Ursnif virus (Free Guide) - updated May 2020
Ursnif virus Removal Guide
What is Ursnif virus?
Ursnif is the info-stealing threat distributed in various online scam campaigns
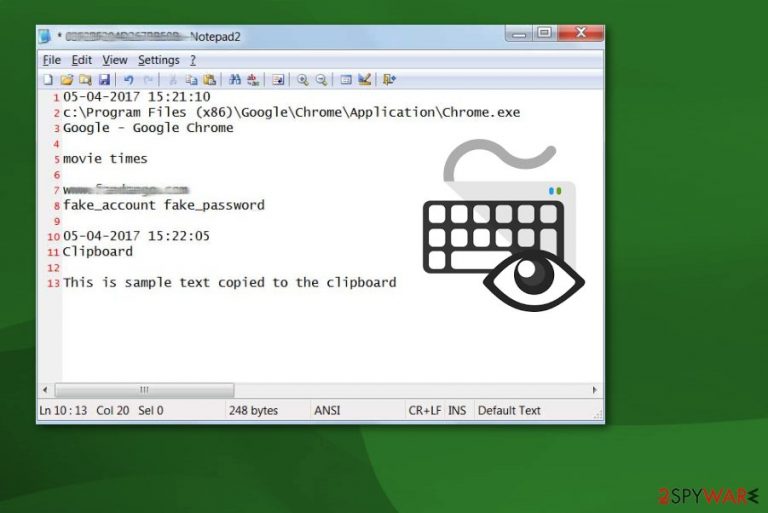
Ursnif (also known as Gozi, ISFB, or Dreambot) is a virus that specializes in banking credentials and other information-stealing by using a variety of methods. Released in 2006, malware has seen a fair share of updates and is constantly returning with new campaigns that typically utilize malvertising (fake Adobe Flash updates) and malspam (Word or Excel documents embedded in phishing emails) for the propagation.
Once inside the system, the Ursnif virus[1] launches the malicious svchost.exe and explorer.exe processes, which are used to hide its presence on the host machine. Additionally, this modular malware starts numerous activities behind victims' backs, including the distribution of other malware.
However, the main Gozi virus activity is related to data tracking – it employs keylogging and other techniques in order to harvest information from browsers, email accounts, user configurations, as well as digital wallets. Ursnif later sends these details to the Command & Control that is accessible to the attackers only.
The threat is known for spreading during scam campaigns and using other techniques. The more recent fake keyboard verification scam – “B, S, Tab, A, F, Enter” CAPTCHA, during which the payload gets loaded without users' knowledge due to the keyboard inputs that people get tricked into doing themselves.
In 2015, the source-code of Trojan:W32/Ursnif was leaked online[2] and placed on the GitHub platform, which allowed several cybercriminal groups to modify malware in a way that would increase its capabilities. As a result, the Trojan is now widely used and is highly evasive, making it a prevalent choice within the illegal data-stealing business.
| Name | Ursnif, Gozi, ISFB, Dreambot |
|---|---|
| Type | Trojan, Data-stealer |
| Associated process | Explorer.exe, iexplorer.exe, svhost.exe, click.exe |
| Symptoms | Information stealing malware rarely emits any symptoms, as it is designed to operate using stealth techniques. Nonetheless, some victims might notice suspicious computer behavior, such as inability to access particular sites via the web browser, system slowdowns, application/system crashes, errors, etc. |
| Danger level | High. Malware uses several evasion techniques, so it may remain on the system for months before it is detected, gathering sensitive information, such as financial details, account credentials, Social Security Numbers, and much more |
| Distribution | The main distribution method is spam emails boobytrapped with malicious attachments. In most cases, MS Office documents are used, although other file types were also spotted in the wild |
| Elimination | If your computer is connected to a network, disconnect it and then perform a full system scan with anti-malware software and remove the malicious virus |
| System fix | In some cases, malware can infect and damage Windows system files. As a result, users might experience stability issues, such as lag, crashes, BSODs, and errors. To fix these problems, you can use the PC repair utility FortectIntego |
In one of the latest Gozi campaigns, threat actors were spotted delivering the payload within MS Word documents, titled as “info_[date].doc,” that are embedded with malicious macros. As soon as users press “Enable Content,” a Visual Basic code is executed, beginning the infection routine.
This variant of Ursnif was also using anti-detection techniques by injecting its Command & Control servers with a reference list of trusted companies, such as Microsoft:[3]
<…>you may notice the C&C host list includes “microsoft.com”, “update.microsoft.com”, “avast.com”, “cdevinoucathrine.info”, “zcei60houston.club” and “kenovella.club”. This seems odd. Why are the hosts of “microsoft” and “avast” listed here? In fact, this is a way to deceive researchers who capture and analyze the traffic.
In January 2020, security researchers from FireEye have discovered a new variant of Ursnif, which was dubbed SaiGon.[4] While this version still focuses on data stealing, its capabilities include backdoor functionality (which allows it to push other malware), process injection, and various evasion techniques.
Trojan info-stealer can run behind your back and steal major data
This trojan is designed to record various sensitive information about the user, including banking data, logins or passwords, web browsing activity, information about the victim's OS and device. All this recorded information is additionally shared with virus developers. Ursnif keylogger can also delete itself from the system once it receives such a command.
Gozi is constantly evolving, and several cybercriminal groups are working on its improvements. It started targeting various financial institutions from the beginning and recently expanded to more prominent organizations and changed distribution techniques and types of information to steal.
Trojan:W32/Ursnif is known to use different techniques as web injecting, man-in-the-browser, or keylogging functionality. The latest attacks were based on spear-phishing emails and the fact that malware deleted copies of itself after the initial process. These facts make this banking trojan more dangerous and difficult to detect or analyze.
Malware steals various data about the user personally, the device, and other account information like:
- information from your email accounts;
- various information from your browsers;
- logins and passwords of your social media accounts;
- banking website logins and passwords.
Ursnif virus changes various registry keys to keep affecting the system. People behind this threat are focusing on getting revenue from various background activities on your system or even stealing your banking credentials so get your money directly out of your bank accounts.
While there is no way to spot the infiltration of this trojan, you should note that the main way used by this malware to get into the system is spam. Gozi has been using intelligent tactics that rely on infected Word documents that are filled with malicious macros.
If you have recently been asked to enable macros to check the content of the email's attachment, we highly recommend making sure that you are not infected and that there is nothing related to Trojan:W32/Ursnif/ Gozi virus. The easiest way to do that is to scan the system with updated anti-spyware.
If you have any doubts either you have this malware on the device or not, check your system with updated anti-spyware, and perform the virus removal to save your personal information. To get rid of any viruses, use reputable anti-malware/anti-virus software.
We do not recommend performing the Trojan:W32/Ursnif removal manually as this is a dangerous cyber threat that can be related to numerous different components hidden on your computer. If you are blocked, reboot your PC to Safe Mode with networking first to disable the virus. Finally, we recommend a scan with FortectIntego to remediate the Windows system and avoid stability issues post-infection.
In most of cases, antivirus programs detect the Gozi Trojan horse as:
- TR/Crypt.XPACK.Gen
- Trojan:W32/Ursnif
- Virus/Win32.PolyRansom.c
- HEUR/Fakon.mwf
- Win32.Doboc.Gen.1
- Troj.Heur.LP.mE18
- etc.[5]
Virus activity may lead you to serious privacy issues or money loss, so you need to remove Ursnif virus as soon as possible. This type of cyber intruder can download and install other malware, including ransomware-type viruses, which could lead you to data loss. There is no need to keep yourself at such a risk. However, we should say one more time that you shouldn't try to delete the trojan manually as you can lead your system to serious trouble by removing needed system components.
Spam email and online scam campaigns spread the trojan accross devices
Researchers[6] have always been warning people that they shouldn't believe anything on the internet that looks too good to be true. That includes banner ads, in-text links, and spam emails as well.
Spam has also been a commonly used technique for trojan distribution. However, when discussing a trojan horse, note that it relies on a slightly different distribution method. The main way used by its developers to deliver this malicious threat relies on Word documents filled with malicious macros. Once downloaded, such an attachment asks you to enable macros and launches the virus in this way.
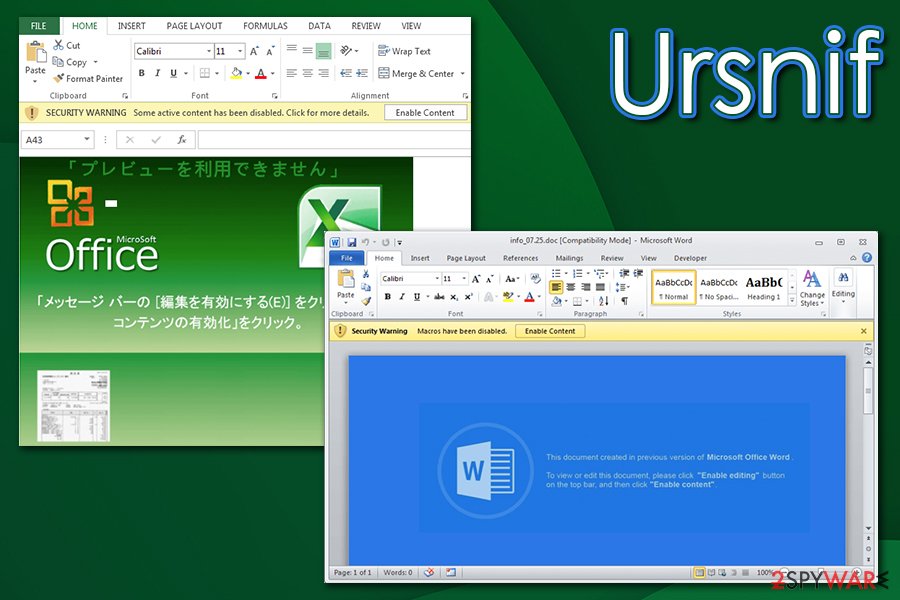
Other unique features about the distribution technique used by this banking trojan:
- Compromised email accounts are used to reply to emails. The content of an email looks convincing;
- The malicious payload is released when the user downloads the macro-filled documents. However, the Trojan waits until the attachment is closed to launch the process;
- The safe-looking Word attachment also executes the PowerShell code. After this process, malware connects to URL and delivers the payload directly on the system;
- The whole campaign is based on the fact that emails are sent from familiar services what increases the chances of people opening the infected file;
- The most common pattern used to name these files is “the name of a local business or service_Statement”
You can avoid getting these intruders if you delete spam emails that are not from companies you know or services you do not use. Make sure to clean those suspicious emails from the email box more frequently and try to scan files before downloading them on the device. Pay more attention to these processes and do not open an email if you were not expecting that.
Trojan:W32/Ursnif virus termination is not easy, but achievable
When dealing with any silent intruder, anti-malware tools are the best option in virus elimination. However, trojans are one of the most dangerous cyber infections that can additionally install malware on the system. To remove Ursnif virus and all related programs from the system, run a full system scan with updated anti-spyware.
If you are blocked, check two methods given below that are supposed to help you disable the virus before a scan. You can get rid of the Trojan:W32/Ursnif infection by relying on proper anti-malware tools that possibly find and delete this threat and any other threats related to issues with your machine.
We recommend SpyHunter 5Combo Cleaner or Malwarebytes for the possible virus removal, although you can also pick a security tool of your choice. Update these programs to their latest versions and run a full system scan to check your device thoroughly and get rid of any malware hiding on your system.
You can also use the anti-virus software of your choice, just make sure that it is a reputable and well-known tool. As for the Gozi virus damage, you need to think about PC repair or optimization tools like FortectIntego that can fix affected files and functions for you.
Getting rid of Ursnif virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Ursnif using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Ursnif. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Ursnif and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting trojans
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Trojan malware on the rise in the banking sector. Biztech. Technology solutions that drive business.
- ^ TOR. Wikipedia. The free encyclopedia.
- ^ Xiaopeng Zhang. New Ursnif Variant Spreading by Word Document. Fortinet. Security blog.
- ^ Sandor Nemes, Zander Work. SAIGON, the Mysterious Ursnif Fork. FireEye. Malware research blog.
- ^ Trojan analysis. Virustotal. Online malware scanner.
- ^ Semvirus. Semvirus. Spyware related news.







