C4H ransomware (Removal Instructions) - Bonus: Decryption Steps
C4H virus Removal Guide
What is C4H ransomware?
C4H is a malicious file-encrypting virus hailing from the Globeimposter ransomware family
C4H is a ransomware-type cyber infection that belongs to the infamous GlobeImposter family. Since 2018, a reduction in the persistence of this ransomware family has been observed up until May 2020 when Petrovic, Russian cybersecurity expert, grasped a virus that encrypts files using .C4H file extension and appends “Decryption INFO.html.”
The ransomware is distributed via trojanized apps, spam emails, or pirated software like cracks. Upon infiltration, it installs Windows boot-up entries, Registry keys, and executables int the Task Manager. Furthermore, it loads an automatic encryption software, which targets non-system files on D: drive and locks them using AES and RSA encryption with the .C4H extension. As a final point, the ransomware generates a ransom note, which presses the victim to contact criminals via chinarecoverycompany@cock.li or chinarecoverycompany@airmail.cc email.
| Name | C4H |
| Geology | GlobeImposter |
| Type | Ransomware virus |
| Extension | .C4H |
| Ransom note | Decryption INFO.html |
| Developer's email | chinarecoverycompany@cock.li chinarecoverycompany@airmail.cc |
| Virus files | 1589462941_QS_pafish.exe or filetype:peexe[1] |
| Distribution | The predecessors of this ransomware tend to spread via Necurs botnet, malicious spam email attachments, pirated software, infected click-to-download ads, and similar. The C4H shows a tendency to mimic its family members |
| Symptoms | The malware initiates a variety of Windows alterations in the first phase. Therefore, errors, terminated AV programs, unresponsive software, crashes, slowdowns, and similar symptoms may be noticed. The second phase encompasses encryption of victim's files and delivery of ransom instructions |
| Decryption | The previous versions of this malware have been deciphered. The free decryption software is still available for people on the NoMoreRansom project. However, the decryptor has been adapted to retrieve file extensions released until 2018, so there is no guarantee that the current .C4H |
| Removal | C4H ransomware removal can be implemented with a professional anti-virus program. There is no other way to get rid of the whole bundle of malicious files. |
| Recovery | The system's recovery after ransomware infiltration is not of less importance. Ransomware removal does not restore damaged system's files and registries, so it's imminent to render a reliable Windows optimization tool. We recommend using FortectIntego |
C4H ransomware and other file-encrypting viruses are used by extortionists who seek financial profit on behalf of other people's misfortune. Criminals engage many strategies to disseminate ransomware payloads and the most “successful” way of tricking regular users seems to be email attachments.
Once the virus finds its place on a target system, criminals engage social engineering techniques to scare victims that the only way to decrypt files is to pay the ransom. For this purpose, C4H virus developers use false claims that running an antivirus program or attempts to self-decrypt files will end up in a permanent loss of encrypted files.
It is not recommended to trust criminals' promises that the C4H decryptor will immediately be provided as soon as the ransomware demand will be received. Paying the ransom poses a high risk of identity theft and other privacy-related issues.
ENGLISH
ALL YOUR FILES AND IMPORTANT DATA ARE ENCRYPTED!To recover data you need decryptor.
To get the decryptor you should:
Send 1 test image or text file chinarecoverycompany@cock.li or chinarecoverycompany@airmail.cc.
In the letter include your personal ID (look at the beginning of this document).We will give you the decrypted file and assign the price for decryption all files
After we send you instruction how to pay for decrypt and after payment you will receive a decryptor and instructions We can decrypt one file in quality the evidence that we have the decoder.
Attention!Only chinarecoverycompany@cock.li or chinarecoverycompany@airmail.cc can decrypt your files
Do not trust anyone chinarecoverycompany@cock.li or chinarecoverycompany@airmail.cc
Do not attempt to remove the program or run the anti-virus tools
Attempts to self-decrypting files will result in the loss of your data
Decoders other users are not compatible with your data, because each user's unique encryption key
The ransom note provides two ways to contact the virus developers, i.e. chinarecoverycompany@cock.li or chinarecoverycompany@airmail.cc. However, instead of disputes with criminals, immediate C4H removal is recommended.
The only way to remove C4H ransomware from the system is to restart Windows into Safe Mode and run a thorough scan with a reputable anti-virus program. Once all malicious entries are removed, you can try to retrieve locked data with a free GlobeImposter decryptor or give a try for alternative recovery methods in case the first one fails.
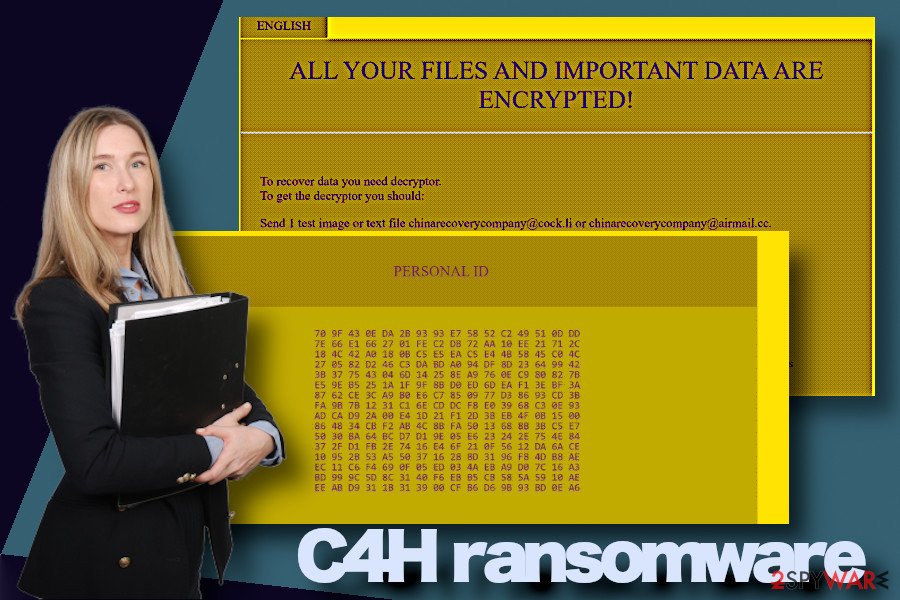
Currently, according to VirusTotal analysis, the C4H virus can successfully be detected and decontaminated by 60 AV engines out of 72. The detection rate is very high, so do not ignore pop-ups of the AV engine if it delivers one of the following warnings:
- Ransom:Win32/GlobeImposter.180910
- Trojan[Ransom]/Win32.GlobeImposter
- Generic.Ransom.GlobeImposter.9F3AF8D5
- TrojWare.Win32.Necne.AB@7l2s58
- Generic.Ransom.GlobeImposter.9F3AF8D5 (B)
- Ransom.GlobeImposter
- Troj/Ransom-EVE
- Mal_FakeGlobe, etc.
If the data on your PC has been encrypted, a ransom note created on the desktop and other folders, desktop background were changed and other signs evidence a ransomware attack, do not postpone C4H removal. Such and similar cyber infections often bear secondary payloads for trojans and spyware. Therefore, the longer you keep an intruder on the system, the higher the danger gets.
Strategies that criminals use to spread ransomware
Our colleagues from LosVirus.es[2] warn users about various insecurities online that can help ransomware to get inside the system. In many cases, ransomware viruses are launched as second payloads of trojans, which usually get installed after vulnerability exploits or pirated software. However, the most infamous online places where people encounter the highest risk to get a ransomware infection are email accounts (spam section), torrent websites, questionable gaming websites, or adult content (gambling, porn) websites.
Apart from having a powerful AV engine with real-time protection enabled, there are other precautionary measures that people should render to stay away from file-encrypting and other malware:
- Manage your email with extreme carefulness. Do not rely on email messages that fall into the spam section. The biggest danger hides under messages that carry attachments or links.
- Avoid visiting unprotected websites and secondary networks. Poorly protected third-party websites can easily be exploited by criminals and infected with malicious ransomware code.
- Avoid visiting adult-content websites. Although there are some potentially secure porn websites[3], clicking on shady ads positioned on those sites poses a risk of being redirected to a phishing website.
A combination of precaution and powerful anti-virus program should be enough to protect your personal information, software, identity, and money from violations.
C4H ransomware elimination and data recovery guidelines
C4H ransomware removal process is implemented by both regular users and skilled users in the same way – a full scan with a professional anti-virus program is required. Manual removal is not possible in any way and any attempt to change malicious files can put the system at risk.
Before you take any actions to remove C4H ransomware, we strongly recommend making the backups of the locked files. That's a measure to ensure that you'll have copies in case the virus gets removed alongside files with .c4h file extensions. For that, you can use a USB flash drive or cloud storage.
Once ready, restart Windows into Safe Mode with networking as explained below, and launch the scanner of your AV tool. A professional tool will detect all ransomware-related entries, processes, and registries that have to be terminated together to successfully finish the C4H removal. For a full system check, we recommend using SpyHunter 5Combo Cleaner or Malwarebytes tools.
Finally, do not forget to fix virus damage. Ransomware affects the Windows system severely and, unfortunately, AV programs cannot fix system damage. For that, use a tool like FortectIntego.
Getting rid of C4H virus. Follow these steps
Manual removal using Safe Mode
Restart Windows into Safe Mode with Networking to terminate all malicious processes triggered by C4H ransomware.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove C4H using System Restore
The System Restore function on Windows can help with the C4H removal and retrieval of encrypted data.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of C4H. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove C4H from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts..C4H extension files can be encrypted with the help of third-party data recovery tools or a free decryptor that has been designed for the previous versions of this cyber infection.
If your files are encrypted by C4H, you can use several methods to restore them:
Use Data Recovery Pro to retrieve some of the compromised files and documents
Files encrypted by C4H ransomware virus can be recovered with the help of third-party software. However, successful decryption is possible when a process is performed step-by-step as shown below.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by C4H ransomware;
- Restore them.
Windows Previous Versions can be of use when dealing with ransomware encrypted files
This software can be used to restore some files affected by file-encrypting malware. However, this option is only available when a System Restore feature was enabled on the system before.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Take advantage of the Shadow Explorer
In case C4H ransomware fails to remove Volume Shadow Copies of the data stored on the system, most of the files can be retrieved by following these steps:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
C4H ransomware decryption software hasn't been developed yet
Despite the fact that there's no official C4H decrypter, you can give a free GlobeImposter decryption software a try since both viruses stem from the same family.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from C4H and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ peexe. VirusTotal. Fee file and URL scanner.
- ^ NOTICIAS SOBRE SEGURIDAD Y VIRUS. LosVirus. Virus and spyware news.
- ^ LAUREN L'AMIE and TAYLOR ANDREWS. 10 Women-Friendly and Computer-Safe Porn Websites. Cosmopolitan. Female-focused millennial media.







