, file-sharing platforms, and so on. But our research shows that one of the most common ways cyber criminals use to infect victims' computers with ransomware is phishing emails.

These emails can be carefully and thoroughly constructed to trick their recipients into believing that they're sent from legitimate companies, institutions, or people. But we're here to help, so we've compiled a list of irregularities that could identify a phishing email. If you spot any of these indications then, please don't open any links or download any attachments:
- If you're addressed generally, without your full name
- If you spot grammatical mistakes
- If you detect a bit different companies logos or any other inconsistencies
- If the sender is forcing you to visit their site
- If the sender is pushing you to download some unsolicited attachment
- If the sender is asking for personal information
Tutorial on 21btc virus removal and a quick system fix
There are many types of malware,[3] but all of it should be dealt with accordingly – eliminated with the help of professional anti-malware software like SpyHunter 5Combo Cleaner or Malwarebytes. A reliable anti-virus tool is a must these days because cyberthreats are lurking hidden in many places around the world wide web.
Before 21btc ransomware removal, victims should copy all their encrypted files to removable, offline storage. That is if you didn't keep backups. At the moment, there's no decryption tool available, but law enforcement and private companies are always working on that.
After you remove 21btc ransomware, you should consider performing system repair with powerful system tune-up tools like the FortectIntego app or similar to restore any possible system irregularities that the cryptovirus caused to help it thrive in the infected device.
Getting rid of 21btc virus. Follow these steps
Manual removal using Safe Mode
Obliterate the infection in the Safe Mode with Networking
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove 21btc using System Restore
Delete malware with System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of 21btc. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove 21btc from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by 21btc, you can use several methods to restore them:
Using Data Recovery Pro to retrieve files
Data Recovery Pro app might restore .21btc extension files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by 21btc ransomware;
- Restore them.
Windows Previous Version – a possible feature to recover data
With this feature, users might be able to restore .21btc extension files to their previous versions.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Using Shadow Explorer for data retrieval
This powerful app could restore files from Shadow Volume Copies if they are not deleted by the 21btc ransomware.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryption tools are currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from 21btc and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Bedynet. Bedynet. Spyware and security news.
- ^ Danny Bradbury. Criminals Exploit Pandemic with Brute-Force RDP Attacks. Infosecurity-magazine. Information security and it security news.
- ^ Roger A. Grimes. 9 types of malware and how to recognize them. Cso. Security news, features and analysis.





















