CoordinatorOptimization Mac virus (Free Guide)
CoordinatorOptimization Mac virus Removal Guide
What is CoordinatorOptimization Mac virus?
CoordinatorOptimization – a dangerous Mac virus that can spy on your personal information
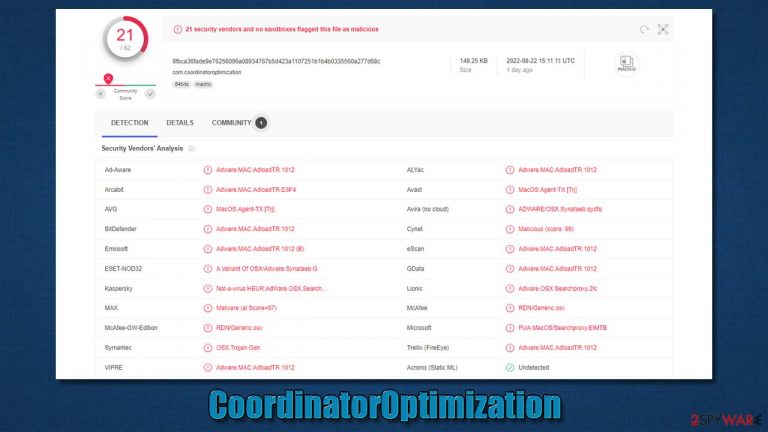
CoordinatorOptimization Mac virus is a member of the notorious Adload malware family. Just like its predecessors, it is designed to hijack[1] your browser and redirect you to malicious websites. It can also be used to collect your personal information and sell it to malicious parties on underground forums. In order to protect your Mac from this virus, you need to remove it as soon as you can.
Unfortunately, CoordinatorOptimization is not that easy to eliminate, as it consists of several components and uses a variety of persistence mechanisms. Thus, if not deleted correctly, the malware may return and continue its malicious deeds. Below we will provide all the required information about the virus and how to effectively get rid of it for good.
| Name | CoordinatorOptimization |
| Type | Mac virus, adware, browser hijacker |
| Malware family | Adload |
| Distribution | Fake Flash Player installers or bundled software from malicious sources |
| Symptoms | A new extension is installed on the browser, along with an application of the same name; search and browsing settings altered to an alternative search provider; new profiles and login items set up on the account; intrusive ads and redirects |
| Removal | Although not recommended to novice users, manual elimination of Mac malware is possible. We recommend performing a full system scan with SpyHunter 5Combo Cleaner and removing all the malicious components automatically |
| Security tips | For best performance and system remediation, employ FortectIntego. Also, cleaning web browser caches is highly advised after the elimination of malware for better privacy and security |
Adload family traits and features
Adload is among the most prominent Mac malware strains out there and has been around since at least 2017. Since that time, hundreds of variants have been released by cybercriminals behind it, and we have covered numerous of them on our website – UniversalSearchConsole, VictorSurge, LivingAware, and PlatformFormat are just a few of them.
Distribution
CoordinatorOptimization is spread in the same way as other malware of this family: through fake Flash Player update prompts and installers for pirated software. Obviously, people never choose to install it themselves and are rather tricked into doing so.
Once a popular technology for viewing web-based multimedia content, Flash Player is now outdated and no longer used. In fact, Adobe has discontinued the plugin. All modern web browsers have replaced the need for Flash Player by embedding its functionality within the browser.
Another popular Adload distribution method is cracked software. High-risk websites that offer illegal installers for well-known applications and video games are frequently utilized to entice people into installing malware. The ideal approach is never to download anything from such websites but instead buy a genuine license to use the program.
Operation
In essence, CoordinatorOptimization is an adware-type application, as it installs the browser extension in Safari (or another used browser), which guarantees that users are exposed to a steady flow of ads. Since adware and malware distributors are known for associating with rogue advertisement networks,[2] which results in ads being of poor quality (often malicious).
The worst thing about this is that the extension has elevated permissions and can steal sensitive information such as credit card numbers or passwords that are entered into the browser. As a result, having an extension installed on the system poses a major privacy risk.
Persistence
The virus is spread through dubious means, but the user has to input their Apple ID before being able to install the application. With this permission granted, the virus uses several exploits to root itself within the system. For example, AppleScript is commonly used to make changes to the infected systems, and new Login Items, Profiles, Plist files, and other items are created automatically. Thanks to all these features, malware successfully avoids detection by Mac's built-in defense systems.[3]
CoordinatorOptimization removal explained
When it comes to CoordinatorOptimization, the best way to remove it is with anti-malware software. This will ensure that all of the malicious files and changes made by the malware are removed from your system. Additionally, using anti-malware software will protect you from future infections by keeping your system up-to-date with the latest security patches.
If you are looking for a reliable and effective anti-malware solution, we recommend using SpyHunter 5Combo Cleaner or Malwarebytes. These apps can quickly and easily find all the malicious items and get rid of them for you within just a few minutes. Alternatively, you can opt for manual elimination, although we recommend cleaning browser caches regardless of which method you choose.
Get rid of the main app and its components
To fulfill its malicious deeds, Adload runs background processes at all times – these are launched immediately after the system is booted. To prevent issues with removal, you should find these processes and terminate them:
- Open Applications folder
- Select Utilities
- Double-click Activity Monitor
- Here, look for suspicious processes and use the Force Quit command to shut them down
- Go back to the Applications folder
- Find the malicious entry and place it in Trash.

Upon infiltration, malware might establish new User profiles and Login items for persistence. This might be the reason why you can't get rid of the app or the extension.
- Go to Preferences and select Accounts
- Click Login items and delete everything suspicious
- Next, pick System Preferences > Users & Groups
- Find Profiles and remove unwanted profiles from the list.
Next, you should take care of the previously-mentioned Plist files and login items.
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and delete all the related .plist files.

Clean your browser
As soon as the CoordinatorOptimization virus is installed, a browser extension is inserted into Safari or another used browser. This appendage would result in changes to the homepage and a new tab function, thereby exposing users to sponsored links or ads.
The extension that uses the magnifying glass icon is what you need to remove in order to restore your browser's functionality and regain control of it. Keep in mind that this may or may not be achievable depending on the virus' persistence mechanisms. If it doesn't work, move on to the next section.
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

If you were unable to uninstall the extension in a regular way, you can reset Safari instead. It is easy to do:
- Click Safari > Preferences…
- Go to the Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

Your last task is to clean the browser caches of Safari. Note that you don't have to do it manually if you employ the FortectIntego maintenance utility, it can quickly and easily get rid of various junk files and trackers.
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

If you are using Google Chrome or Mozilla Firefox browser, proceed with the instructions below.
Getting rid of CoordinatorOptimization Mac virus. Follow these steps
Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Browser hijacking. Wikipedia. The free encyclopedia.
- ^ Zeljka Zorz. How does a rogue ad network function?. Help Net Security. Cybersecurity News.
- ^ Phil Stokes. How AdLoad macOS Malware Continues to Adapt & Evade. SentinelOne. Security research blog.
