Chinadecryption2021 ransomware (virus) - Recovery Instructions Included
Chinadecryption2021 virus Removal Guide
What is Chinadecryption2021 ransomware?
Chinadecryption2021 ransomware is a computer infection that locks your files and asks you to pay ransom for their return
Chinadecryption2021 is a virus that one could get infected with without expecting it at all – malware is distributed in ways that allow stealthy infiltration. Once inside a Windows computer, it changes the way it operates by modifying certain settings, dropping malicious files, creating directories, etc. However, this is not the main goal of attackers, as these modifications are done for one and sole purpose – to lock all personal files on the device and networks.
The encryption process of pictures, videos, documents, or other files is performed with the help of a powerful encryption algorithm (usually, AES),[1] which makes all the data unreadable. In essence, files are locked behind a complex password that is generated for each of the users individually, making it impossible to replicate the decryption process of another victim. At this time, all the files are marked with .chinadecryption2021.[ID], extension, and can no longer be opened.
The data locking process is usually very quick unless the number of files on the system is very large; this makes interrupting the process rather difficult. It is important to note that the data is not corrupted and requires a unique key in the possession of cybercriminals. For obvious reasons, they are not willing to provide it for free.
The attackers state all their demands within a ransom note titled “!!! ALL YOUR FILES ARE ENCRYPTED !!!.txt,” the attackers state all their demands. They claim that the only way to restore files is to pay a ransom. While the sum is not stated, it is clear that Bitcoin should be used when paying – criminals use digital currency because it provides them anonymity and multiple other benefits.
We strongly advise against paying, as there is no guarantee that hackers will keep their promises. Instead, you could take a different approach and try to restore your data using alternative methods. Note that this is not always possible, as it depends on various factors on an individual level.
| Name | Chinadecryption2021 ransomware |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| Family | Zeppelin |
| File extension | All the personal files are appended with .chinadecryption2021.[ID] extension; the ID is generated for each of the victims individually |
| Ransom note | !!! ALL YOUR FILES ARE ENCRYPTED !!!.txt |
| Contact | chinadecryption2021@goat.si and chdecryption2021@tfwno.gf |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| removal | Perform a full system scan with SpyHunter 5Combo Cleaner or another reputable security software |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
Why you should avoid paying
Some malware is designed to be stealthy – it runs in the background without emitting any symptoms and even sometimes bypasses security measures implemented on the machine to remain there as long as possible. The most known types of malware that employ these tactics are Trojans designed for stealing sensitive information. Likewise, rootkits[2] might be employed by criminals to hide the presence of malware.
That being said, Chinadecryption2021 and any other ransomware only hide itself before it finishes the file encryption process. After that, it is in the attackers' best interest to make users aware of what happened to their computers and personal data. For this purpose, ransomware is programmed to generate a predetermined ransom note, which might sometimes pop up as a program window, although, in most cases, a simple text file is employed.
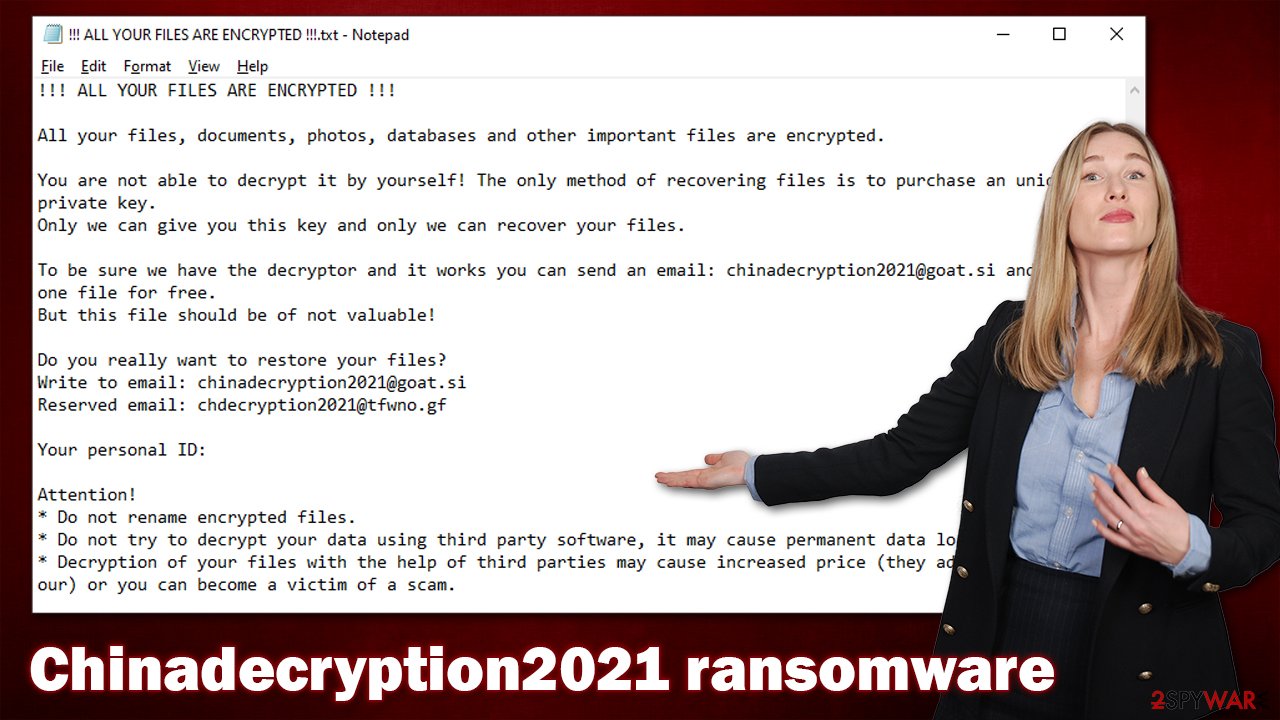
In this case, a ransom note !!! ALL YOUR FILES ARE ENCRYPTED !!!.txt is placed on users' desktops, as well as all directories where affected files are located. The exclamation marks within the name also help the note to stay at the very top of all the other files, making it more noticeable. Here are the contents of the note:
!!! ALL YOUR FILES ARE ENCRYPTED !!!
All your files, documents, photos, databases and other important files are encrypted.
You are not able to decrypt it by yourself! The only method of recovering files is to purchase an unique private key.
Only we can give you this key and only we can recover your files.To be sure we have the decryptor and it works you can send an email: chinadecryption2021@goat.si and decrypt one file for free.
But this file should be of not valuable!Do you really want to restore your files?
Write to email: chinadecryption2021@goat.si
Reserved email: chdecryption2021@tfwno.gfYour personal ID:
Attention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third party software, it may cause permanent data loss.
* Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
It does not differ much from any other ransom notes that are used by other ransomware strains. Cybercriminals explain that all the files on the system have been locked, and they are willing to provide a decryption tool for a fee. They also claim to provide a free test decryption service, which would allegedly convince users that recovering files using threat actors' decryptor is possible.
However, this is a mere trick. There have been plenty of instances where users were provided with sample decryption but later did not receive the key that would unlock all personal files. In other words, you can never trust cybercriminals, as they do not care about the well-being of their victims. Without a doubt, it is not a rule but keep in mind that you might not only lose your files but also money. Instead, we recommend going an alternative route. For that, refer to the information we provide below.
Things to do before you start Chinadecryption2021 ransomware removal
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). However, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works.
IMPORTANT for those without backups! →
If you attempt to use recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them.
Before you proceed with the removal instructions below, you should copy the encrypted files onto a separate medium, such as a USB flash drive or SSD, and then disconnect them from your computer. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices.
It is important to do this in Safe Mode, as malware could be potentially spread to the external device. To reach Safe Mode, follow these steps:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

Once here, insert a storage device and move over your most important files. Without a doubt, if you have working backups you could restore your files from, you can skip this step.
Step 1. Use security software
It is very important to use security software for Chinadecryption2021 virus removal. While there is a chance that malware would delete itself after data encryption is complete, there is no guarantee that additional modules would not be present on the machine. For example, Djvu variants Zaps, Maql, and many others, were found dropping data-stealing components that would steal passwords and other sensitive information when browsers are used.
Likewise, if any type of malicious software has compromised your system, there is always a chance that it came in bulk. Infection weakens the initial protection of systems implemented in Windows to repel other threats. As a result, there could be data stealing or another type of malware running in the background.
After you make backups of the encrypted files, you should immediately scan your device with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful security software. This would ensure that all the malicious components are eliminated from the device automatically. While it is possible to delete ransomware manually, it requires excessive IT knowledge and is not a recommended practice for home users.
Step 2. Alternative file restoration methods
Many users, once they realize that their files have been locked, fall into a straight-out panic – their documents for school or work can no longer be opened. At this point, victims believe that their files have been damaged and are not recoverable. While it is true that the attackers have the decryption key (although this might not always be true) that would be able to restore all the encrypted files, paying them is very risky.
There are also people who believe that security software can restore the .chinadecryption2021 files after malware is removed. Unfortunately, this is not the case at all, and after its elimination, data will remain locked. This is precisely why ransomware remains one of the most devastating PC infections out there. To prevent this from happening, make sure you always have working backups of your most important files – we provide details on how to create them below.
So, what choices do you have? Paying crooks is risky, but you also want your files back. We would recommend you try using recovery software which can, under certain circumstances, be successful in the recovery process.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Another way to recover the encrypted files is to wait for a free decryptor from security experts. There are plenty of examples where researchers managed to find bugs[3] within the ransomware code, which allowed them to create a free decryption tool. Alternatively, law enforcement agencies might capture the remote servers controlled by the attackers, which would make all the unique keys available to victims. Here are a few links you can use to look for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors
Step 3. Fix damaged system files
Finally, you should take care of your computer health. Malware is a complex program that uses sophisticated methods to bypass built-in protection and change the way Windows operates. During the infection period, some system components can be inadvertently damaged, which might cause some software or computer to crash or return errors. This is particularly common after malware is deleted from the infected system, as anti-virus cannot repair damaged system files.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it can also remove malware that has already broken into the system thanks to several engines used by the program. Besides, the application can also fix various Windows-related issues caused by malware infections, such as Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

Below, you will also find more information on how to back up your files correctly to avoid future ransomware attack consequences. Keep in mind that anti-malware software, such as SpyHunter 5Combo Cleaner or Malwarebytes, remains your primary defense mechanism against incoming attacks.
Getting rid of Chinadecryption2021 virus. Follow these steps
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Josh Lake. What is AES encryption and how does it work?. Comparitech. Tech researched, compared and rated.
- ^ What is Rootkit?. Trend Micro. Security definition.
- ^ Software bug. Wikipedia. The free encyclopedia.
