CommonValue Mac virus (Free Guide)
CommonValue Mac virus Removal Guide
What is CommonValue Mac virus?
CommonValue is a malicious Mac app that can insert other malware and steal your personal data
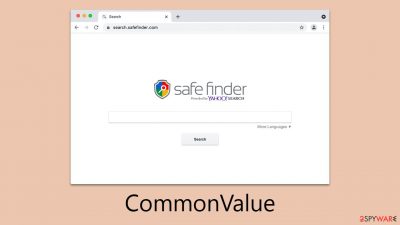
CommonValue is a prevalent Mac virus that has been circulating on the internet, affecting a substantial number of users globally. It is a part of the Adload malware family, known for its active presence since its initial detection in 2017. The virus does not spread autonomously, but users often inadvertently install it through various deceptive tactics employed by its developers, including fake Flash Player installers.
Upon installation, CommonValue introduces a browser extension to web browsers like Safari, Chrome, Firefox, and others. This extension is central to its malicious activities, which typically include altering the user's homepage, new tab settings, and default search provider, though these modifications can vary with different versions of the virus.
The primary purpose of these changes is to facilitate the display of sponsored links and advertisements, thereby generating revenue for the virus's creators. Furthermore, the extension is designed to harvest personal information, including account and credit card details.
The impact of this malware is significant, as it alters system configurations and inserts its components without user consent. It can also download additional harmful payloads, escalating the risk to the system. Given its potential threat to both personal privacy and computer security, it is crucial to remove CommonValue from affected Macs promptly.
| Name | CommonValue virus |
| Type | Mac virus, adware, browser hijacker |
| Malware family | Adload |
| Distribution | Fake Flash Player installers or bundled software from malicious sources |
| Symptoms | Installs an extension to the browser that can not be deleted easily; changes homepage/new tab to Safe Finder, Akamaihd, or something else; redirects lead to potentially malicious or scam sites, promotes suspicious software, etc. |
| Removal | The easiest way to remove Mac malware is to perform a full system scan with SpyHunter 5Combo Cleaner security software. We also provide a manual guide below |
| Other tips | PUAs and malware often leave traces within web browsers – cookies, for example, are used for tracking. You should get rid of these leftovers with FortectIntego or employ our manual guide |
Distribution methods and avoidance techniques explained
CommonValue Mac virus, a variant of the Adload malware family, predominantly spreads via two effective strategies: counterfeit Flash Player updates and unauthorized software installers. These methods are simple yet highly effective, contributing significantly to Adload's reputation as a prevalent type of Mac malware.
The first method employs bogus Flash Player updates. Cybercriminals exploit the legacy of Adobe Flash Player as a deceptive hook – it was formerly irreplaceable software for media content. Users are frequently misled into downloading and installing these “updates,” which are, in fact, malicious files that act as a gateway for the CommonValue virus. These fraudulent updates are commonly encountered by users through pop-up notifications on compromised websites.
The second distribution route involves illegal software installers. Found on unofficial, third-party websites, these installers offer free downloads of popular software but are often bundled with hidden malware. Many users, unaware of the risks, download and install these applications, inadvertently allowing malware like CommonValue onto their systems.
The effectiveness of these distribution methods is grounded in several key factors:
- Both tactics exploit users' trust in familiar software (such as Adobe Flash Player) or their desire for free access to well-known applications.
- A significant portion of users lack awareness about the dangers of downloading updates or software from non-official sources.
- Many users do not have robust anti-malware defenses on their systems, making them more vulnerable to malware attacks.
The proliferation of CommonValue and other members of the Adload malware family is largely dependent on these deceptive distribution techniques and the vulnerabilities of users. Understanding and being aware of these methods is essential for users to effectively protect themselves against such cyber threats.
Adload is one of the most common Mac infections out there
The increasing popularity of Macs has dispelled the myth that they are immune to malware. In recent years, there has been a significant surge in malware attacks on Macs, garnering the attention of cybercriminals throughout the world.
While Macs are less vulnerable to more serious forms of malware like rootkits and ransomware, they are increasingly plagued with adware issues. Notably, adware for Macs is more obtrusive and aggressive than that for Windows systems.
Adload adware, which has been aggressively corrupting Mac users for over a half-decade, is an excellent example of this tendency. CommonValue is one of the more aggressive adware variants among the growing array of threats to Mac users.
Adload is easily identifiable by its distinct icon, featuring a magnifying glass set against backgrounds of varying colors such as blue, teal, green, or gray. The presence of an app or extension bearing this icon is a strong indication of an Adload malware infection.
Despite exhibiting some minor variations across its versions, Adload consistently upgrades its methods to evade detection. Once it gains access to a system, it uses AppleScript to bypass Gatekeeper and XProtect, which are integral security features of the Mac operating system.
This maneuver allows Adload to add extensions and other components with high-level permissions, facilitating the unauthorized collection of personal data and downloading of further malicious payloads. Consequently, it's not unusual to find multiple variants of malware on a single Mac, complicating its removal process. Due to its tenacious nature, eradicating it can be challenging, but following the steps outlined below can lead to successful removal.
Removing the threat and cleaning the browser
CommonValue virus removal requires a more intricate approach than simply moving the application to the Trash. This is because it is engineered to operate with administrator privileges and carries out a range of invasive actions such as dropping files into vital system areas, creating new user profiles, and adding login items.
Given its complex nature, it is advisable to use robust security solutions for its effective elimination. Tools like SpyHunter 5Combo Cleaner or Malwarebytes are recommended, as they are specifically designed to tackle such advanced threats and are not affected by limitations that may hinder the Mac's built-in anti-malware capabilities. These security apps can automatically identify and remove all components of the malware efficiently.
For those who opt for manual removal, it's essential to proceed with caution. Undertaking manual steps does not assure complete eradication of the malware, especially since there might be concealed payloads actively running in the background, executing harmful tasks discreetly.
If proceeding manually, the first critical step is to terminate all background processes related to CommonValue via the Activity Monitor. This action is vital to prevent these processes from obstructing the removal procedure. It's important to be thorough in this step to ensure that no part of the malware remains active during the removal process.
- Open Applications folder.
- Select Utilities.
- Double-click Activity Monitor.
- Here, look for suspicious processes and use the Force Quit command to shut them down.
- Go back to the Applications folder.
- Find the malicious entry and place it in Trash.
![Uninstall from Mac 1 Uninstall from Mac 1]()
To effectively remove the malware from your Mac, you need to address two critical components that it manipulates: Login Items and Profiles. Both play a significant role in the persistence and functionality of the malware.
- Go to Preferences and pick Accounts.
- Click Login items and delete everything suspicious.
- Next, pick System Preferences > Users & Groups.
- Find Profiles and remove unwanted profiles from the list.
Finally, you should get rid of Launch Daemons and other configuration data left by malware. Proceed with the following:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and delete all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
When dealing with Adload variants, which typically comprise a primary component and a browser extension, manual removal requires specific attention to the browser extension. This add-on is particularly concerning as it's designed to track personal data, including credit card details and passwords.
Another important task here is to make sure that the browser's cookies and other data are removed from the system, as the virus can continue its tracking activities. For a quicker process, you can always employ FortectIntego maintenance and repair software. Alternatively, follow the instructions below to do this manually.
Getting rid of CommonValue Mac virus. Follow these steps
Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.












