Error Code 0x80073b01 scam (Support Scam Virus) - Free Instructions
Error Code 0x80073b01 scam Removal Guide
What is Error Code 0x80073b01 scam?
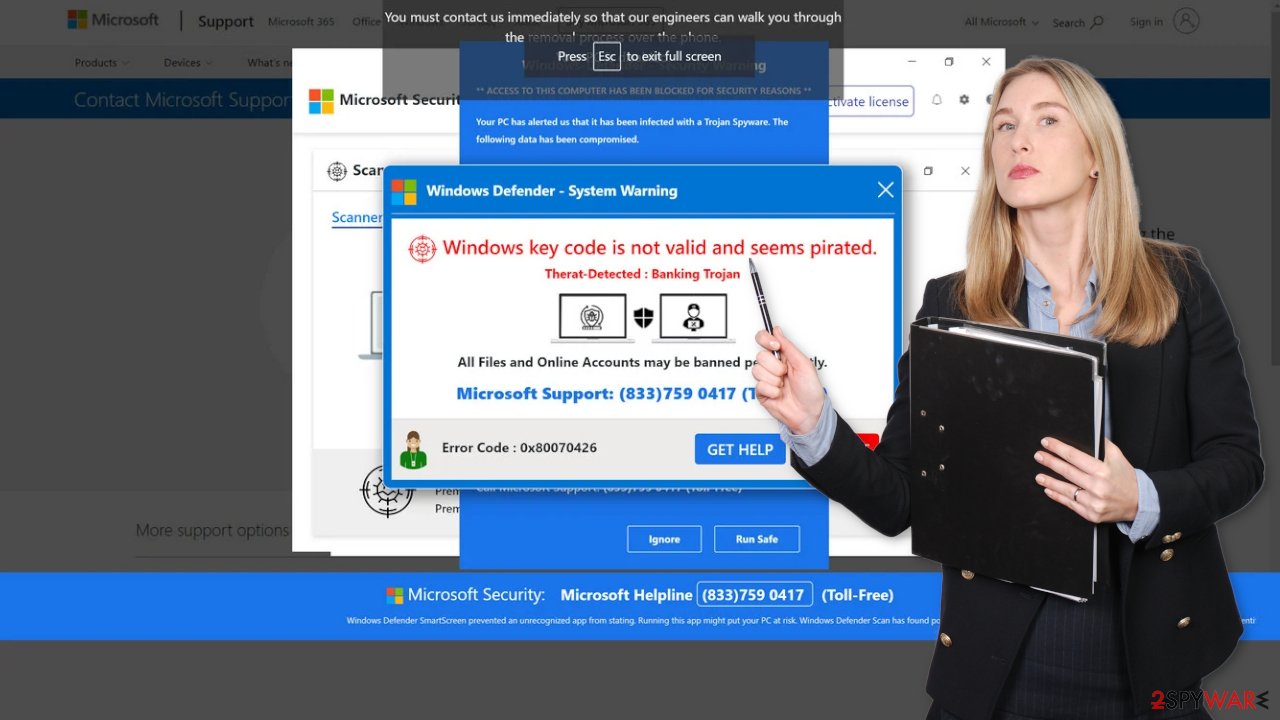
Error Code 0x80073b01 alert is a fake Microsoft technical support page set up by scammers
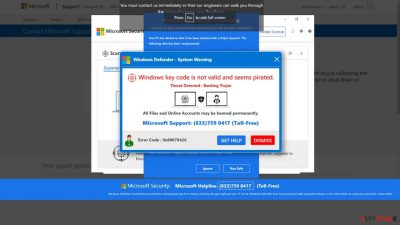
In the age of digital connectivity, online scams and cyber threats have become ever more prevalent. Among these malicious tactics, the “Error Code 0x80073b01” pop-up scam has emerged as a particularly concerning and deceptive scheme. In this article, we will delve into the intricate workings of this scam, shedding light on its fraudulent nature, the tactics employed by scammers, and most importantly, how to safeguard yourself against falling victim to such deceitful traps.
| NAME | Error Code: 0x80073b01 |
| TYPE | Tech support scam |
| SYMPTOMS | Fake Microsoft alert pops up on full-screen mode |
| DISTRIBUTION | Software bundling, suspicious ads |
| DANGERS | This might lead to malware infection, sensitive detail disclosure, and stolen money |
| ELIMINATION | Get rid of viruses by using an anti-malware tool or follow manual instructions below |
| FURTHER STEPS | Malicious programs can trigger various issues, so you should run FortectIntego to find and possibly fix virus damage yourself |
Understanding the Scam
The “Error Code 0x80073b01” pop-up scam is a browser-based trap intended to trick unwary users by playing on their sense of urgency and anxiety. It often takes the form of a troubling communication that purports to be from Microsoft or a reliable tech help organization. The phony notice frequently claims that your machine has crashed badly or is infected with a virus. This is a deliberate ploy to incite panic and force users to respond immediately.
Human psychology is a skill that the con artists behind the “Error Code 0x80073b01” pop-up scam use to their advantage. They seek to obstruct rational thought and induce rash actions in users by playing on fear and uncertainty. The hoax is made more convincing by the use of official-sounding language and Microsoft logos, which lends the fraud an air of legitimacy.
The scam alert offers a phone number that users are told to call for technical support in order to further the con. However, calling this number will connect you with fraudsters experienced at deceiving victims rather than real tech help staff. When you answer the phone, the con artists start a series of steps that give them remote access to your computer.
Once given remote access, con artists use a variety of strategies to keep up their pretense of technological know-how. They might instruct victims to launch different system programs, including the Event Viewer, which shows a ton of system logs, many of which to an inexperienced eye appear alarming. These records are then utilized by the con artists to further persuade victims of the seriousness of their computer's condition.
Scammers utilize a number of psychological ploys to win the user over as the encounter goes on. They frequently stick to a script, describing how the problem may be fixed in a sequence of stages that usually end with the purchase of pointless software or services. Victims are persuaded to provide their credit card details under the pretense of paying for legitimate support.
What to do?
Here are some essential steps to safeguard yourself from falling victim to this deceitful scheme:
- Stay calm: Regardless of how alarming the pop-up message may seem, remember that legitimate tech support entities do not display alerts in this manner. Take a deep breath and resist the urge to act hastily.
- Do not call: Refrain from dialing any numbers provided in the pop-up. Microsoft and other reputable companies do not ask users to call for support through unsolicited pop-ups.
- Use Task Manager: If your browser becomes locked in full-screen mode due to the scam pop-up, use the Task Manager (Ctrl + Shift + Esc for Windows) to close the browser. This will effectively halt the scam's progress.
- Ensure security software: Maintain up-to-date and reputable antivirus and anti-malware software on your system. Regular scans can help detect and prevent such scams.
- Verify official support channels: If you encounter a potential issue with your computer, visit the official website of the company (e.g., Microsoft) and seek assistance through their verified support channels.
Check your browser extensions
It's likely that the appearance of this specific tech support scam page was brought on by a malicious extension that was added to your web browser. Online applications have the authority to take over your browser and modify crucial settings. After that, the application can start to show intrusive pop-ups and adverts and trigger redirects to dubious websites. The plugins you've added should be carefully removed by opening the browser's settings. This step might be used to see if any obvious changes occur.
Additionally, it's crucial to take action to protect the integrity of your web browsers by getting rid of any tracking tools that may be installed by shady websites. Cookies[1] and cache can be used fraudulently even though they normally improve user experiences by offering pertinent results and customized suggestions based on unique interests.
By selling cookies to ad networks or other third parties, these unscrupulous actors can flood your inbox with misleading advertisements. Additionally, these behaviors provide fraudsters access to a variety of information, including your IP address, location, websites viewed, links clicked, and online purchases.
Consider using a comprehensive solution like FortectIntego that can handle various aspects to speed up these tasks. This tool removes previously collected data from your device in addition to stopping tracking methods. Additionally, it has the capacity to fix serious system flaws, fix corrupted files, and fix registry issues. This function turns out to be especially helpful after a virus infection.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the window's top-right).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
MS Edge (legacy)
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.
![Remove extensions from Edge Remove extensions from Edge]()
Scan your machine with professional security tools
There's a good chance that your computer is infected with adware or another kind of potentially unwanted application (PUA)[2] that directs you to websites connected to rogue advertising networks. These applications frequently enter the operating system through the download of freeware. Software bundling is a method used by websites that offer freeware to make money. This entails incorporating extra software into installers that profits from user interactions.
It's advised to only use official web stores and developer websites to avoid such incidents. Even while this strategy could have some up-front charges, it can eventually spare you from suffering system harm over the long run or becoming a victim of internet scams. Additionally, if you want to make sure that no installation steps are hidden from your view, you can choose the “Custom” or “Advanced” installation approach. Examine the list of files carefully, and if there are any unneeded programs, deselect them.
SpyHunter 5Combo Cleaner and Malwarebytes stand out as exceptional options because to their well-deserved reputation as reliable anti-malware tools. These programs have the ability to locate and successfully remove a variety of dangers that are hiding inside your system. Sometimes manual removal attempts result in re-infection because users may fail to notice linked files hidden across multiple directories. However, if you're still determined to try manual removal, follow these instructions:
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till the uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Chris Maus. What Are Cookies and Are They Dangerous?. Qkey. Payment Security Providers.
- ^ Chris Hoffman. PUPs Explained: What is a “Potentially Unwanted Program”?. Howtogeek. Technology Magazine.






