Moqs ransomware (virus) - Decryption Steps Included
Moqs virus Removal Guide
What is Moqs ransomware?
Moqs virus renders your personal files useless until a ransom is paid
Moqs ransomware encrypts your files and forces you to pay for them via the cryptocurrency transfer platform. Malware authors claim that there are no other options but their decryption tool, which they can provide for $980 (although a 50% discount is also offered for those who decide to pay within 72 hours of the infection).
Many might consider this option, as it can be worth it if data on these devices is valuable or necessary to do one's job. One might feel as though they're being held hostage in a sense while waiting anxiously for this initial payment before access will finally be granted back into an account. Until then, all data has been lost when trying to save anything from the device infected with this virus. Fortunately, there are a few alternative methods that might be helpful when trying to return files for free – a Djvu decryptor and third-party recovery software might just work for some.
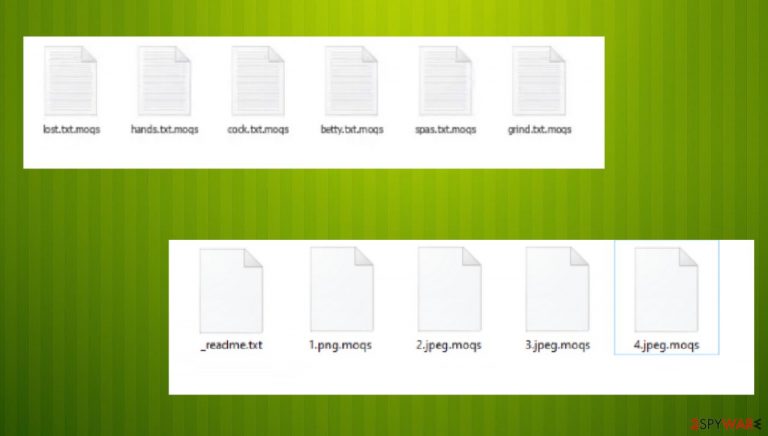
When the ransomware infects your computer, it will scan for pictures, videos, documents, and other types of files, which are then encrypted with a strong RSA encryption algorithm, and the appendix .moqs added to each of them. As a result, victims are unable to open any of the files located on their system, regardless of what they try.
Once the Moqs ransomware has encrypted your files, it will display a text file _readme.txt – it contains instructions on how to contact the cybercriminals who created this malware and pay the ransom. Victims of such attacks are asked to email helpmanager@airmail.cc or manager@mailtemp.ch with inquiries about what needs to be paid for the attackers not only to decrypt all personal information but also to restore the computer functionality into the normal state.
The text found in the ransom note:
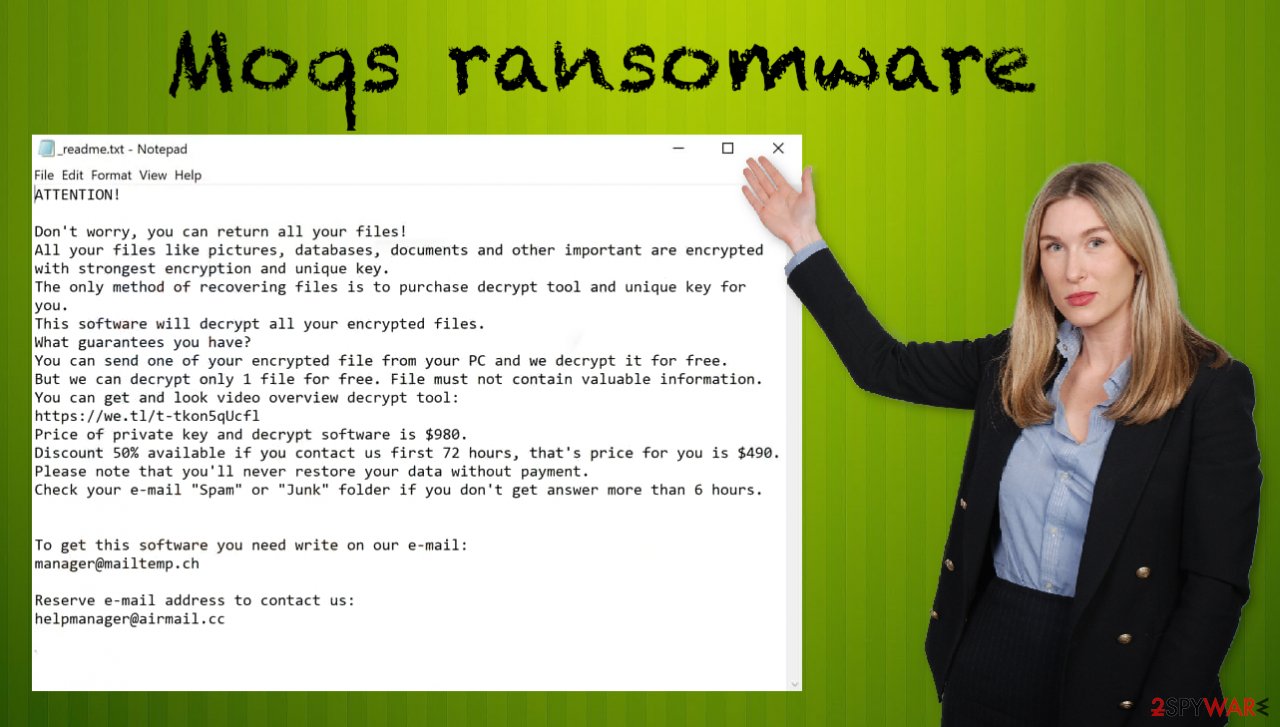
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-mNr1oio2P6
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
manager@mailtemp.ch
Reserve e-mail address to contact us:
helpmanager@airmail.cc
Your personal ID:
Unfortunately, paying is never a good option. Especially when it comes to a known ransomware family like Djvu/STOP that this piece belongs to. Once you see a pop-up demanding $980/ $490 worth of crypto, you should try to save files from the machine and move on to the ransomware elimination. Do not believe that discount offer either.
| Name | Moqs ransomware |
|---|---|
| Type | File-locking virus, crypto-malware |
| Family | Djvu/STOP ransomware |
| Appendix | .moqs gets added at the end of the original filename and file type indicator after the encoding |
| Ransom note | _readme.txt |
| Contact information | manager@mailtemp.ch, helpmanager@airmail.cc |
| Distribution | Files that spread malware payload can be added to malicious emails as attachments and come via pirating of software, game cracking |
| Removal | You need to eliminate the threat as soon as it is possible, and anti-malware tools can work for that the best |
| Recovery | Decryption is not possible since online IDs are no longer used and official decoding tools do not exist. Alternate methods include previously known decryptors, data recovery software. Malware damage and virus leftovers can be restored with FortectIntego |
In many cases, this family is reported to spread using software cracks and similar high-risk files, often downloaded from various websites. Users complain online that malicious threat affected their files after they download from pirated platforms or torrent sites.[1] Anti-malware software, if installed, would at the time block the malicious file, although users commonly believe that it is a false positive, and let it be executed, immediately starting the infection process of Moqs ransomware.
Additionally, some users might get infected after encountering malspam. Security experts suggest that victims are more likely to be tricked into opening malicious email attachments than falling for social engineering tricks used by cybercriminals. That means you should always avoid suspicious files attached to suspicious emails coming from unknown senders.
What difference do offline IDs vs. online IDs make to decryption?
Moqs virus is a piece of malicious software belonging to the family of money-extortion threats. This malware encrypts data and demands payment for the decryption tools that never get to the victims. In other words, files affected by the ransomware are rendered inaccessible/unusable, and victims are asked to pay for the access that may never be restored.
The family previously had versions that were possibly decryptable, but that ended quickly once developers improved the coding methods and started to rely on online IDs only. This method means that each particular victim gets the unique key formed during the encryption, making decryption impossible unless the key is obtained. This is the principle that latest versions like Gujd, Ufwj, Wwka, Zzla are based on.
If you have infected your computer with one of the Djvu variants, you should try using Emsisoft decryptor for Djvu/STOP. It is important to mention that this tool will not work for everyone – it only works if data was locked with an offline ID due to malware failing to communicate with its remote servers.[2]
Even if your case meets this condition, somebody from the victims has to pay criminals, retrieve an offline key, and then share it with security researchers at Emsisoft. As a result, you might not be able to restore the encrypted files immediately. Thus, if the decryptor says your data was locked with an offline ID but cannot be recovered currently, you should try later. You also need to upload a set of files – one encrypted and a healthy one to the company's servers before you proceed.
- Download the app from the official Emsisoft website.
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
- After Disclaimer shows up, press OK.
- Press Add folder at the bottom.

- Press Decrypt.

From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
The important step – thorough malware removal
Malicious actors are asking for a ransom and claim to care for you while the only purpose is money. Experts[3] always note how important it is to stay away from contacting them. Paying is not recommended, you should remove the infection instead.
In most ransomware infections, decryption is impossible without interference from the cybercriminals responsible or law enforcement. Since file recovery is only possible with third-party tools, you must remove the infection fully beforehand. It might be possible to wait for the updated decryption tool by storing some files on the external device, but you need to remove the virus as soon as possible if you want to recover the functionality of the device.
Regardless of the circumstances, it is expressly advised against communicating with and/or meeting the demands of criminals. Despite paying, victims often do not receive the necessary tools to recover the data. Therefore, they experience financial loss and their files remain encrypted – virtually worthless. But restoring files on the machine where the virus is still active can cause damage.
Removing Moqs ransomware from the operating system prevents it from further encryptions. Unfortunately, removal will not restore already affected data. However, there are a few methods that could be used to decrypt the files. You should rely on anti-malware tools like Malwarebytes that can detect this threat and other more Advanced pieces of malware.
Programs like SpyHunter 5Combo Cleaner are the ones that can find all pieces of this ransomware and terminate the processes running in the background. There are various places where infections can be hidden. Unfortunately, incorrect removal can lead to data loss when you restore those files.
Additionally, the infection itself alters various settings, disables programs, damages files. Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup, and other sections, delete or corrupt DLL files, etc.
Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstallation is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
File recovery options and .moqs file decryption alternatives
There are various forms of ransomware. Some of them, once installed on the target computer, encrypt files with strong encryption algorithms (like RSA-2048 and AES-128) and then demand a ransom payment from the victim to decrypt those files.
If no ransom is paid within the specified time frame, the private key required for decryption is deleted or destroyed, thus making it impossible to recover encrypted data without paying a ransom. The affected user can restore data only if he/she keeps backups that do not use encrypted storage media.
Other ransomware may simply block access to their own executable file (“e.g.”, by creating infinite loops in code), uninstall themselves once they have been executed, or delete important system files like drivers which will cause the computer to freeze on next reboot. Such threats can damage functions of the machine, not all files or common pieces.
The primary aim of this ransomware is to use military-grade encryption algorithms to temporarily lock files on the victim’s computer until a ransom is paid. It is obvious that people keep their important files on either personal or work computers, and the idea of losing all of them in a few minutes is scary. Cybercriminals expect that victims will be willing to do anything it takes to recover these .moqs- marked files, including paying a ransom. However, that is not recovering your files.
Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you. Therefore, we suggest trying regardless of which ransomware attacked your computer. Including now when your files get affected by the ransomware.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

The most important fact about ransomware is that even though those common files get encrypted, the worst thing that happens is caused on the machine. You can get options for file recovery and even decryption of those files, but the data that gets altered directly on the computer cannot be easily restored. The same goes for the consequences of the infection and virus files placed in various parts that users cannot find manually. Make sure to keep tools like SpyHunter 5Combo Cleaner or Malwarebytes on the machine and up to date to avoid infection removal procedures in the future.
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Hackers Crack Pirated Games with Cryptojacking Malware. Threatpost. IT and cybersecurity news.
- ^ About Djvu/STOP ransomware. Emsisoft. Support forum.
- ^ Virusai. Virusai. Virus removal guide and spyware related news.
