BBGT ransomware (Virus Removal Guide) - Recovery Instructions Included
BBGT virus Removal Guide
What is BBGT ransomware?
BBGT ransomware – cryptovirus that carries out targeted attacks for maximum profits

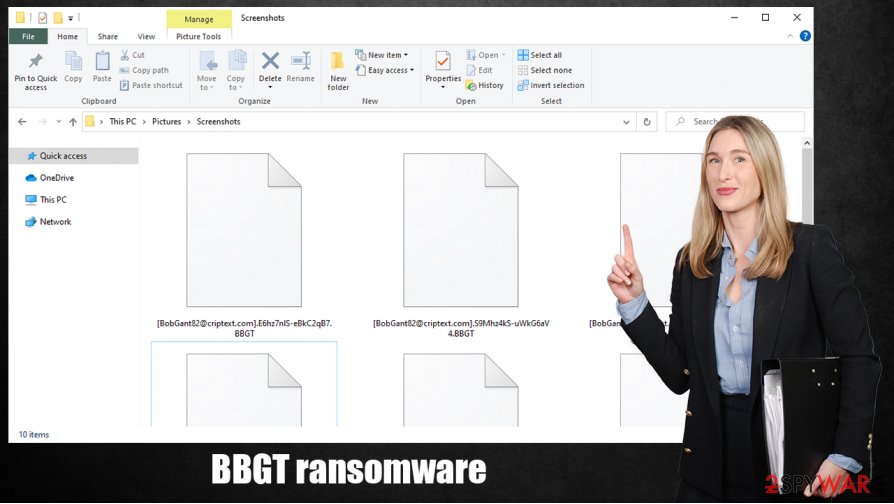
BBGT ransomware is a computer virus that steals some valuable data before encrypting it with military-grade AES and RSA algorithms. Afterward, a ransom note containing instruction, titled BBGT_INFO.rtf, is created and placed along the locked files.
Unlike most other ransomware, when encrypting files, the virus doesn't append an extension to the original filenames – it replaces them with a three-part extension, which consists of the email address of the criminals (BobGant82@criptext.com), a random sequence of 17 characters, and .BBGT extension.
The malware belongs to the Matrix ransomware family, which has been terrorizing companies and everyday computer users since late 2016. Its previous versions include BNFD, SNTG, SCR, and others. Since the attackers are running a double extortion scheme, many victims are more inclined to pay the ransom, even if backups are available.
| name | BBGT ransomware |
|---|---|
| type | Ransomware |
| Family | Matrix ransomware |
| ransom note | BBGT_INFO.rtf |
| Appointed file extension |
Replaces the original file name with [BobGant82@criptext.com], random sequence of 17 characters, and .BBGT extension |
| Additional info | Cybercriminals state that they steal valuable information before encrypting data. If the victims don't start dialog within 48 hours, the criminals will start to publish their files. |
| Criminal contact details | Three emails are provided to start negotiations – BobGant82@criptext.com, BobGant82@yahoo.com and BobGant82@tutanota.com |
| Virus removal | Perform a full system scan and eliminate the infection with reliable anti-malware software |
| System health | Cryptoviruses modify system settings and files. To undo that, use a powerful system repair tool like the FortectIntego app |
BBGT ransomware ransom note message below this paragraph, but we'll summarize it for you. The cybercriminals start by declaring that all files on the victims' devices are encrypted but not corrupted, and that decryption is possible only with their tools. They also state that some of the valuable and confidential information was downloaded to their private servers.
Next, the perpetrators issue a warning that if the victims don't start negotiations by contacting them within 48 hours of the attacks, they will start publishing the stolen confidential data on the internet. If no contact is made within 96 hours, the hackers threaten to attack clients and partners of the victims with ransomware. Moreover, they will try to sell stolen databases to anyone who shows interest.
Then the creators of the BBGT virus explain that the victims aren't random. They are chosen. The assailants state to know that the picked victim can pay the ransom. And then threaten once more by declaring that they will launch DDoS attacks[1] on the victim's website and IT infrastructure.
Afterward, three emails are given to establish contact – BobGant82@criptext.com, BobGant82@yahoo.com, and BobGant82@tutanota.com. Also, a personal ID is appointed. And then a gesture of good faith is shown – free decryption is offered for any three files from the infected machine. Lastly, the developers of the ransomware urge the victims not to waste time and contact them immediately. Any shenanigans will only increase the ransom amount.
All in all, it's a terrifying ransom note, and the victims could feel pressured to meet the demands of the criminals, but we recommend the victims to remove BBGT ransomware instead for a couple of reasons. First, it is illegal,[2] second, if victims pay once, they can pay again so that the cybercriminals might attack you more and more.
The best way to delete any malware, including ransomware, is by using professional anti-malware software. We suggest using time-tested anti-virus apps like SpyHunter 5Combo Cleaner or Malwarebytes for BBGT ransomware removal. Some malware can prevent AV tools from deleting it. In that case, use our guide below on how to do it in Safe Mode with Networking.
When the virus is eliminated from your devices, you're still not out of the woods as many cryptoviruses make alterations to system files and settings to help them accomplish their purpose. To revert all these changes that might impede device performance, cause crashes, and so on, we recommend using the FortectIntego app or a similar system tune-up tool.
The ransom note message displayed in the BBGT_INFO.rtf reads:
Our congratulations. You become a victim of ransomware attack.
First оf аll wе hаvе tо infоrm уоu thаt уоur dаtа is nоt соrruptеd аnd саn bе rеstоrеd quiсklу аnd sаfеlу. Dоn't wоrrу аbоut it. оur sоftwаrе wоrks pеrfесtlу.
Аs уоu саn sее аll уоur filеs wеrе еnсrуptеd аnd rеnаmеd. уоur dаtа is еnсrуptеd with а strоng сrуptо аlgоrithm АЕS+RSА. Уоu саn rеаd аbоut thеsе аlgоrithms in Gооglе. Уоur uniquе dесrуptiоn kеу is sесurеlу stоrеd оn оur sеrvеr аnd nо wау tо rеstоrе уоur dаtа withоut оur hеlp.
Аlsо аll intеrеsting vаluаblе аnd соnfidеntiаl dаtа wаs uplоаdеd tо оur sеrvеrs.
If уоu will nоt stаrt diаlоg with us in 48 hоurs wе will stаrt publishing уоur соnfidеntiаl dаtа in thе Dаrknеt. Аftеr 96 hоurs stоlеn pаrtnеrs аnd сliеnts соntасts will bе usеd fоr nеw rаnsоmwаrе аttасks. Аlsо, If pоssiblе, wе will sеll уоur dаtаbаsеs tо intеrеstеd pаrtiеs.Plеаsе nоtе thаt уоu аrе nоt а rаndоm tаrgеt. Wе knоw thаt уоu аrе аblе tо pау аnd wе will dо оur bеst tо соmplеtе this аttасk with pауing а rаnsоm pауmеnt frоm уоur pаrt. If уоu dоn't gеt in tоuсh, wе will lаunсh а DDоs аttасk оn уоur sitе аnd IT infrаstruсturе.
If уоu rеаllу wаnt tо sоlvе this situаtiоn уоu hаvе tо writе tо оur 3 еmаil аdrеssеs:
BobGant82@criptext.com
BobGant82@yahoo.com
BobGant82@tutanota.com
In subjеct linе please writе уоur ID: –Уоu саn аttасh up tо 3 smаll еnсrуptеd filеs fоr frее tеst dесrуptiоn. Wе will dесrуpt thеsе filеs fоr frее аnd sеnd thеm tо уоu. This will bе prооf fоr уоu thаt wе саn dесrуpt аll уоur dаtа. Plеаsе nоtе thаt filеs must nоt соntаin vаluаblе infоrmаtiоn.
Important!
* Wе аsking tо sеnd уоur mеssаgе tо аll оf оur 3 еmаil аdrеssеs bесаusе fоr vаriоus rеаsоns, уоur еmаil mау nоt bе dеlivеrеd.
* Оur mеssаgе mау bе rесоgnizеd аs spаm, sо bе surе tо сhесk thе spаm fоldеr.
* If wе dо nоt rеspоnd tо уоu within 24 hоurs, writе tо us frоm аnоthеr еmаil аddrеss. Usе Gmаil, уаhоо, Hоtmаil, оr аnу оthеr wеll-knоwn еmаil sеrviсе.Important!
Plеаsе dоn't wаstе thе timе, it will rеsult оnlу аdditinаl dаmаgе tо уоur соmpаnу!
Dоn't trу tо fооl us, it will оnlу inсrеаsе thе priсе!
Wе аrе prоfеssiоnаls аnd just dоing оur jоb!
Wе аrе аlwауs оpеnеd fоr diаlоguе аnd rеаdу tо hеlp!
Investing in cybersecurity pays off
Nowadays, ransomware cyberattacks are a common thing. Some are aimed at specific companies, some target random everyday computer users. We're here to help, so we provide a short tutorial that might help people evade these attacks and stay safe while using their devices connected to the internet.
- Always keep backups. One of the most important things to do is to keep backups of essential data on at least two separate devices, one of which should be offline storage.
- Purchase, constantly update, and regularly use a trustworthy anti-malware application so it could prevent malicious software from gaining access to your device.
- If you have a company, invest in cybersecurity by teaching your employees about phishing emails and other hackers' techniques to attack computers.
- Please install the latest updates available to all software. Whether it's an Operating System or a web browser, all soft must be up-to-date.
Guide to remove BBGT ransomware from infected computers
Ransomware can be aimed at random everyday computer users or specific companies, but either way, it's a nightmare to become a victim of a cyberattack. Although BBGT virus victims are chosen deliberately, it could be modified and distributed to regular people too. So acquire a time-proven anti-malware software like SpyHunter 5Combo Cleaner or Malwarebytes to prevent such attacks.
Instead of meeting the demands of the criminals, all cyberattack victims should focus on BBGT ransomware removal. Manual elimination is possible but requires time and extensive knowledge, so we suggest using the aforementioned anti-malware apps for this task.
When BBGT ransomware and all its components are cleared out, experts[3] recommend performing a full system scan with the FortectIntego tool (or any similar system repair tool) to restore any changes the cryptovirus could have made to the system registry and other core system settings.
Getting rid of BBGT virus. Follow these steps
Manual removal using Safe Mode
Removing BBGT ransomware with Safe Mode with Networking
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove BBGT using System Restore
Infection elimination with System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of BBGT. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove BBGT from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by BBGT, you can use several methods to restore them:
Using Data Recovery Pro for information recovery
This app might be able to recover your data.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by BBGT ransomware;
- Restore them.
File recovery with Windows Previous Version feature
With this Windows function, users could be able to recover .BBGT extension files to their previous versions, i.e., before contamination.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Using Shadow Explorer to retrieve data
This powerful app could restore files from Shadow Volume Copies if the virus didn't remove them.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryptor is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from BBGT and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ George V. Hulme. DDoS explained: How distributed denial of service attacks are evolving. CSO. Security news, features and analysis.
- ^ Raphael Satter. Companies may be punished for paying ransoms to sanctioned hackers - U.S. Treasury. Reuters. Business and financial news.
- ^ Zondervirus. Zondervirus. Spyware and security news.





















