Ooss ransomware (Free Guide) - Decryption Steps Included
Ooss virus Removal Guide
What is Ooss ransomware?
Ooss ransomware is the version of well-known ransomware that spreads around via pirating services and with the help of infected files
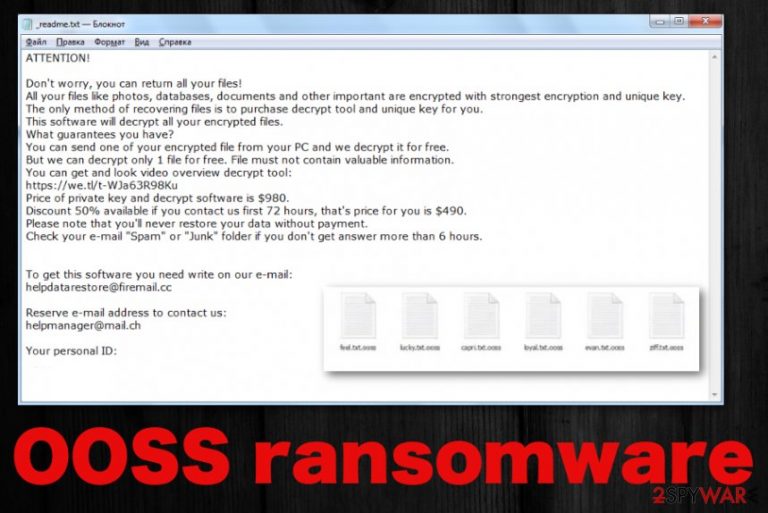
Ooss ransomware virus is the version that can permanently damage your files because there are not many other options. Even though, Emsisoft released a decryptor for Djvu, the software works for victims that have the variant using offline keys. Typically, such victims' ID ends in t1, so you can easily identify that. However, right now there are little to none samples that use offline IDs for encryption. When your files get marked using .ooss file appendix, you can be sure that there is a cryptovirus on your device, so get a proper anti-malware tool and make sure to clean the traces of this malware, so it can be terminated and files restored on the clean and safe machine.
| Name | Ooss ransomware |
|---|---|
| Family | STOP virus/ Djvu ransomware |
| File marker | .ooss – the file extension that comes after the original file name and appendix indicating the type of the particular data. Once files get encrypted they become useless and unreadable, so you can see which ones are damaged due to this marker |
| Ransom note | _readme.txt – the file that delivers a message from malicious actors and contains ransom demand, contact information, instructions on how to get cryptocurrency that is their preferred payment method |
| Ransom amount | The amount demanded ranges from $980 and $490 that is the discounted offer for people why contact criminals in the first 72 hours after the ransom note get received |
| Distribution | The family is known using pirated software and malicious files included in such packaged mostly,[2] but can also infect machines by sending emails with malicious file attachments and links redirecting to malware-laced sites |
| Danger | This is the threat that focuses on money demands, so when you pay, but your files still remain encrypted, you lose your money and data. Also, instead of recovering your files, criminals can send you additional malware and affect the machine further |
| Elimination | Ooss ransomware removal is the process that needs anti-malware tools because ransomware cannot be found manually and you need to thoroughly clean the system to ensure that files will get restored on a safe system |
| Repair | To get system files and functions affected by the virus repaired, you also need a program. Anti-malware tool cannot fix virus damage, so you should rely on system programs like FortectIntego or a PC optimizer that can possibly indicate issues with your settings and OS functions and repair needed files in the registry and so on |
Ooss ransomware belongs to the family of malware that hasn't altered the ransom note file for years now. _readme.txt file delivers the same message and is named the same for most of the time that the Djvu family is observed. The message gets slightly changed because contact emails differ from version to version. However, the same contact emails get displayed for at least three or four versions at the time.
The ransom note added on the desktop after OOSS ransomware encryption:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-7YSRbcuaMa
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
datarestorehelp@firemail.ccReserve e-mail address to contact us:
datahelp@iran.irYour personal ID:
However, no one ensures that after the email, Ooss ransomware developers going to send you that decryption software or a key needed for file restoring. You shouldn't consider paying or contacting these criminals at all because they cannot guarantee that. In most cases, even big targets, companies that get affected by such ransomware decide not to pay and recover their networks themselves without risking again.[3]
Experts[4] always recommend recovering files with your backups after the Ooss ransomware removal instead of paying these hackers because secondary encryption can permanently affect your photos, videos, documents, and other common files. Despite the file-locking process, this family can possibly load additional malware like info-stealing trojans and more dangerous threats. 
The same goes for Ooss ransomware virus damage that cannot be indicated by the AV tools even. Anti-malware programs cannot recover your files, or fix system damage, so go for a system optimization tool a cleaner, something like FortectIntego and ensure that the machine is checked yet again. This way, you can repair needed files in system folders and recover default settings of the startup, registry entries.
File locking process that Ooss ransomware first runs on the infected system relies on army-grade encryption algorithms that allow threats to change the original code of a file, so it cannot be used again and becomes unopenable. There are many algorithms and methods that can be used in such procedures, so the latest changes and improvements made by malicious actors caused huge differences in the persistent and decryption possibilities.
Previously other versions before Ooss ransomware were decryptable, and new versions each week were not that scary since many victims got their files repaired thanks for the offline keys and some researchers. When cybercriminals use offline IDs nowadays, victims can also get their files restored since one obtained key can restore the same type of data for many other devices.
When the connection to malicious hacker-hosted C&C server is not made, Ooss ransomware relies on offline ID, and these ones get changed with each virus variant – extension. Everyone who has their files encrypted by the save version has the same ID and can help others to get their data back.
However, the summer of 2019 ended with significant changes in the RSA encryption method used by these criminals Ooss ransomware. Online keys get used for pretty much each new release, and virus connects to the command and control servers to get randomly generated victim ID that is unique for each victim. In such cases, the only way to get files recovered is a proper decryption tool that relies on the same technique as the encryption that was launched in the first stage of the ransomware attack. Unfortunately, for this version you have the only solution – restore files using data backups. 
Malware identification flaws help spread ransomware payload files online
There are many ways that criminals use for delivering their shady programs and when it comes to such malicious programs like crypto-malware, it is extremely uncommon to even notice the infection. When malicious script with ransomware payload is injected on the file that gets attached to email notifications the encryption starts immediately after opening the infected document or visiting the link. It happens due to malicious macro viruses that get triggered by the user why receives the scammy message.
However, this particular family is known for using another flaw of online users to their advantage – paying less attention to details and relying on illegal activities like pirating and torrent service. When the person downloads the license key for original software or cheatcodes of video games malicious files including ransomware dropper or virus that infects the system with cryptovirus directly get loaded.
Choosing legitimate sources for programs and avoiding torrent sites, pirating services, shady sites, and other illegal activities can help avoid these infections. Also, clean the email box more often, be more suspicious, remove received emails that raise questions.
Get rid of the .ooss files virus completely with AV tools
Make the system malware-free again and terminate the Ooss ransomware virus with anti-malware tools because such software can help eliminate anything related to the intruder and additional threats that may run in the background without your knowledge. Tools designed to scan the machine fully can check many hidden places.
Ooss ransomware removal gives the best results for you when you use proper tools like SpyHunter 5Combo Cleaner, or Malwarebytes. These are security programs that can find, detect, and remove the ransomware and other possibly dangerous intruders that you cannot notice yourself. These programs are not the ones that could recover encrypted files, but you need to terminate the virus to have a totally secure machine.
When you remove Ooss ransomware using anti-malware tools, professional software can eliminate traces and potentially harmful parts of the threat. However, after that, you still need to repair damage made in system folders with tools like FortectIntego, and only then worry about data recovery. When you double-check and ensure that the system is clear, rely on your data backups or third-party software, and restore encrypted data.
Getting rid of Ooss virus. Follow these steps
Manual removal using Safe Mode
Reboot the machine in Safe Mode and get rid of the Ooss ransomware by scanning the system with AV tool
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Ooss using System Restore
System Restore feature should help with virus termination because this function can recover the system in a previous stage when malware was not running
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Ooss. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Ooss from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Ooss, you can use several methods to restore them:
Data Recovery Pro – the program capable of restoring your encrypted files
When users accidentally delete their files or threats like Ooss ransomware damage the data, Data Recovery Pro comes for the rescue
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Ooss ransomware;
- Restore them.
Windows Previous Versions feature restores data individually
When System Restore is enabled, you can rely on Windows Previous Versions feature for your encrypted files
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer is the method helpful for Ooss ransomware encrypted files
Shadow Volume Copies should be left untouched if you want to use this method for your encrypted files
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Particular decryption tool for Ooss ransomware is not developed, but DJVU decryptor may help
Try this decryption tool designed for Djvu versions using offline IDs
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Ooss and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Michael Gillespie. .ooss v208 report. Twitter. Online social media paltform.
- ^ Cracked software versions are harboring Djvu Ransomware. Cyware. Malware and vulnerability reports.
- ^ Cynthia Brumfield. To pay or not pay a hacker’s ransomware demand? It comes down to cyber hygiene. CSOonline. Technology news.
- ^ Bedynet. Bedynet Spyware related news.







