Remote Administration Tool (RAT) email. Is this scam dangerous?
I infected you with my private malware (RAT) (email scam) Removal Guide
What is I infected you with my private malware (RAT) (email scam)?
Remote Administration Tool infection email is a message scamming people with the scary warning about possible virus infiltration
Remote Administration Tool (RAT) email is a malicious spam campaign that is coming from the I hacked your PC group. It is using the titles: I infected you with my private malware, We have installed one RAT Software, You Got Owned, and so on.
Criminals are frightening users that RAT (Remote Administration Tool)[1] was installed on their computers for tracking. These people claim that they got access to your desktop screen, camera, microphone, and other directories and that they will expose the collected personal data to the world. As prevention for these actions, hackers offer to pay them a price of $900 or $1600 in Bitcoin.
If you happen to receive an email from spammers, make sure you ignore it. Additionally, double-check the system with your anti-virus to make sure that you are not required to take care of Remote Administration Tool removal.
| Name | Remote Administration Tool (RAT) email |
|---|---|
| Type | Email scam/Trojan/malware |
| titles used in the scam |
|
| True/false | This is a scam |
| main features | It claims that the system is infected with malware, it will reveal the personal information. To prevent being exposed, you must pay a ransom |
| Possible dangers | Can come with malicious components attached |
| Ransom price | $900 or $1600 in Bitcoin |
| Related threats | Remote Administration Tool |
| Elimination | Check for any malware by scanning your device with reliable security tools |
| system health | You can use FortectIntego to check if there was any damage initiated by hackers |
The infectious email appears to be a fake email message which is very good news for infected users. However, you still need to be careful with such content as it might carry malicious objects attached somewhere. Furthermore, if this scam keeps appearing frequently in your email inbox, you should change your passwords to
While I infected you with my private malware scam might be fake, it still has the risk of bringing potentially infectious content to your Mac or Windows computer. If you are keen on searching and removing suspicious threats from your computer or laptop, you can use reliable antimalware and also check out OS cleaning tips that are provided at the end of this article.
Spam email features and danger
The scam aims to collect Bitcoin transfers from gullible users who get scared once attacked by such type of message:
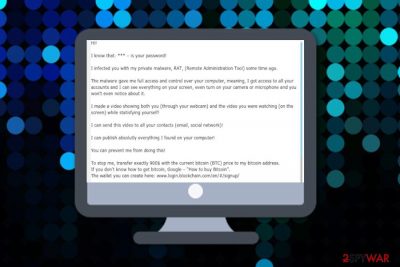
Hi!
I know that: *** – is your password!
I infected you with my private malware, RAT, (Remote Administration Tool) some time ago.
The malware gave me full access and control over your computer, meaning, I got access to all your accounts and I can see everything on your screen, even turn on your camera or microphone and you won’t even notice about it.
I made a video showing both you (through your webcam) and the video you were watching (on the screen) while statisfying yourself!
I can send this video to all your contacts (email, social network)!
I can publish absolutly everything I found on your computer!
You can prevent me from doing this!
To stop me, transfer exactly 900$ with the current bitcoin (BTC) price to my bitcoin address.
If you don’t know how to get bitcoin, Google – “How to buy Bitcoin”.
The wallet you can create here: www.login.blockchain.com/en/#/signup/My bitcoin adress is: 1Q9QmbRyHu89jWKwVXgkvTMNDuEags5kdq
After receiving the payment, I will delete the video, and we will forget everything.
I give you 4 days to get the bitcoins.
Since I already have access to your computer, I know when you read this email.
Don’t share this email with anyone, this should stay our little secret!
Other, shorter versions of this scam read:
Your computer was infected with my malware, rat (remote administration tool), your browser wasn't updated / patched, in such case it's enough to just visit some website where my iframe is placed to get automatically infected, if you want to find out more – google: “drive-by exploit”.
I infected you with my private malware, (RAT), a few months back when you visited some website where my iframe was placed and since then, I have been observing your actions.
To stop me, transfer exactly 1600$ with the current bitcoin (BTC) price to my bitcoin address.
My bitcoin adress is: 1JtTm5eCxqj94Pb4d58pWGZjLUMYHuC6yX
After receiving the payment, I will delete the material I got from you, we will forget everything and you can continue living your life in peace like before! I give you 3 days to get the bitcoins and pay! Since I got access to your account, I know if this email already has been read!
To make sure you read this email, I sent it multiple times! Don't share this email with anyone, this should stay our little secret!
Our recommendation would be to calm down and not rush to pay the hackers who spread the malicious software email password scam as this is fake and you will lose your money for absolutely nothing. However, if you still are full of doubts and believe that the cybercriminals somehow managed to steal your password, you can check if it was not leaked in some type of data breach attempt by visiting Haveibeenpwned.[2]
You need to remove the email from your email box as this scam claims absolute nonsense. However, this gives you a sign that you should not forget to take care of security measures while performing computing work or browsing online. It is very important to create strong and complex passwords and enable two-factor identification so that particular log-ins will be not that easy to access.
Usually, scamming messages, such as I infected you with my private malware, We have installed one RAT Software or You Got Owned are targeting the most sensitive fields from which crooks have the best chances of collecting income. Users often do not mind creating easy-guessing and short passwords which are not hard to identify. As noticing that, cybercriminals can threaten people that their passwords have been stolen as it is very possible to be true due to the lack of safety. To ensure that no personal data has been leaked, perform Remote Administration Tool removal if needed.

Rogue files from email notifications and random links can spread malware
According to technology experts from Virusai.lt,[3] email scams are one of the most common ways for malware distribution. Email messages come with attachments (executables, Word documents, PDF files) that carry the malicious payload. Users need to be very careful while opening suspicious attached documents/files. It is strongly recommendable to scan such content with reputable antimalware.
It is known that especially ransomware and trojan[4] spreaders like distributing their malware via email spam. It is very important that people gain basic knowledge on how to recognize suspicious emails from truly official ones. Once you receive a doubtful-looking email, you have to always check for grammar mistakes in the text. Usually, criminals do not pay attention to their writing.
Furthermore, always check the sender, from what kind of email address the letter came from. If it is a reputable organization, you will not see anything like “restoredata@firemail.cc”. Additionally, reputable companies will contact you by mobile phone if the need for communication is urgent.
Fake messages can stop when the virus gets removed

You need to complete the virus removal to ensure that no malware is trying to enter your computer system via such a scam. This type of scamming application might be caused by some type of malicious threat or an ad-supported application that needs to be terminated from the machine too.
In order to remove I infected you with my private malware (RAT) (email scam) virus from your Windows or Mac computer system, you need to scan the machine with trustworthy antimalware software to identify the cause. Also, you can take a look and try completing the below-provided guide to clean infected directories in your operating system.
Getting rid of I infected you with my private malware (RAT) (email scam). Follow these steps
Uninstall from Windows
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
How to prevent from getting spam tools
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ What is a Remote Administration Tool (RAT)?. McAfee. Securing tomorrow.
- ^ Have I Been Pwned. haveibeenpwned.com. Check for breached data.
- ^ Virusai.lt. Virusai.lt. Spyware news.
- ^ What is a Trojan Virus?. Kaspersky Lab. Resource Center.









