2021 update. COM surrogate virus: check for corrupted files
COM surrogate virus Removal Guide
What is COM surrogate virus?
COM surrogate virus is the malware that alters various settings and hides its purpose behind Windows processes

COM surrogate virus is a malicious version of the Component Object Model[1] – a legitimate file used by the Windows operating system that usually runs in the background and is related to the dllhost.exe. While the initial functionality of COM is to allow the creation of COM objects used by Windows, the file that is disguising under the same name is here for much more malicious purposes.
Since 2015, hackers have started camouflaging this process to disguise malicious Trojan horses[2], such as Trojan.Poweliks. According to reputable security vendors, a more precise name for this malicious process is Dllhost.exe 32 COM surrogate virus. The infiltration of such treats might reveal sensitive information about users and even allow hackers to steal money directly from a bank account.
Masking malicious executables by using Windows legitimate names is not a new tactic, as hackers are merely trying to mislead users to make them think that the virus is just another harmless process. In reality, any executable can be replaced, duplicated, or corrupted by malware. To separate malicious executables from legitimate processes, users should run a scan with security software and check the file's location (it should be C:\Windows\System32).
| Name of the virus | COM surrogate virus |
|---|---|
| Type of malware | Trojan |
| Danger level | High. Trojans can steal personal information, such as credit card details or login information, open a backdoor to other cyber infections, allow hackers to connect to the PC remotely, etc. |
| Related files | Dllhost.exe |
| Error message displayed | “COM surrogate has stopped working” |
| Symptoms | Multiple processes running in Task Manager, high disk usage or CPU consumption, system slowdowns, program crashes, etc. |
| Removal options | Manual Trojan removal is hardly possible. You should use trustworthy anti-malware software instead |
| Recovery | Use FortectIntego to recover from the infection damage |
Many Windows users are looking for an answer to the question is this a virus or not. In fact, the answer is simple – the former COM surrogate is not a virus. On the contrary, it's one of the crucial Windows OS files that should not be removed under any circumstances.
However, criminals can disguise Trojan under the fake copy of the COM surrogate virus process. In fact, the ability to conceal itself under the name of a legitimate Windows process is a key feature of the Trojan. If you happen to find it in your Task manager, don't hesitate and remove it from the system.
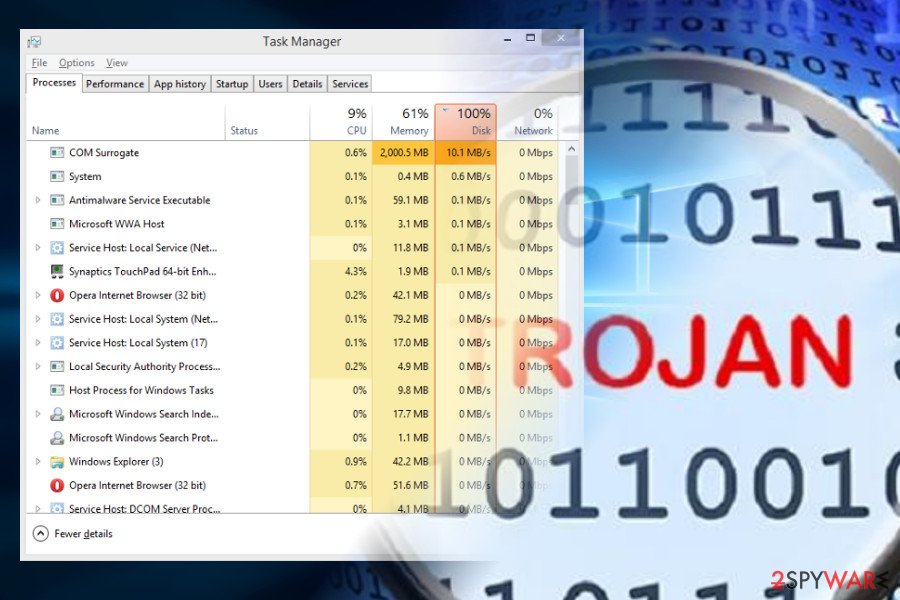
COM surrogate virus peculiarities
Just like many other Trojan horses[3], COM surrogate virus can be used for a long list of malicious activities, such as stealing personal information and other data which is considered sensitive. Besides, this malware can be used to help other viruses infiltrate the system, allow remote code execution, and used for many other purposes.
You should immediately check your computer using reputable anti-spyware if you suspect that it is infected with a virus. Typically, affected systems start working slower than previously, tend to crash, use an excessive amount of RAM or CPU.
Besides, you might have problems when using Microsoft Office programs, Notepad, or other applications. Finally, pay attention to suspicious programs showing up on your PC, and interrupting your browsing sessions. They can also be considered as one of the signs showing that the system is infected with a virus.
However, you should also note that these problems can be caused by many different computer viruses[4]. Though, if you can find strange and unknown processes running in the Task Manager, you should think about COM surrogate virus removal. Take our advice and scan your PC with reputable anti-malware software. Once you get rid of the virus, scan your device with FortectIntego to repair the damage done and bring your system back to normal.
Ways to distinguish between a real and fake COM surrogate
Please, do NOT mix this entry with Dllhost.exe COM surrogate which is a critical system process used for hosting some of Windows operating system services and processes. Typically, this interface gives the ability for the developers to create COM objects that attach themselves to various programs and extend them.
Thus, due to its specific and diverse purpose, users cannot recognize it and often confuse between the original file and the virus files. To spot a malicious Trojan horse that just impersonates a legitimate process dllhost com surrogate, you should pay attention to these tips:
- Depending on the version of the Windows OS, the original file should be located in c:\windows\system32 or c:\winnt\system32 directories;
- The virus is using a tremendous amount of your CPU power or memory while the necessary process' usage is significantly lower;
- A large number of dllhost.exe *32 operating in the Task Manager is also an indication that your computer is infected with a virus.
The COM object is used to generate thumbnail images of files in the folder and many other at first sight intangible processes. Due to this functionality, users are sometimes presented with “COM Surrogate has stopped working” error which means that they need to double-check display drivers, renew codecs, temporarily turn off anti-virus software, check the disk for errors, etc.[5]
It seems like the problem usually occurs when browsing pictures or trying to view a video, although some reported cases are also related to printing. Nevertheless, the legitimate process is supposed to help you view thumbnails of the files and, if the service fails, users encounter “COM Surrogate has stopped working” error.
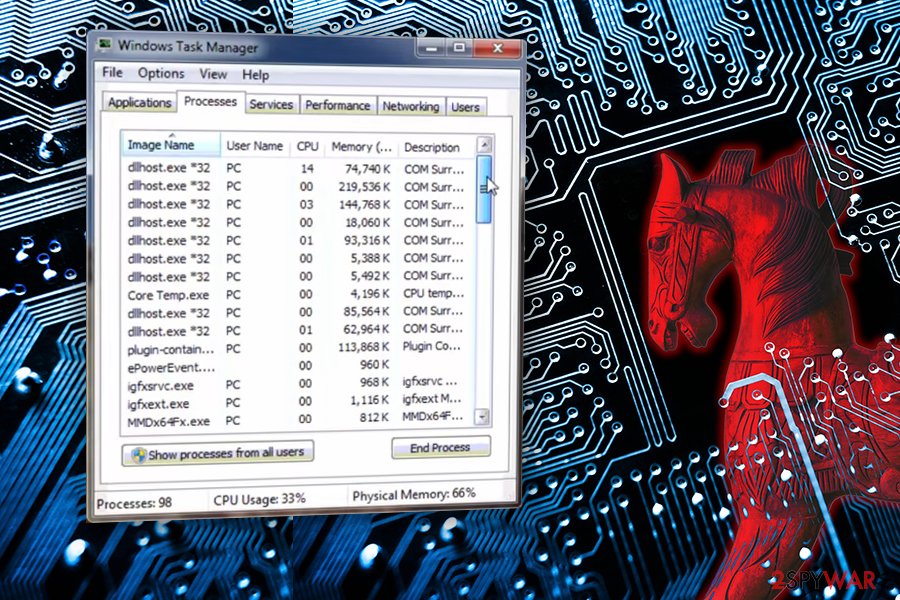
However, If you got infected with the malware that obfuscates this activity, you should not try to stop it on your own. You may end up removing essential files and cause severe damage to your computer.
For this reason, you have to employ antivirus or anti-malware software, and let your preferred software remove COM surrogate virus from the computer.
Trojan version spreads via rogue websites
Developers of the malicious process distribute it via malicious websites that might promote fake updates of regal applications. Thus, users are lured into unconsciously downloading the infected file instead of by the delusional look of it. Moreover, you should avoid illegal downloads since crooks often use them to spread trojan and other high-risk computer infections.
If that is not enough, Lesvirus.fr[6] analysts noticed that some victims got infected via spam e-mail messages sent under the name of DHL or FedEx shipping company. The subject line stated that it failed to deliver a package and submitted an attachment with further details. Once the user opened an attachment, the Trojan infiltrated on the computer and started its malicious activity.
Thus, if you want to stay safe, you should start avoiding illegal websites, ignore suspicious emails[7], never download their possibly infected attachments and also close all misleading ads[8] that may show up on your way while browsing the web.
If an advertisement is offering you to update your Flash Player, FLV Player, or similar program, you should close it. If you have any doubts that you need to update these programs, you should visit their official websites. As we have already said, you should never leave this particular virus on your computer. If you have even the smallest doubts about it, please use our tips below and fix your computer.
Terminate COM surrogate virus by using anti-malware software
You should employ reliable security software to remove the virus if you want to protect your confidential data like bank logins, credit card details, passwords, and similar information.
Remember that if you get rid of the original Windows file, you might completely damage your operating system, thus do not try to eliminate it by yourself. That's why manual COM surrogate removal is not advisable.
To avoid making unnecessary mistakes, download a robust anti-malware and run a full system scan with it to remove COM surrogate virus from the system. In case the Trojan blocks the anti-virus scanner, follow these steps to fix that:
Getting rid of COM surrogate virus. Follow these steps
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from COM surrogate and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting trojans
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Component Object Model. Wikipedia. The free encyclopedia.
- ^ The Effects of the Trojan Horse Virus. Techwalla. Tech Articles.
- ^ Andra Zaharia. The Top 10 Most Dangerous Malware That Can Empty Your Bank Account [Updated]. The Heimdal Security Blog. The blog about online security and malware.
- ^ Neil J. Rubenking. 7 Signs You've Got Malware. PC Mag. Technology Product Reviews, News, Prices.
- ^ Gabriel E. Hall. How to fix “COM Surrogate has stopped running” error. UGetFix. Fix any computer related issue.
- ^ LesVirus. LesVirus. Malware Removal Guides.
- ^ Charlie Osborne. The five most dangerous email subjects to watch for. ZDNet. Technology News, Analysis, Comments and Product Reviews.
- ^ Hilary Tuttle. The Rise of Malvertising. Risk Management. The Official Website of a Multi-national Insurance and Reinsurance Consulting Organization.
