Redlight-mc2.club ads (Free Instructions)
Redlight-mc2.club ads Removal Guide
What is Redlight-mc2.club ads?
Redlight-mc2.club is a deceptive website designed to make you install questionable software
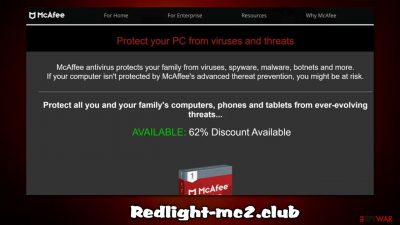
Redlight-mc2.club is a malicious website one can encounter while browsing the web on Google Chrome, Mozilla Firefox, MS Edge, or another web browser. The main goal is to show visitors misleading messages about their computer security and make them buy dubious software – McAfee or Norton. While both names are of legitimate security vendors, there is no guarantee that the version that is promoted is; it could also be malware, so installing any apps through this website is a high risk to computer safety.
Please ignore the messages that come from Redlight-mc2.club or Redlight-mc1.club. Both of these sites were created by malicious individuals that have nothing to do with the original security software maker and are trying to push insecure applications, profiting from purchases in the process.
Although the notifications about computer infections are fake, you should not dismiss the probability of the adware infection, as it is one of the main causes why users end up on malicious scam websites. Below we will explain how the scam operates and how to ensure your system is clear from potentially unwanted applications and malware.
| Name | Redlight-mc2.club |
|---|---|
| Type | Scam, adware, redirect |
| Operation | Claims that the memory is full and suggests to free it by offering insecure software |
| Distribution | Software bundles, malicious redirects, ads |
| Symptoms | Redirects to suspicious websites that hold plenty of commercial or scam content; fake messages offer to download malicious software; ads plague every visited website; unknown extension or program installed on the system |
| risks | Malicious software might lead to dangerous websites, resulting in financial losses, malware infections, and more |
| removal | To delete unwanted apps manually, you can follow our removal guide below. You should also ensure that your system is clean and scan it with powerful security software, such as SpyHunter 5Combo Cleaner |
| Further steps | Cleaning web browsers is one of the secondary things you should do after PUP/malware removal to secure your privacy. You can use FortectIntego to do it quickly |
Fake security notifications are often used to promote PUPs and malware
Considering that there are almost two billion websites[1] active at any time, it is important to note that not all of them were created to operate legitimately. There are plenty of fake websites that were created for one and only purpose – to scam users into performing actions they would not, would they know the consequences of their actions.
Redlight-mc2.club is your typical scam website that relies on scare tactics – it tries to intimidate users by claiming that their systems have been infected with viruses. Here's the message you might encounter after being redirected to the site:
McAfee
Your PC is infected with 5 viruses!
ACTION REQUIRED!
Your Norton Subscription Has Expired!
Renew now to keep your pc protected.
If your PC is unprotected, it is at risk for viruses and other malware.
The scammers are attempting to catch users off guard and make them concerned about their computer safety. To make it more believable, they create a fake website that looks like that of Norton or McAfee. In reality, the deception is soon to be seen if one would try browsing the pages within site – they simply don't work. There are plenty of similar scams around; for example, “Pornographic virus alert from Microsoft” tries to impersonate the tech giant Microsoft while Google Chrome Critical Error tries to copy Google alerts.
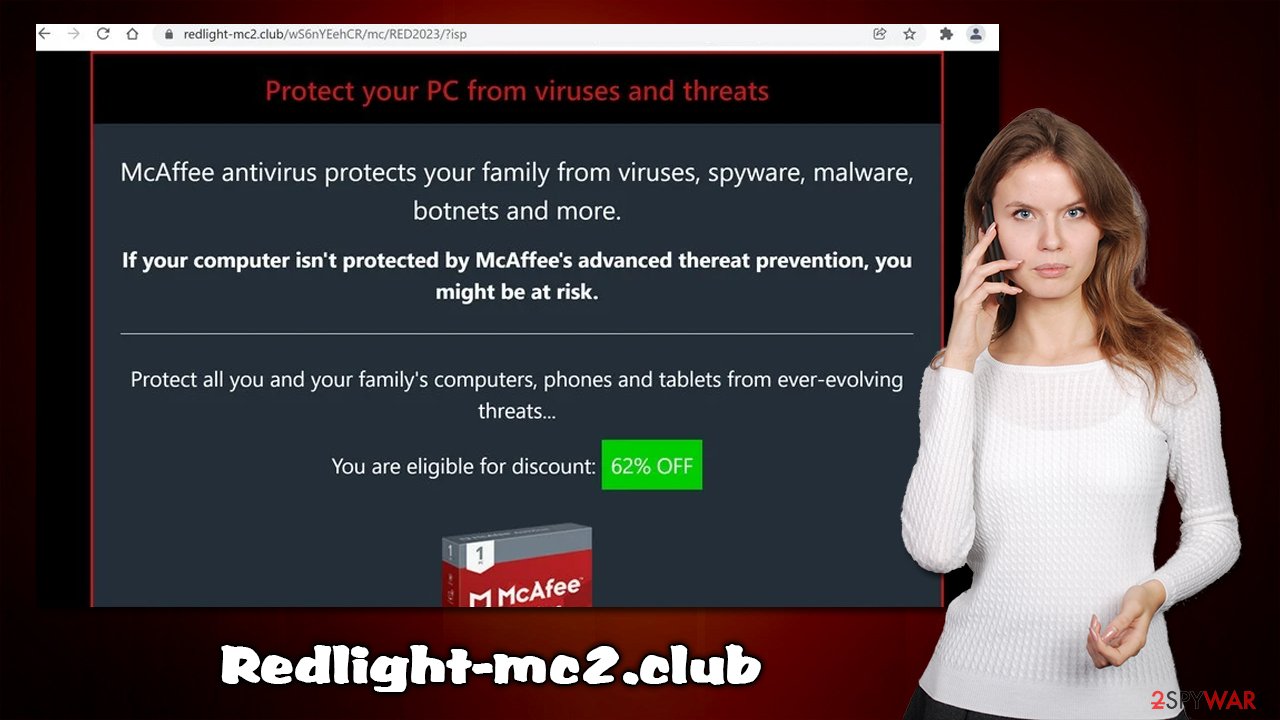
One of the main indicators that the page is fake is its URL address – Redlight-mc2.club. If you have been redirected to a website unexpectedly, you should never trust its contents, especially if it claims that something is missing, needs to be updated, or that you won a gift card, or similar. Always check the web address within Omnibox, as it usually indicates clearly that the website is fake. If in doubt, close the tab and look up the official website through your search engine.
If you proceed with downloading anything offered on scam sites, the consequences can be dire. You might be scammed into providing your personal information, such as credit card details, or download software that would infect your PC and perform malicious activities behind your back.
How to thoroughly check your system for adware
If you have not interacted with Redlight-mc2.club or any other scam website for that matter, you should generally be safe. While, technically, it is possible to install malware automatically on your system without your direct input, this can only happen thanks to a software vulnerability that should be present on your device. This is why it is vital to update all the software, including the operating system, as soon as security patches are deployed.
Nevertheless, we strongly recommend you proceed with the steps below to ensure that your system is not infected with adware, other PUPs, or even malware.
1. Scan your computer with a legitimate security tool
First of all, the easiest way to make sure whether your system is infected is security software, for example, SpyHunter 5Combo Cleaner or Malwarebytes. Anti-malware is your first line of defense not only against potentially unwanted programs but also Trojans, ransomware,[2] rootkits, and other malicious software. Just make sure that the security tool is up-to-date and never ignore its warnings.
2. Check the apps installed on the system
An anti-malware scan is a great way to check whether malicious files are present on the system. It checks your whole operating system and removes all the malicious components at once. However, potentially unwanted programs are in the gray area, so not all security vendors recognize all PUPs. It also highly varies based on what criteria is used. Nevertheless, don't forget to check your device manually as well:
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
![Uninstall from Mac 2 Uninstall from Mac 2]()
3. Remove unwanted extensions
Adware and browser hijackers[3] are particularly known to be spread as browser extensions. They are easy and cheap to produce, all while providing enough functionality to insert ads, gather user data for marketing purposes, and perform other activities once installed.
Therefore, you should always pay attention to the installed extensions section within your browser. Keep in mind that even add-ons you trusted for years might become rogue, so if you are experiencing intrusive ads everywhere you go, you might want to try uninstalling all the extensions and seeing which one is at fault.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
4. Clean web browsers
The last step is ensuring that your browsers are cleaned properly. Once the adware is installed on the system, it drops cookies and other tiny items on your system, which interact with the web browser to track you. For example, websites you visit, links you click, ads you interact with, and a lot of technical data can be collected and sent to third parties automatically.
Therefore, after you remove adware or/and malware from your system, ensure that browser caches are removed as well. If you would rather do that automatically, we recommend using PC repair and maintenance utility FortectIntego for the job.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ How Many Websites Are There?. WebsitesSetup. Free resource for helping beginners to build, manage and grow their websites.
- ^ Josh Fruhlinger. Ransomware explained: How it works and how to remove it. CSO Online. Tech magazine.
- ^ Alexander S. Gillis. Browser hijacker (browser hijacking). TechTarget. Data-driven marketing services.












