Drive by Exploit email (Easy Removal Guide) - Free Instructions
Drive by Exploit email Removal Guide
What is Drive by Exploit email?
Drive by Exploit email is a scam that threatens to expose compromising material about the user after an alleged computer hack
Drive by Exploit is is a term that was incorporated in a recent money extortion scam campaign, and the email author claims that the computer owner was infected with malware using this technique. However, the term, strictly speaking, is not entirely correct, as the infection method the fake email creator is referring to is called “Drive-by download” or “Drive-by install” – this is one of many signs that victims should pay attention to when dealing with Drive by Exploit scam.
Drive by Exploit email is a common type of scam that goes around the internet, targeting people whose email login credentials were previously compromised in one of the data breaches. Unfortunately, those claims about a disturbing video and webcam recordings frighten users and they fear for their privacy and reputation. Hackers demand at least $726 in Bitcoin to allegedly keep the compromising records undisclosed. However, you should be aware that crooks are simply lying about getting malware into your machine via the drive-by download method.
However, Drive by Exploit email scam is elaborate, because many users are unfamiliar with the term “Drive by exploit,” and, while it is not entirely accurate, such infection method exists and can be used as one of the major attack vectors by cybercriminals – the information leakage is always a possible threat. This is why experts[1] recommend changing all the passwords to complex ones that are never reused for different accounts.[2]
| Name | Drive by Exploit email |
|---|---|
| An alternate name of a scam | Your computer was infected with my private malware |
| Type | Email scam/ phishing campaign |
| Claims | The email states about malware infection and possible damage that this virus can cause. Also, scammers claim that private video of you was filmed and is going to be sent to your email contacts or even published online. All of those are false, and scammers only guessed your password or got that information from another scam campaign, leaked data incident |
| Tactics | Social engineering[3] technique employed to threaten people and get money from them directly with the ransom demands |
| Ransom amount | Goes from $726 to $1200 and differs from one campaign to another. Criminals mainly prefer Bitcoin cryptocurrency |
| Distribution | Deceptive emails, rogue advertisements, websites, and fake domains that copy real pages. Sometimes email addresses may be included in a public database, so scammers use those to target people |
| Danger | Paying can lead to loss of data and money. Any contact held between you and scammers can end up in a dangerous malware infection and privacy issues like identity theft |
| Elimination | Use professional anti-malware and remove Drive-by Exploit email |
| Recovery | To repair the system post-elimination, get FortectIntego and run a scan |
Drive by Exploit email is only one of many similar extortion/sextortion scams that surfaced online. This one was reported multiple times online in these past few months, so it seems that criminals are not stopping with their malicious campaigns.[4] People who receive the scammy message report that it comes with a lengthy notification and all those claims about your private information, hacked account, pornographic content.
Drive by Exploit email virus mainly focuses on these fraudulent statements:
- your account was accessed by hackers;
- full control of the computer is gained;
- spyware is installed on the machine;
- private data and webcam video was recorded;
- personal data can be published publicly and sent out to your contact list.
The email message states that all the malicious activities can only be stopped by paying the ransom demanded on the scammy Drive-by Exploit email. Although reports from victims state that the message is pretty much the same for all the targets, a ransom amount can go from $726 to $1200. Remember that these are fraudulent statements, and there is no malware on your device, in most cases.
Nevertheless, you should exit the window with that scam message and try to remove Drive-by Exploit email traces and possibly related programs, files. Also, your device may be exploited due to some vulnerabilities that you are not aware of, so get an anti-malware tool and scan the machine to avoid serious malware infection consequences. After a scan with anti-virus, we also recommend using FortectIntego for best results. 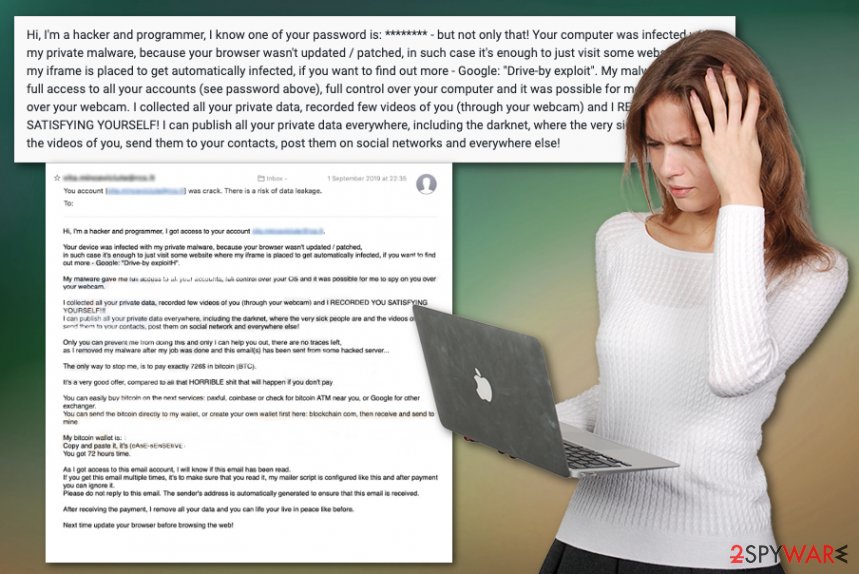
The Drive by Exploit email message states (short version):
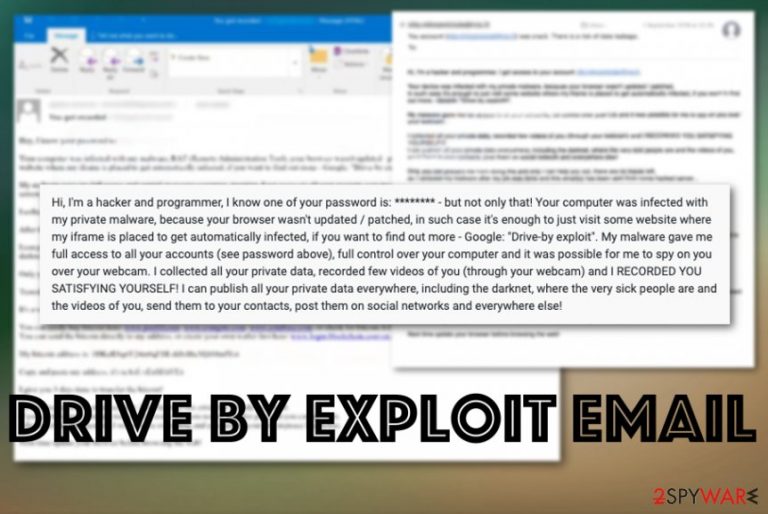
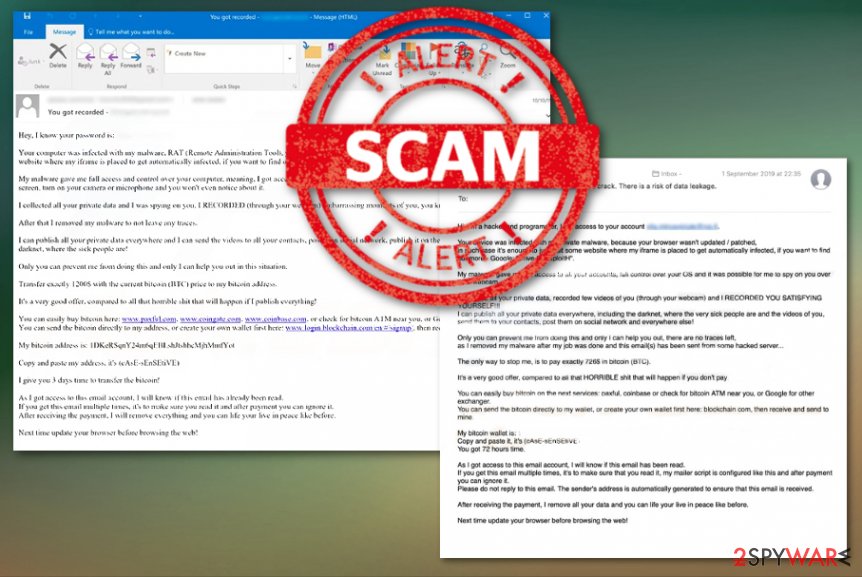
Hi, I'm a hacker and programmer, I know one of your password is: ******** – but not only that!
Your computer was infected with my private malware, because your browser wasn't updated / patched, in such case it's enough to just visit some website where my iframe is placed to get automatically infected, if you want to find out more – Google: “Drive-by exploit”.
My malware gave me full access to all your accounts (see password above), full control over your computer and it was possible for me to spy on you over your webcam. I collected all your private data, recorded few videos of you (through your webcam) and I RECORDED YOU SATISFYING YOURSELF!
I can publish all your private data everywhere, including the darknet, where the very sick people are and the videos of you, send them to your contacts, post them on social networks and everywhere else!
You need to exit the email as soon as possible and remove Drive by Exploit email, any traces of other malware, and programs that possibly got installed already behind your back. To fully eliminate the issues surfacing on the computer, you should rely on professional anti-malware tools that can find and delete those malicious programs.
Additional tips for Drive by Exploit email removal can be:
- remember that contacting people, clicking on links and content on the email itself can lead to direct malware installation;
- paying is not an option because all the claims are false, so you would lose your money;
- scammers use various scary claims, but always think about things you actually did and their statements;
- check the system for cyber threats more often to avoid infiltrations in the first place.
Malicious files may be attached to emails and deceptive advertisements
Malware campaigns involve various distribution techniques and methods used to spread infections behind the user's back, while no symptoms are caused. It happens when various deceptive techniques get employed. Deceptive sites, copies of real domains with malicious scripts all over them, even other spam emails deliver payloads on the targeted computers.
Criminals disguise their products as common files and even plants malicious scrips in push notifications, deceptive promotional sites. You need to pay close attention to anything that appears on your screen, especially when it involves emails, social media accounts. Try to keep the AV tools running and securing the machine.
Drive by Exploit email termination should be followed with a thorough system scan
Drive by-Exploit email virus can also occur on mobile devices, despite the operating system, so you should be aware of these fraudulent emails when you check the email box on your iPhone or Android phone. The best way to avoid any infiltration of malware is to run malware scans more often on all your devices.
Drive by Exploit email removal can be performed with the anti-malware program also, and this is the best way to clean any program that can initiate the infiltration of different malware. Powerful security programs can also indicate system flaws and security issues.
You can remove Drive by Exploit email, other intruders, and PUPs that your antivirus tool indicates with a few clicks of the computer mouse. This is the best way to tackle cyber infections because all traces can be cleaned automatically. Of course, double-check before any other steps and make sure to avoid shady emails in the future.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Drive by Exploit email. Follow these steps
Uninstall from Windows
Get rid of Drive by Exploit email by following the steps on the Windows device
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
Clean the macOS machine with the help of this Drive-by Exploit email virus removal guide
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Drive by Exploit email registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting spam tools
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Bedynet. Bedynet. Spyware related news.
- ^ 8 tips to make your passwords as strong as possible. Mentalfloss. Knowledge and interesting facts.
- ^ Nate Lord. Social engineering attacks; common techniques. Digitalguardian. Data protection blog.
- ^ Drive-by exploit? Is this real? On an iPhone?. Reddit. Online community forum.
