.aesir file extension virus (Improved Instructions) - updated Dec 2016
.aesir virus Removal Guide
What is .aesir file extension virus?
What do we know about .Aesir file extension virus?
.Aesir file extension virus is the latest version of the Locky ransomware, entitled according to the name of an ancient Norse god. Locky creators seem to have grown especially fond of the Norse mythology [1] which is evident by looking at the titles of the latest ransomware variants including Thor, Odin, Loki (Locky), and Heimdall. Talking about Aesir in particular, we should point out that it targets around 456 different file types, and like its preceding versions uses a combination of AES-1024 and RSA-2048 ciphers [2] to render personal files useless. This ransomware kin has proved that its has been created by high-skilled programmers who definitely know how to manipulate complex layers of obfuscation [3] to successfully deliver ransomware to target computers and encrypt the files. What’s new in Aesir virus project is that it uses a different C2 server (89.108.73.124/information.cgi, 185.75.46.73/information.cgi, or 91.211.119.98/information.cgi) and drops a differently titled ransomware note — _[set of chars]-INSTRUCTION.html [4]. When encrypting the data, the virus gets rid of the original filename and replaces it with a random set of characters, and also appends extension “.aesir” instead of the original one. Unfortunately, .Aesir file extension removal is virtually impossible. The files remain encrypted even if it is overwritten manually. So, you should not even bother with that and proceed straight to the virus extermination using proper antivirus tools. One of the trusted software you can apply for this purpose is FortectIntego.
As soon as it encrypts all files, virus develops a .html file (the ransom note), and saves a copy of it to every folder with encrypted data, including Desktop to deliver information about possible decryption options. The ransom note launches via user’s default web browser and displays the classic Locky’s “! ! ! IMPORTANT INFORMATION ! ! !” message, which provides links to Wikipedia’s articles about RSA and AES cryptographic systems, also ones leading to personal ransom-payment site, and instructions on how to download Tor browser, which helps to access them. Finally, Aesir ransomware virus replaces the desktop image with a black picture (-INSTRUCTION.bmp file) featuring text provided in the ransom note.
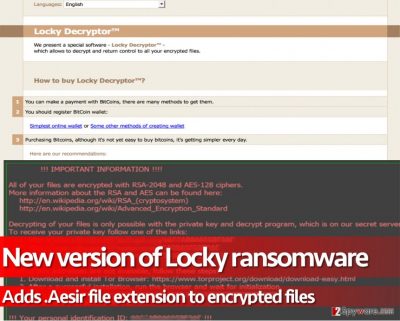
.Aesir ransomware encodes data with with unbreakable encryption, and once files are locked, they’re lost. The criminals working behind this cyber extortion project want victims to pay ransoms in order to receive software that is built based on a secret decryption code that is the only key to data recovery. There is no way to find out this code without criminals’ help, and we can assure you that these scams do not intend to negotiate. They ask to buy certain amount of Bitcoins and send them to their Bitcoin waller to get the Locky decryptor. Instead of taking your hardly-earned money and giving them away to criminals, think whether it’s worth it. You should also take into account the fact that 20% of all ransomware victims who paid the ransom never got their files back because criminals simply refused to provide them with decryption software. You must understand that scammers only care about the money, not about your well-being. Therefore, you should keep your money to yourself and remove .Aesir virus without a doubt.
Ransomware infiltration tactics:
Our analysis shows that .Aesir file extension virus is currently being distributed using new tactics. Recently, we discovered that Nemucod Trojan downloader is currently being distributed via Facebook spam campaign that delivers the bogus photo to victims. The infectious message contains an attachment that is titled as Photo_[4 random numbers].svg. More experienced computer users might quickly notice that the file extension differs from standard image formats (such as JPG, JPEG or PNG) and might refrain themselves from clicking on it. SVG is an XML-based vector image format, which is capable of carrying a JavaScript code. Once the victim clicks on such file, it redirects him/her to a phishing website that looks like Youtube. Here, crooks use the good old “install an extension to view the video” technique to trick the user to install a malicious piece of software. As soon as the victim install the extension, the virus gets access to victim’s Facebook account and uses it for Aesir proliferation – it sends out messages containing Locky’s newest version to all victim’s friends. At the same time, the malicious extension installs Nemucod, which later on downloads and executes Aesir malware.
Obviously, the rest of the Locky virus group programs are still distributed via malicious email spam campaigns. The experts count numerous spam emails with random subject titles that lead to Locky or its versions. Some of them include “Invoice number: 947781”, “New(910)”, “Firewall Software”, etc. Usually, such emails feature convincing messages urging the potential victim to download the attached documents and open them on their computers. It has been recently reported that spam emails with the subject title “Your Amazon.com order has dispatched #[random numbers]” have especially intensified. These emails are delivered to the victims’ computers via fake email accounts, such as auto-shipping4@amazon.com or auto-shipping5@amazon.com and carry a .zip attachment, which should not be opened in any case! It delivers a destructive payload that can take away all personal files away for good. Please bare in mind that types of the attached files may vary and arrive on the computer in .DOCM, .XLS. or other formats [5].
How does .Aesir file extension virus removal work?
.Aesir file extension virus is not one of those mid-level malware examples that are complex but in one or another case decryptable. Frauds who code this virus know what they’re doing and why they’re doing, and they shamelessly attack innocent computer users who surf the world wide web without expecting to encounter anything bad there. We suggest you remove .Aesir file extension virus as soon as you can along with Nemucod and other malware. For that, employ FortectIntego. If you can’t launch your antivirus, run the PC in a Safe Mode with Networking first. This will stop the virus from blocking your anti-malware tool and you will be able to continue with .Aesir file extension removal without any further interferences.
Getting rid of .aesir virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove .aesir using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of .aesir. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove .aesir from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Speaking of Aesir’s antidote, malware analysts remain silent because Locky’s team leave no flaws in the virus’ code, which means that there are no hooks that would allow cyber security experts crack the virus’ code and create an effective decryption tool. Therefore, the only way to recover files is to use a data backup.
If your files are encrypted by .aesir, you can use several methods to restore them:
Data Recovery Pro method
If you wish, you can try this data recovery tool after removing Aesir virus. It might not be able to recover all of the encrypted files, but it might help you to restore some. We highly recommend you to backup encrypted data in case one of the attempts to decrypt files result in failure and corruption of data.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by .aesir ransomware;
- Restore them.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from .aesir and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Norse Mythology for Smart People. Norse mythology site.
- ^ How do RSA and AES differ?. Quora. The best answer to any question.
- ^ Diwakar Dinkar. Locky Ransomware Hides Under Multiple Obfuscated Layers of JavaScript. Securing tomorrow. Today.
- ^ Enter .Aesir – The Newest Variant of Locky Ransomware. Tripwire IT news site.
- ^ Conrad Longmore. Malware spam leads to Locky. Dynamoo's Blog.





















