Fake keyboard CAPTCHA verification scam (virus)
Fake keyboard CAPTCHA verification scam Removal Guide
What is Fake keyboard CAPTCHA verification scam?
Fake keyboard CAPTCHA verification scam is the campaign during which users get tricked into installing a trojan
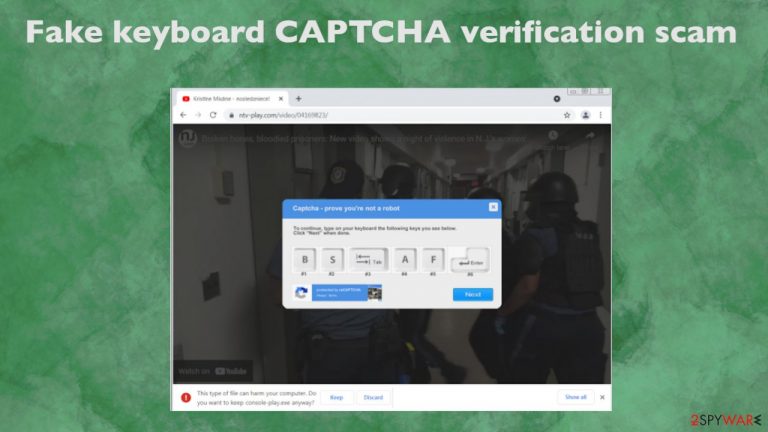
“B, S, Tab, A, F, Enter” CAPTCHA scam is a pop-up that states about verification need to prove that the user is not a robot. This is not a real Captcha form that is used to tell humans apart from the automated computer activity. It is known that these tests encourage people to enter the particular combination on the keyboard and hit enter to confirm that the person is really behind the screen, so browsing can continue. Unfortunately, then scammers can expose users to dangerous content and inject Ursnif/ Gozi trojan on the machine.[1]
This malware campaign was discovered to prompt users into allowing the trojan to download. The intrusive captcha prompt tricks users into bypassing warnings on the browser, so the download can happen. Once that is done and trojan is added on the machine, various information can be stolen, including banking credentials and personal data. “B, S, Tab, A, F, Enter” CAPTCHA scam downloads file when the suspicious URL leads to the download of the file instead of showing the YouTube video about particular New Jersey women's prison.
The downloaded file – console-play.exe contains the payload of this virus. This is the point where the browser should prompt about the possible infection and danger behind the execution of this piece. However, the fake captcha verification pop-up shows up and prompts users to press B, S, Tab, A, F, and then Enter keys. Those letter keys do nothing, but Tab and Enter allow the browser to focus o the Keep file button and allowing the malicious infection to get saved.
| Name | “B, S, Tab, A, F, Enter” fake Captcha verification |
|---|---|
| Type | Malware spreading campaign, trojan, scam |
| Technique | Captcha verification pop-up disguises the scam that aims to allow malicious files to download from the web |
| Distribution | Online advertisements, social engineering[2] techniques and pirating software, malicious emails can lead to exposure to such scam sites and campaigns |
| Danger | The distributed trojan can access personal data and steal banking credentials, trigger the additional drop of the virus payload |
| Elimination | Threats like this require anti-malware tools, so all the pieces can be detected and completely removed from the machine |
| System repair | Try to run the FortectIntego and check all the parts of the system for affected or corrupted pieces that can interfere with the normal performance of your PC |
These fake captcha prompts can be a clever way to spread malicious files by relying on users themselves. The malicious warning alert gets redirected, and the possibly dangerous piece accesses the system quickly. Unfortunately, the trojan payload file gets executed once downloaded, and the malicious behavior can start without any additional permissions needed.
The video that intentionally was a start of interest can start after some time automatically, so users cannot think more about this than just that verification worked. Information-stealing trojan can get active and work free from here. Its executable gets loaded on the machine alongside other files needed for the decoy, process launching, and persistence.
It is possible to keep this infection at bay with anti-malware tools like SpyHunter 5Combo Cleaner or Malwarebytes because AV detection engines are based on finding anything possibly malicious, and the main file that gets downloaded can be indicated by many tools designed like this. Fake keyboard CAPTCHA verification scam removal is important and needs to take place as soon as possible because, as many experts[3] note, trojans can open backdoors to the PC and result in direct attacks.
Silent damage and issues that Ursnif or any other malware can cause
Settings on the machine can be read and changed, including various registry entries, powershell commands. When the scam campaign ends up successfully infiltrating the machine, you may not notice any symptoms because trojans and more advanced malware like this can be silent and work inside without causing any issues with the performance. Unlike the Fake keyboard CAPTCHA verification scam, malware like this is dangerous and critical yet silent.
An infection can alter the Windows registry database, damage vital bootup, and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software cannot do anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstallation is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it can also remove malware that has already broken into the system thanks to several engines used by the program. Besides, the application can also fix various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

Functions of the malware distributed via fake verification messages
“B, S, Tab, A, F, Enter” scam is delivering the particular information-stealing malware – banking trojan. Such infection can aim to run processes on the machine or even infiltrate additional malware on the PC, but the main goal of the virus is to obtain valuable information.
The infection can steal a broad range of private and sensitive data related to credit information, banking platforms. The malicious program can get these details from the infected system directly or use particular applications installed. It is possible to trigger layers on the browser that logs keystrokes and steals information you put in when logging in to a particular site or banking service.
The threat can target information related to your browsing activities, collect cookies, usernames, passwords, and financial platform-related data. The threat obtains various details, and later on, the information can be used in secondary attacks and damage machines, affect them more than the initial “B, S, Tab, A, F, Enter” fake CAPTCHA scam managed to.
If malware is not letting you use antivirus in normal mode, access Safe Mode and perform a full system scan from there.
Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
Once you reach Safe Mode, launch SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable antivirus, update it with the latest definitions and perform a full system scan to eradicate malware and all its malicious components. You need to double-check to ensure that malicious programs dropped during this scammy process were eliminated completely.
Do not hesitate and try to check if the system got affected immediately. The threat installed during this “B, S, Tab, A, F, Enter” CAPTCHA scam campaign that can result in privacy issues, money losses, identity theft. Trojans can run alongside other threats and drop additional malware acting as a vector, so make sure to repair the system fully after the infection.
The maliciosu URLs that deliver these malicious files can be dropped in emails, deceptive messages in social media, or included in advertisements online. As you can see, the infection process is quick, and you can receive the trojan immediately after the Fake keyboard CAPTCHA verification message pop-ups. Make sure to repair the system with FortectIntego, keep the security tools, and ensure the system is virus-free before you use all the financial sites and important documents again.
How to prevent from getting malware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Lawrence Abrams. Malware campaign uses clever 'captcha' to bypass browser warning. Bleepingcomputer. IT and cybersecurity news.
- ^ 9 Examples of Social Engineering Attacks. Terranovasecurity. Security tips and advice.
- ^ Dieviren. Dieviren. Spyware related news.
