Guer file virus (Bonus: Decryption Steps) - Recovery Instructions Included
Guer file virus Removal Guide
What is Guer file virus?
Guer ransomware locks your files by employing powerful encryption algorithm
Guer ransomware is a recent threat that has been spreading via cracked game files and software licenses on pirating platforms. It locates common files like documents, photos, videos, and encrypts them, trying to get the user to pay for access via cryptocurrency transfer platform. The encoding happens after they have attached .guer extensions on all of your data. The creators also allege there are no other options but their decryption tool, which costs $980. The group behind this threat can offer a discount to fake legitimacy and trust, so people are more encouraged to pay up.
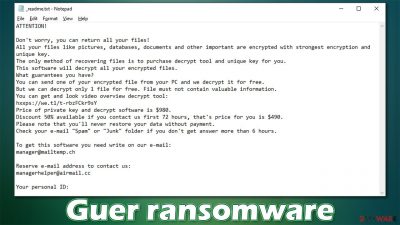
Guer virus infects your computer and locks your files with the help of encryption algorithms,[1] making them unreadable, so you cannot determine the value of a file. But there are other parts of the machine that can get affected by the infection. Once infected by the nefarious cryptovirus, you will receive the ransom demand message from the Djvu ransomware family creators and can see their demands in the text file – _readme.txt.
When you first see the ransom demanding message, it will display a text file that gives instructions on how to contact the cybercriminals who created this malicious software and pay them for their ransom. Victims are then asked to email helpmanager@airmail.cc or manager@mailtemp.ch in order for these attackers not only to decrypt all personal information but also restore computer functionality back into a normal state. That is a false claim, and you should never trust these criminals since they have the only purpose – to get your money.
| name | Guer ransomware |
|---|---|
| Type | Ransomware, file-locker, cryptocurrency extortionist |
| Family | Djvu/STOP ransomware |
| symptoms | Commonly used files like documents, pictures, archives, and other personal data get renamed and locked; a ransom note appears on the desktop and in affected folders; security-related software gets disabled, sites like that – blocked |
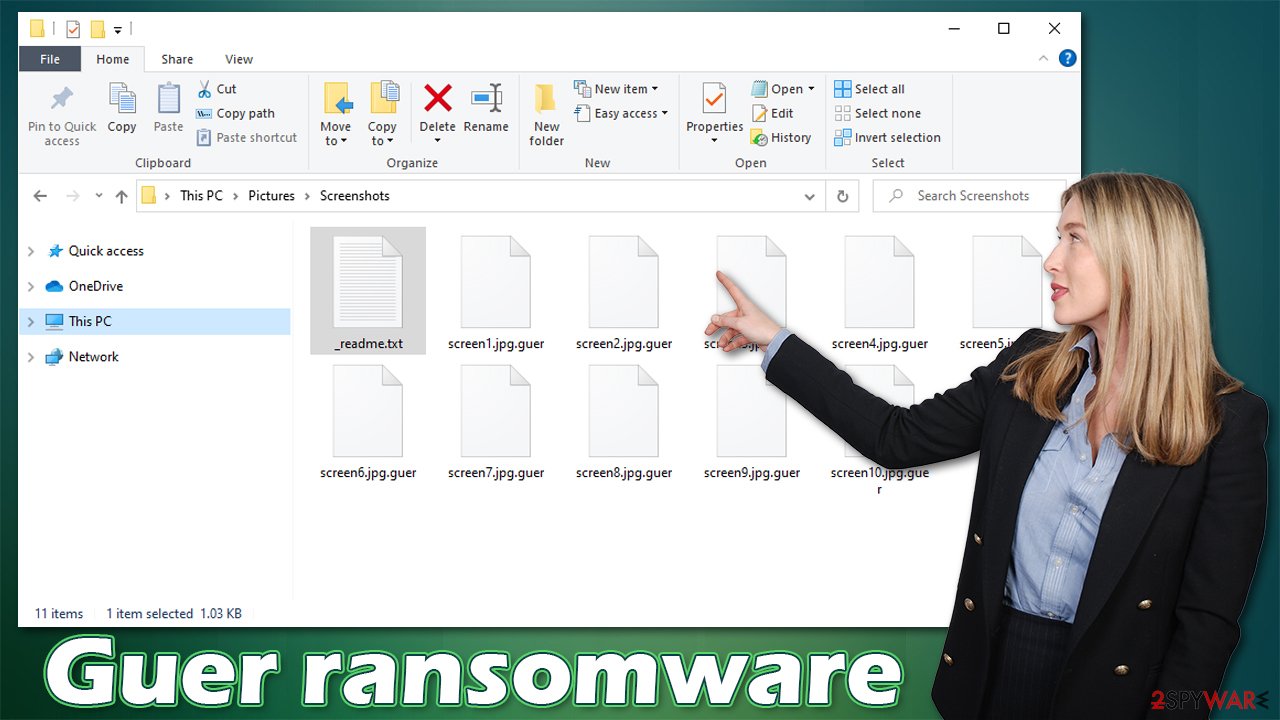
| Appended file extension | Non-system data is renamed by appending the .guer extension at the end of original names |
| Ransom note | _readme.txt |
| Distribution | Malicious pieces get downloaded from file-sharing platforms, torrent sites, or via email spam attachments[2] |
| Data recovery | Possible decryption software can be useful with some pieces; media files can get restored with the special tool. Other alternate options get listed below |
| Elimination | To fully remove the ransomware infection, you must use reliable anti-malware software that finds all pieces related to the virus and can eliminate them |
| System health check | The computer might not run smoothly after the ransomware removal if damaged pieces still left behind. We highly recommend using the FortectIntego to find virus damage and recover any system performance issues |
You should remove Guer ransomware instead of increasing the wealth of criminals responsible for spreading it. Manual removal is not an option as the infection might have spread its components throughout your system, and it would be impossible to find all of them without damaging other functions.
Luckily, there are a bunch of tools like antivirus programs that can help with this process. Many users rave about how efficient a security tool with real-time protection features has been against malware in general – many compliments on their cyber protection level. Get rid of the virus and all the related components first, and only then move to other file recovery and system repair options.
Even though the worst thing about the infection is encryption, you need to make sure that the machine is free of threats and data can be restored using alternate methods. Your first option when dealing with cryptocurrency extortion-based malware is to eliminate the threat. That can be done with anti-malware tools like SpyHunter 5Combo Cleaner or Malwarebytes because these programs are based on virus detection.
Paying the demanded sum is not recommended because threat actors often claim decryption tools that do not exist or cannot help with those files at all. This particular family was decryptable a few years back, but criminals added other methods and techniques, ensuring the more difficult recovery. The latest versions like Gujd, Hhqa, Zzla, Moqs cannot be easily decrypted. However, there are options for some users when the offline IDs get used when forming the unique decoding key.
Offline keys vs. Online keys when Djvu encrypts files
Every time a new variant of ransomware comes out, they change the key and ID to encrypt your files. These identifiers are often easy for experts or law enforcement agencies to identify because there is only one that can decrypt each type of file. This is the online ID method when each victim of the same threat can get a different, uniquely formed ID needed for the file recovery.
If you're an expert trying to get back into your system after it has been encrypted by this malware, all you need is the right private key which can only be obtained when law enforcements obtain those from the creator or criminals release the database. Payment should also provide this option, but that is not the best solution. This is the method that the latest versions like the Guer virus use nowadays.
Previous versions of the crypto-ransomware were able to encrypt files without connecting to their command and control servers – using offline keys. This creates less of an issue when trying to decrypt your files because you can just use one of those keys from another compromised system because they are similar enough. These decoding tools were created based on the offline ID method.
If you have infected your computer with one of the Djvu variants, you should try using Emsisoft decryptor for Djvu/STOP. It is important to mention that this tool will not work for everyone – it only works if data was locked with an offline ID due to malware failing to communicate with its remote servers.
Even if your case meets this condition, somebody from the victims has to pay criminals, retrieve an offline key, and then share it with security researchers at Emsisoft. As a result, you might not be able to restore the encrypted files immediately. Thus, if the decryptor says your data was locked with an offline ID but cannot be recovered currently, you should try later. You also need to upload a set of files – one encrypted and a healthy one to the company's servers before you proceed.
- Download the app from the official Emsisoft website.
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
![Guer file virus Guer file virus]()
- Press Decrypt.
From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
When you see that the system is not going to be decrypted, you can move on to other options. Unfortunately, these are limited since the ransomware is advanced and damaging. Your machine needs to be in pristine condition when you replace files affected by the virus using backups or copies of the data. Experts[3] always note that this is why virus removal and damage recovery are crucial.
Ways to repair the system after the infection
Guer ransomware is a dangerous virus that locks files and demands a ransom to unlock them. By removing the malware, you can prevent further damage as it spreads quickly throughout your system without warning. However, many parts of the machine can be altered, files and programs deleted or disabled to affect the removal and recovery procedures.
For example, an infection can alter the Windows registry database, damage vital bootup, and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by Guer malware, antivirus software is not capable of doing anything about it.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application can also fix various Windows-related issues that are not caused by malware infections, such as Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them.
![Reimage results Reimage results]()
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
It's important to note that it is unlikely the virus will unlock any files after encryption. The author of the ransomware wants you to pay a ransom in order for you to receive decryption software, which may be fake. To avoid being scammed and receive these threats we highly recommend avoiding torrent sites, paying attention to sources of programs and random emails in your box that have attachments.
Some malicious emails pretending to be from a legitimate company or law enforcement and say that you need to take particular actions via provided files or links. It is usually fake, malware-laden emails and pirated software that spreads all the payload files for Guer file virus, so avoid these platforms entirely.
Never underestimate the power of anti-malware tools like SpyHunter 5Combo Cleaner or security software. The application checks system and can avoid any malicious infections. Malwarebytes and other solutions like this can provide PUP blocking and real-time protection that keeps the PC virus-free.
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Tarcisio Marinho. Ransomware encryption techniques. Medium. Informational blog.
- ^ Barry Collins. Don’t Click On These 5 Dangerous Email Attachments. Forbes. Media company.
- ^ Virusai. Virusai. Spyware related news.








