FrequencyRemote Mac virus (Free Guide)
FrequencyRemote Mac virus Removal Guide
What is FrequencyRemote Mac virus?
FrequencyRemote is a malicious app designed to steal your data and show you intrusive ads
The FrequencyRemote malware is a dangerous Mac application that has been specifically designed to hijack web browsers, distribute intrusive advertising, and evade detection and removal through sophisticated persistence techniques. It belongs to the notorious Adload malware family and has multiple harmful variants created by malicious hackers.
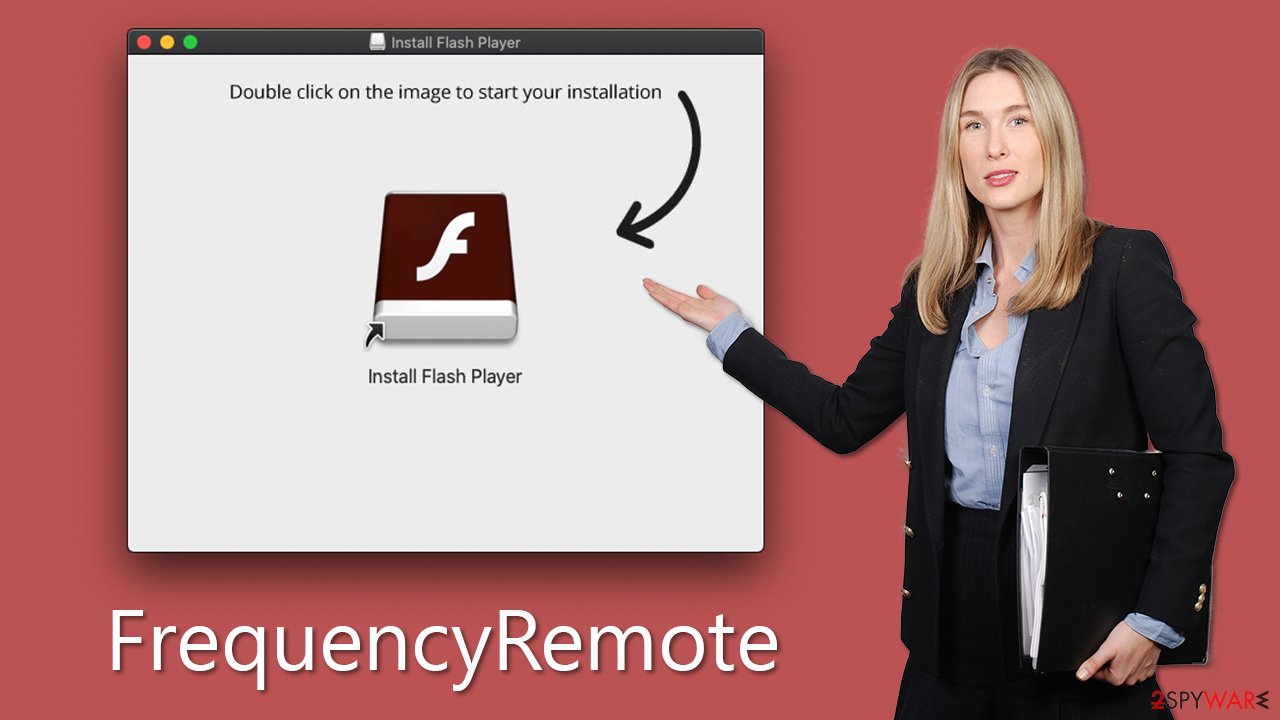
Using deceptive tactics like pirated software installers and fake Flash Player upgrades, the FrequencyRemote malware successfully spreads its infection, infecting numerous users on a daily basis. Once activated, it takes control of browser settings, altering the homepage and default search engine and bombarding users with sponsored links and irritating ads. This can expose users to phishing content, including scams promising quick riches or fake virus infection alerts, posing serious risks to their online security and privacy.
The browser extension associated with FrequencyRemote is particularly concerning, as it stealthily collects sensitive personal information, such as login passwords and credit card details, further exacerbating the privacy and security threats this malware poses.
In the following sections, we will explore effective methods for removing the FrequencyRemote malware from Mac systems and preventing its recurrence. Taking prompt and proactive action against this malicious application is crucial to safeguarding Macs against the harmful characteristics of malware and the potential damage it can cause to online security and privacy.
| Name | FrequencyRemote |
| Type | Mac virus, adware, browser hijacker |
| Malware family | Adload |
| Distribution | Pirated software installers, fake Flash Player updates, misleading ads |
| Symptoms | Installs a new extension and application on the system; changes homepage and new tab of the browser; inserts ads and malicious links; tracks sensitive user data via extension |
| Removal | The fastest way to remove Mac malware is to perform a full system scan with SpyHunter 5Combo Cleaner security software. We also provide a manual guide below |
| System optimization | If you don't keep your browser clean of cookies and other web data, ads you've seen before will reappear, or your data could continue being tracked. But FortectIntego can help stop that |
How Mac malware spreads and how to avoid it
Mac malware, particularly variants of Adload, can spread through various deceptive tactics. Two prominent examples are fake Flash Player updates and cracked software downloaded from unofficial websites.
First, hackers may disguise malware as fake Flash Player updates, tricking users into downloading and installing the malware under the guise of a legitimate software update. This tactic preys on users' trust in familiar software like Flash Player and their willingness to keep their software up-to-date, thereby luring them into unwittingly installing malware onto their Macs.
Second, cracked software downloaded from unofficial websites is another common way for Adload variants to spread. Hackers may distribute malware-infected versions of popular software applications that are cracked or pirated, enticing users to download and install them for free. However, these unauthorized sources are often riddled with malware, and users who download and install such software are at risk of infecting their Macs with Adload or other types of malware.
Both of these tactics rely on exploiting users' vulnerabilities, such as their trust in legitimate software updates and their desire to access paid software for free. It is important for Mac users to exercise caution and only download software from trusted and official sources to avoid falling victim to these deceptive tactics and inadvertently installing malware on their systems.
Regularly updating software from legitimate sources, using reliable antivirus software, and being cautious while downloading software from the internet is crucial steps in protecting against the spread of Mac malware, including Adload variants.
Adload explained
Adload, a persistent Mac threat, has been actively distributed via fake Flash Player installers or pirated software installers, making it one of the most prolific threats in the Mac ecosystem. With hundreds of variants released since at least 2017,
Adload is known for its unique naming pattern, where titles consist of randomly picked two or three words, for example, MicroInput or DominantCommand – previous versions of the virus. Additionally, all variants of Adload use the same magnifying glass icon, albeit with varying background colors such as blue, teal, green, red, and gray.
Despite being initially classified as adware, FrequencyRemote, and other Adload variants have evolved to pose serious threats. The primary objective of the cybercriminals behind Adload is to generate passive revenue from intrusive ads in the form of pop-ups, deals, offers, banners, and more.
However, due to the use of rogue advertising networks, the quality of these ads can be appalling, with a higher likelihood of encountering phishing and other malicious content. To evade Mac's built-in security measures, the authors of Adload are constantly changing modules and improving persistence mechanisms, making it a formidable and constantly evolving threat.
Choose automatic FrequencyRemote removal
Adload variants may not be overly complex in technical terms, but their persistence mechanisms often outsmart Apple's defenses, allowing many new versions to slip past Mac's XProtect. As a result, the malware can remain active in the background for extended periods of time unless alternative removal methods are used.
Third-party security software, such as SpyHunter 5Combo Cleaner or Malwarebytes, can significantly simplify the elimination process. Manual removal of the virus may require advanced computing knowledge, as the malware creates numerous items upon infiltration, and missing any of them could result in the infection recurring.
If you choose to attempt malware removal yourself using the steps provided below, exercise extreme caution when dealing with browsers. Clearing browser caches, cookies, and other leftover files is essential for safeguarding your privacy. Alternatively, you can opt for an automatic solution using FortectIntego.
Manual method of elimination
1. Delete the app and the extension
Once the malware infiltrates the system, it initiates background processes that run whenever it is active, carrying out its malicious activities. To remove the main application of the virus, you need to access Activity Monitor and halt its associated processes using the following steps:
- Open Applications folder
- Select Utilities
- Double-click Activity Monitor
- Here, look for suspicious processes related to adware and use the Force Quit command to shut them down
- Go back to the Applications folder
- Locate the malicious app and move it to Trash.
After addressing the main application, proceed to open Safari, Chrome, or any other browser you use, and delete the extension that utilizes the magnifying glass icon against a gray background.
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
If you encounter difficulties in removing the malware's extension through normal means, resetting the browser can be a viable option to bypass the app's persistence mechanisms and eliminate the extension without any issues. If you require assistance with this procedure, please follow the instructions below:
Safari
- Click Safari > Preferences…
- Go to the Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop, and then select Empty Caches.
![Reset Safari Reset Safari]()
Google Chrome
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.
![Reset Chrome 2 Reset Chrome 2]()
Take care of leftover files
Even after removing the browser extension and the main application, it's possible that numerous files may still remain on your system. For instance, the virus may utilize Login items to launch itself every time macOS is loaded automatically, and virus-related profiles may enable it to execute actions without the user's knowledge. Therefore, it's crucial to thoroughly eliminate these leftover files to ensure the complete removal of the malware.
- Go to Preferences and select Accounts
- Click Login items and delete everything suspicious
- Next, pick System Preferences > Users & Groups
- Find Profiles and remove unwanted profiles from the list
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and delete all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
Finally, clean your browsers from cookies and other web data, as they are commonly used to track users in various ways.
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
How to prevent from getting adware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.







