Get Icons browser extension (Free Instructions)
Get Icons browser extension Removal Guide
What is Get Icons browser extension?
Get Icons is a browser extension with the sole goal of exposing users to intrusive ads
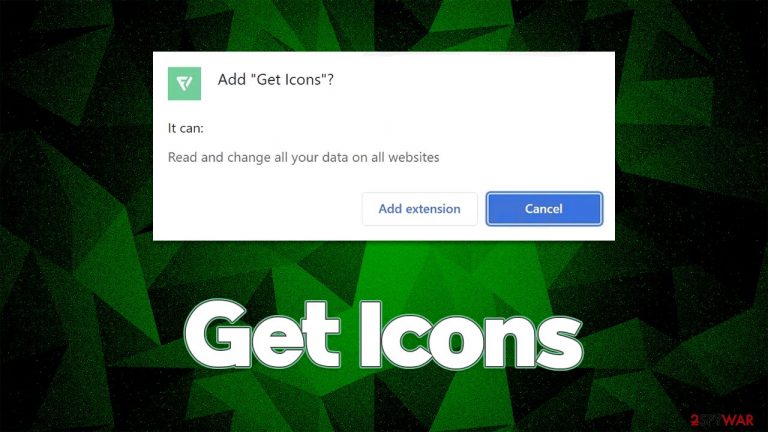
Get Icons is an extension that can be downloaded for seemingly innocent reasons – it is advertised as an app that “allows you to download the most beautiful icons on the internet.” Indeed, some people are heavy into customization of their browsing or computer-using experience, so they might find changing a few icons quite appealing. Unfortunately, this is only a disguise for what actually is an adware-type application distributed as an extension for Google Chrome, MS Edge, and other compatible browsers.
First of all, it is important to note that the Get Icons extension might not only be downloaded due to its alleged useful functionality but it also manages to find its way into users' systems via deceptive methods and is installed behind their backs. For example, a misleading ad might tell users that they need to update an already installed app.
Software bundling is also a commonly used tactic for potentially unwanted program distribution, where several apps are compiled into a standalone installer, and optional components are deliberately hidden from users' views during the installation process of the freeware.
The main goal of adware[1] is to deliver pop-ups, deals, offers, coupons, and other types of advertisements to users. In these cases, the advertised features of the app fade, as the developers only have one purpose in mind – to monetize users' clicks. In order to stop the unwanted activity, you have to uninstall the Get Icons extension from your browser.
| Name | Get Icons |
| Type | Adware, potentially unwanted browser extension |
| Alleged function | Provides accessibility to “beautiful icons on the internet” |
| Distribution | Software bundles, third-party websites, misleading ads |
| Risks | Installation of other potentially unwanted software or malware, personal data disclosure to third parties/cybercriminals, monetary losses due to fake offers |
| Removal | To get rid of adware, you can follow our removal guide below. If ads and other intrusive behavior do not stop, you should scan your computer with SpyHunter 5Combo Cleaner anti-malware and delete all threats automatically |
| Additional tips | Malware or adware infections can diminish the performance of your computer or cause serious stability issues. Use FortectIntego to remediate your device and ensure that the virus damage is fixed and data trackers removed automatically |
Operation
Unlike browser hijackers, Get Icons would not change the homepage, new tab, or the search provider. By doing so, browser hijackers commonly provide a sign to users that something is not correct – this is especially useful after being infected inadvertently. However, with adware, things are quite a bit different.
Upon installation, the Get Icons app asks for the following permissions:
- Allow this extension to read and change all your data on websites you visit
- Block content on any page.
By giving these permissions to the extension, you allow it to modify what and when you see things on various websites. Evidently, they are nothing more than advertisements and can be inserted into pages that would not have them initially. It is a very commonly used technique by adware creators, as many users would not even check the permissions before installing the app on their browsers or systems. Thus, we strongly recommend always checking what the app can do once it's installed on your device prior to allowing its installation.
In order to show ads that users are more likely to click on, most PUPs tend to collect user information. While the gathered data is mostly anonymous, some of it might not be. For example, the IP address is considered to be personal data in some jurisdictions or countries. Regardless, it is better to have fewer third-party tracking activities going on in the background.
In order to storm the intrusive advertisements and unwanted data tracking activities, you should eliminate the unwanted application from your device. Below you will find all the needed details to do just that thoroughly.
The correct Get Icons removal process
Ad-revenue is a very legitimate and widely-used monetization method used by many websites and applications. Therefore, you should not think that every app that shows some ads is automatically adware – that's not true. As long as ads do not interfere with the normal operation of the app and don't make you click on them accidentally by popping up randomly, it is not adware. Likewise, potentially unwanted apps are also distributed in deceptive methods, and it is one of the primary traits of such software.
That being said, we recommend removing all applications that show up on your system unexpectedly and don't fulfill their intended purposes. For example, if Get Icons promises to allow downloading various icons but serves intrusive ad campaigns, its usability and usefulness are debatable.
Uninstall the extension
Browser extensions are really easy to eliminate under normal circumstances. The easiest way to do so is by checking the “Extensions” button next to the URL bar. Since not all apps show up that way, you might have to access the browser's settings – check out the instructions below if you need help with that.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.

MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

MS Edge (legacy)
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clean the web browsers
Adware displays ads on various websites, and some of these can be very attractive to users they are shown to. This happens due to user data gathering practices – which websites they visit, search queries they type, links they click, and much more. This data is later used to generate ads that are crafted for particular user groups, sometimes making them buy products they otherwise wouldn't.
To collect this information, adware uses cookies, web beacons,[2] pixels, and other tracking technologies. Bits of information related to this process are stored locally on users' computers, thus security experts[2] highly recommend cleaning web data after the PUP/malware removal and also doing so regularly from time to time.
You can easily do this by employing a powerful maintenance and repair utility FortectIntego – it could also fix any system issues that the infection could have caused. Alternatively, follow these instructions:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies, and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Scan with anti-malware
Your final step is to make sure that your system is not affected by more dangerous threats, such as Trojans or rootkits. Malware can be particularly stealthy – not run active windows, hijack legitimate Windows processes, not show up in the installed program lists, etc.
Therefore, we strongly recommend you download and install SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable software in order to ensure that all the malicious processes and files are eliminated from the system at once. Anti-malware is one of the main ways to defend yourself against malware attacks in the future as well, so make sure you have it running at all times.
Avoid adware with these tips
As we already mentioned, users don't usually install potentially unwanted programs which disturb their web browsing experience or perform other disruptive or unwanted tasks. The distributors of adware and other shady software are aware of that, hence they often choose to use deceptive distribution methods to spread it to as many users as possible in order to retain the maximum amount of ad revenue. There are two main methods by PUP developers to distribute their software:
- Misleading advertisements
- Software bundles.
Software bundling is a time-proven technique that has been proved extremely successful over the years. In order to avoid being tricked by it, we recommend avoiding third-party websites where possible and choosing official sources instead. When downloading freeware, always pick the Advanced/Custom instead of Recommended/Quick settings in order to stay in control of what is being installed on your device.
Also, whenever you are redirected to a suspicious website (this usually happens on high-risk sites such as torrents), e.g., Phonenow.net, News-cetowu.cc, or Cusj.xyz, do not interact with it in any way. You may be asked to subscribe to push notifications [3] or download potentially dangerous software. Also, don't believe claims that something has expired, that needs to be updated, or that virus was found on your system – these are all scams and should be ignored.
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Adware. Investopedia. Source of financial content on the web.
- ^ Cookies and Web Beacons. NTT. NTT Communications.
- ^ Abigail Abesamis Demarest. What are push notifications? How the pop-up alerts sent by apps, devices, and browsers work. Business Insider. Global tech, finance, markets, media, healthcare, and strategy stories.
