Mystic ransomware / virus (Improved Instructions) - Removal Guide
Mystic virus Removal Guide
What is Mystic ransomware virus?
Mystic crypto-malware links to Crypt888 ransomware?
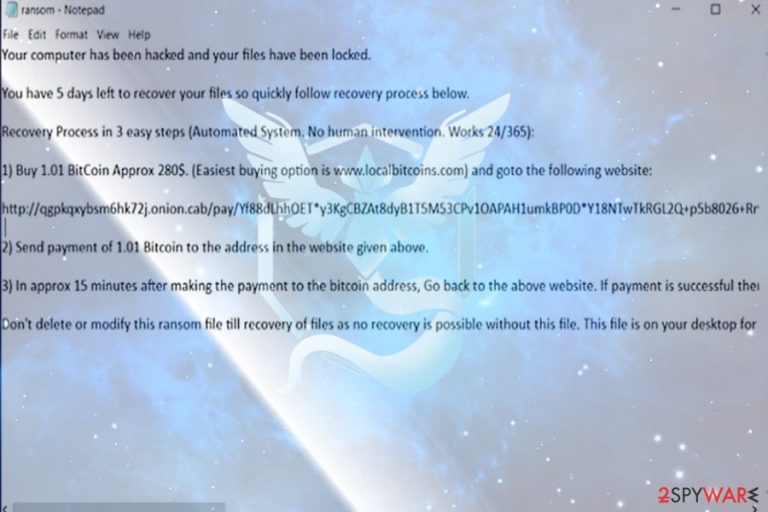
Mystic virus functions as a file-encrypting threat. It manifests unusual behavior for ransomware since it does not append any file extensions[1] nor presents its GUI. Nonetheless, it drops its ransom.txt message which contains brief information about the malware.
Besides the demands to pay 1.01 BTC ransom (approximately $3900), the message also states that the file recovery is simple if a victim follows the indicated steps. It also includes a link to the payment onion site, which, at the moment, does not work properly.
Now the malware is detectable as Gen:Variant.Kazy.21167, Backdoor.Graybird, Ransom_MYSTIC.A, W32/Trojan.BKHV-5194, etc. Regarding the detection names, there has been another ransomware which functioned as Kazy trojan – GrodexCrypt.
The latter has been coded on the pattern of Crypt888. Note that the latter is a well-known ransomware group. Though its developers release new versions, you can try decode data using Crypt888 free decryption software created by AVG experts.
Considering the fact that the link provided in the ransom.txt does not work properly and the amount of required ransom , it would be better to remove Mystic virus. You can do so with the assistance of FortectIntego or Malwarebytes.
Reference to Pokemon Go?
The very name of the crypto-malware possibly pertains to the Team Mystic, one of the teams accessible for Pokemon Go level 5 players. Though it might give a slight insight to the personality of the perpetrator, their identity remains in secret.
The malware tends to encrypt files present on the desktop, even though it leaves its ransom note among system files. It also launches a series of processes. Here are some of them:
- ole32.dll
- netapi32
- rpcrt4.dll
- apphelp.dll
- clbcatq.dll
- comctl32.dll
Mystic ransomware also accesses Remote Access Connection Manager (RASMAN) which enables the connection to a remote server. Though the crypto-virus is still under development, it is not recommended to waste time on remitting the payment. There is no guarantee that you will succeed in file recovery. Therefore, Mystic removal might be a better solution. 
Avoiding the encounter with ransomware
If you are interested in rasomware and cyber security, you probably already know that the most popular distribution method is malspam. Likewise, the highest probability to execute Mystic hijack is open its malicious email.
At the moment, it is not known what specific technique, i.e., whether the developers disguise the malware under fake invoice or account verification inquiries, is used. In any case, pay attention to the emails which are supposedly sent by official institutions.
Crooks disguise under the representatives of official institutions and urge potential victims to open the corrupted email as soon as possible. If you receive such message which tries requires immediate caution, act the opposite.
Evaluate the authenticity of the message and verify the sender before opening any attached files. Some malware security tools also help you battling the flow of spam emails.
Get rid of Mystic malware
Dealing with a crypto-virus is never an easy process. Regarding the features of this malware, manual Mystic removal might be futile. Update the security tool and scan the device. In case the virus prevents you from launching the security program, use the below instructions.
After you eliminate the infection from Windows, attempt data recovery. Some of the options are discussed below. Note that the virus does not only target English-speakers, but may attempt to assault Pokemon Go[2] users in Poland, France, or Denmark[3].
Getting rid of Mystic virus. Follow these steps
Manual removal using Safe Mode
Reboot the device in Safe Mode to access the security application and remove Mystic ransomware.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Mystic using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Mystic. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Mystic from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Mystic, you can use several methods to restore them:
Data Recovery Pro method
This is one of the alternative solutions to restore damaged data. Though the program was designed to restore files affected by system failure, you may succeed in restoring data encrypted by Mystic virus.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Mystic ransomware;
- Restore them.
How does ShadowExplorer work?
This program uses shadow volume copies. There is no information whether the malware deletes them in advance, so you may have a chance.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Mystic Decrypter
At the moment, there is no decryption software for this version released.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Mystic and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ DemonSlay335. ransom.txt. Pastebin. #1 paste tool since 2002.
- ^ Aaron Brown. Pokemon Go WARNING - Millions of players hit by terrifying new malware. Express. Home of the Daily Sunday Express.
- ^ Remove malware. Undenvirus. News and malware removal guides in Dannish.







