Love2Lock ransomware / virus (Simple Removal Guide) - Decryption Methods Included
Love2Lock virus Removal Guide
What is Love2Lock ransomware virus?
Love2Lock malware is under analysis at the moment: what is known about this virus so far?
Love2Lock virus[1] is nothing else but a malicious ransomware[2] virus, which seeks to encrypt files in order to convince the victim pay a ransom to get them back. Once it gets installed on the computer, it soon begins scanning all folders and encrypting target files. The program has a list of target file extensions, and as soon as it finds a file with a matching one, it encrypts it. Although some victims believe that nothing is impossible, we are afraid that this rule doesn’t apply to recovery of files encrypted by ransomware viruses. Typically, such malicious programs use complicated encryption codes and then corrupted files become completely inaccessible. They can be recovered with Love2Lock decryption key[3] only, but this code is securely stored on cybercriminals’ private servers, so it is impossible to reach them.
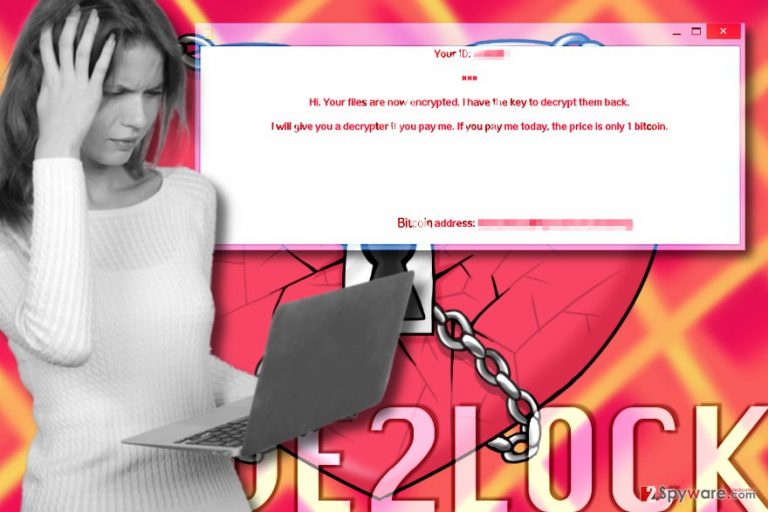
Love2Lock virus securely encrypts files and then creates and saves a note on the computer’s desktop. Criminals ask the victim to pay a certain amount of money in exchange for the decryption code, however, paying the ransom gives no guarantee that files will be recovered. In most cases, scammers simply disappear with the money, leaving victims in limbo. Love2Lock uses a combination of AES[4] and RSA ciphers to encode files, and it is not possible to crack these algorithms. However, the virus is under analysis at the moment, and the article will be updated soon. Therefore, we suggest you remove Love2Lock ransomware from the system and try data recovery options explained below the article. For Love2Lock removal, we recommend using anti-malware software, for instance, FortectIntego.
How can I secure my PC from ransomware?
Love2Lock ransomware is believed to be distributed via deceptive emails, malware-laden ads and most likely exploit kits[5]. While the last distribution method might not be associated with this particular virus, you should learn more about it in order to prevent Cerber or Spora ransomware attacks. The first distribution method that we mentioned is based on deceptive messages that cyber criminals precisely prepare. They compose convincing and legitimate-looking messages and attach some malicious files to the email, and if the victim opens such attachments, he allows malware to infiltrate the computer system. The virus then successfully encrypts all data and starts threatening the victim. Malware-laden is also a matter of concern. Cyber criminals manage to infect legitimate ad networks and demonstrate malicious ads online even through legitimate websites. If you want to prevent ransomware attacks, you must protect your system in advance. The first thing you should do is to install a reliable anti-malware software. Next, create a data backup (on an external hard drive, USB or another data storage device). Finally, try to stay away from suspicious emails, websites, and ads online.
How to remove Love2Lock ransomware?
In need of Love2Lock removal instructions? Then you have come to the right website – we have already prepared an informative guide on how to remove Love2Lock from your PC. First of all, you will need to make sure that the computer is in the right mode and you can start the removal procedure safely. Therefore, you will need to reboot your PC into Safe Mode with Networking. Next, you will have to install/update antivirus or anti-malware software, and finally, you will need to perform a full system scan. For smooth uninstall procedure, we suggest following these instructions:
Getting rid of Love2Lock virus. Follow these steps
Manual removal using Safe Mode
As we have mentioned before, you need to restart your computer to begin Love2Lock removal. Follow guidelines listed below.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Love2Lock using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Love2Lock. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Love2Lock from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Speaking about data recovery, we can only say that the most effective way of recovering data is using a backup. However, many users do not use them as they do not consider them useful. If you do not have a backup, try these data recovery options.
If your files are encrypted by Love2Lock, you can use several methods to restore them:
Data Recovery Pro
Data Recovery Pro is a useful application that can help you to recover files encrypted by Love2Lock ransomware. Although we cannot guarantee that it can recover your files, it can restore various corrupted/deleted files, so it is definitely worth to try it.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Love2Lock ransomware;
- Restore them.
Windows Previous Versions(System Restore)
Users who have a restore point set up can use Windows Previous Versions to restore their files.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Love2Lock and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Tweet by @struppigel. Twitter. Social Network.
- ^ Cerber ransomware becomes the main concern of security professionals. eSolutions. Official news fro eSolutions team.
- ^ Lucian Constantin. Professionally designed ransomware Spora might be the next big thing. Computerworld. IT news, careers, business technology, reviews.
- ^ Advanced Encryption Standard. Wikipedia. The Free Encyclopedia.
- ^ Exploit Kits. F-Secure Labs. Knowledge Base - The latest research in threats and technology.







