“New Voice Message In Your Office365 Extension” email scam (fake) - Free Instructions
“New Voice Message In Your Office365 Extension” email scam Removal Guide
What is “New Voice Message In Your Office365 Extension” email scam?
“New Voice Message In Your Office365 Extension” is a fake email disguised as an alert from Microsoft
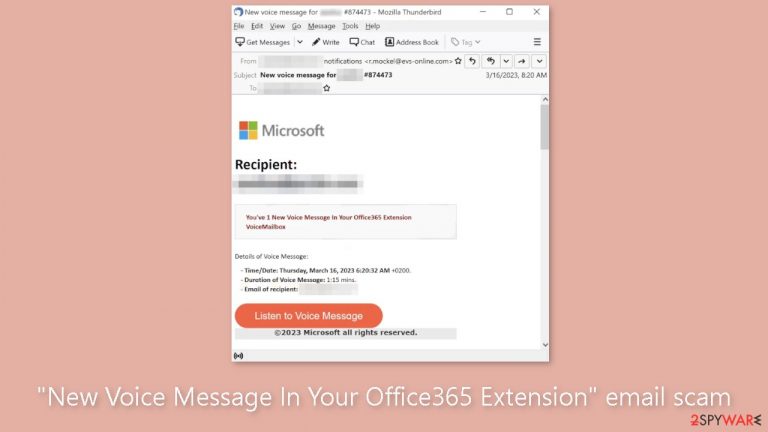
“New Voice Message In Your Office365 Extension” – a phishing[1] scam that attempts to trick unsuspecting users into revealing their login credentials. Phishing is a type of cyber attack in which users are duped into providing sensitive information such as passwords, credit card information, and other personal information. Cybercriminals frequently use social engineering[2] techniques such as phishing emails, phone calls, and text messages to trick victims into clicking on malicious links or downloading malware.
In this spam email, the attacker hopes the recipient will click on the “Listen to Voice Message” link, which will take them to a phishing site. When the victim arrives at the page, they may be prompted to enter their login credentials, which the attacker can then steal and use for malicious purposes.
| NAME | New Voice Message In Your Office365 Extension |
| TYPE | Phishing, scam |
| SYMPTOMS | Users receive an email supposedly from Microsoft, saying that they have a new voice message |
| DISTRIBUTION | Deceptive emails |
| DANGERS | The email scam can lead to unauthorized online purchases, changed online account passwords, and even identity theft |
| ELIMINATION | Scan your machine with anti-malware tools if you downloaded any suspicious files |
| FURTHER STEPS | Use FortectIntego to clear your browsers and get rid of any remaining damage |
Social engineering
The full message in the “New Voice Message In Your Office365 Extension” fake email:
Subject: New voice message for ********* #874473
Microsoft
Recіpient: *********
You've 1 New Voіce Messɑge In Your Office365 Extension VoіceMailbox
Detɑіls of Voіce Messɑge:
– Tіme/Dɑte: Thursday, March 16, 2023 6:20:32 AM +0200.
– Durɑtіon of Voіce Messɑge: 1:15 mins.
– Emɑіl of recіpіent: *********Lіsten to Voіce Messɑge
©2023 Microsoft all rights reserved.
The spam email campaign in question is intended to trick recipients into clicking on a link that leads to a phishing website. The ultimate goal is to obtain the recipient's email address and password, which can then be used to conduct a variety of fraudulent activities such as identity theft, malware distribution, and financial scams.
Cybercriminals frequently use spam emails to obtain sensitive information from unsuspecting victims. They use social engineering techniques to instill fear or urgency in the recipient, causing them to act quickly and without thinking.
Phishing emails are the most common type of spam email, as they attempt to trick the recipient into giving up their login credentials or other sensitive information. Malware emails, which contain infectious files or links that can infect the recipient's computer with malware, and scam emails, which offer fake products or services in exchange for money, are two other types of spam emails.
Potential dangers and how to avoid them
Spam emails frequently include malicious links or attachments that, when clicked, can install malware or spyware on the victim's device. Once installed, this malware has the ability to steal sensitive data, log keystrokes, and take control of the device. Other spam emails may attempt to gain access to the device by exploiting vulnerabilities in the recipient's email client or operating system.
To avoid becoming a victim of spam emails, take the following precautions:
- Do not click on links or download attachments from suspicious or unknown senders. Always verify the sender's identity before opening any email.
- Be cautious of urgent or threatening messages that ask you to act quickly or provide sensitive information.
- Install reputable antivirus and antimalware software on your device, and keep it up to date.
- Regularly back up your data to prevent loss in case of a security breach.
- Use strong, unique passwords for all your online accounts, and enable two-factor authentication whenever possible.
Clear your browsers and fix the OS
After a malware infection, performance, stability, and usability issues are to be expected, to the point where a full Windows reinstall is required. These infections can modify the Windows registry database, harm vital bootup and other sections, delete or corrupt DLL files, and so on. When malware corrupts a system file, antivirus software cannot repair it.
That is why FortectIntego was created. It can repair a significant portion of the damage caused by an infection like this. Blue screen errors,[3] freezes, registry errors, damaged DLLs, and other issues can render your computer completely inoperable. You can avoid reinstalling Windows by using this maintenance tool. So, if you suspect a virus infection and are experiencing other unwanted symptoms on your device, you should use it.
Another useful feature of this software is the ability to delete cookies and cache. Cookies can be used by any website or browser plugin to track your activity, such as the pages you visit, links you click on, items you buy online, and so on. If you clicked on any links in the spam email, you should consider this possibility carefully.
Check your system for malware infections
If you contacted the scammers and gave them access to your machine, you might have been infected by malware. We recommend using SpyHunter 5Combo Cleaner or Malwarebytes security tools that will scan your machine, eliminate it, and prevent such infections in the future by giving you a warning before a malicious program can make any changes.
Crooks often disguise their malicious programs as “handy” tools so they would be more difficult to identify for the average user. People also often fail to eliminate all the related files and entries which could lead to the renewal of an infection. The program could have any name and icon, so this step is best performed by anti-malware tools.
However, if manual removal is what you prefer, we have instructions for Windows and Mac machines:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

How to prevent from getting spam tools
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Phishing. Wikipedia, the free encyclopedia.
- ^ Social Engineering. Imperva. App Security.
- ^ Tim FIsher. Blue Screen of Death (BSOD). Lifewire. Software and Apps.
