Snowlaysecond.top ads (scam) - Free Guide
Snowlaysecond.top ads Removal Guide
What is Snowlaysecond.top ads?
Snowlaysecond.top is a malicious website that promotes scams
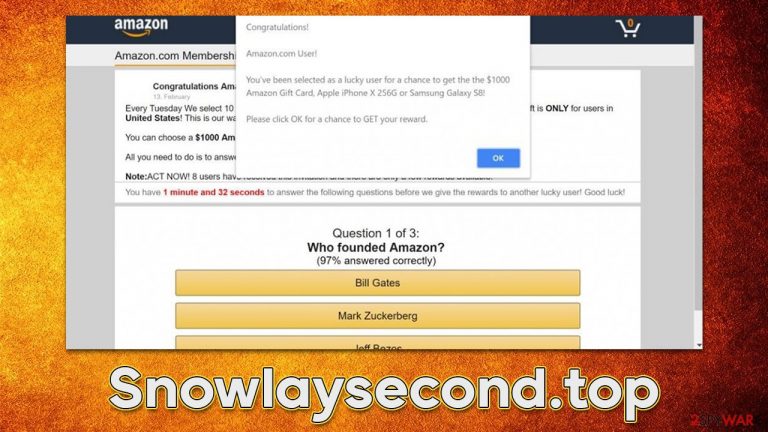
Snowlaysecond.top is a random website you may find yourself on due to different reasons, including unexpected browser redirects or link clicks on suspicious domains. As soon as you enter the page, you are likely to be presented with a misleading statement about you winning a gift or that you are eligible to participate in a survey that would result in an amazing prize, such as the newest iPhone or PlayStation console.
The main goal of scams hosted on Snowlaysecond.top is to convince people that they were lucky and some renowned company is willing to gift them an expensive item, seemingly for free. Those who believe it are then tricked into providing their home address, phone number, email, or even credit card information. This data can later be used in further phishing campaigns[1] or sold on the dark web[2] to cybercriminals.
If you have interacted with the scam, you should check out the details we provide below. We explain how to deal with the situation and mitigate any damage that could occur as an outcome of this endeavor. Likewise, we explain how to remove adware[3] or other malware, which could be the main reason for Snowlaysecond.top redirects.
| Name | Snowlaysecond.top |
| Type | Scam, phishing, adware |
| Operation | Claims that the user has been selected for a free gift; those who proceed to reclaim it are asked to provide private information such as credit card details |
| Distribution | Adware, malicious links, redirects from other websites |
| Dangers | Malicious software can cause redirects to malicious websites – financial losses, malware infections, and data disclosure can be more likely |
| Removal | To remove unwanted apps manually, you can follow our removal guide below. If the unwanted ads and other disruptive behavior do not stop, you should scan your computer with SpyHunter 5Combo Cleaner security software and delete all threats automatically |
| Other tips | FortectIntego can help you when dealing with leftover adware files. For example, you can get rid of various browser trackers and fix system damage automatically |
Scammers want personal information or unintentional subscriptions for services
The element of surprise is very powerful when it comes to various online fraud schemes. A gift card and similar giveaway scams often focus on convincing users to proceed thanks to familiar brands or company names, such as Google or Amazon.
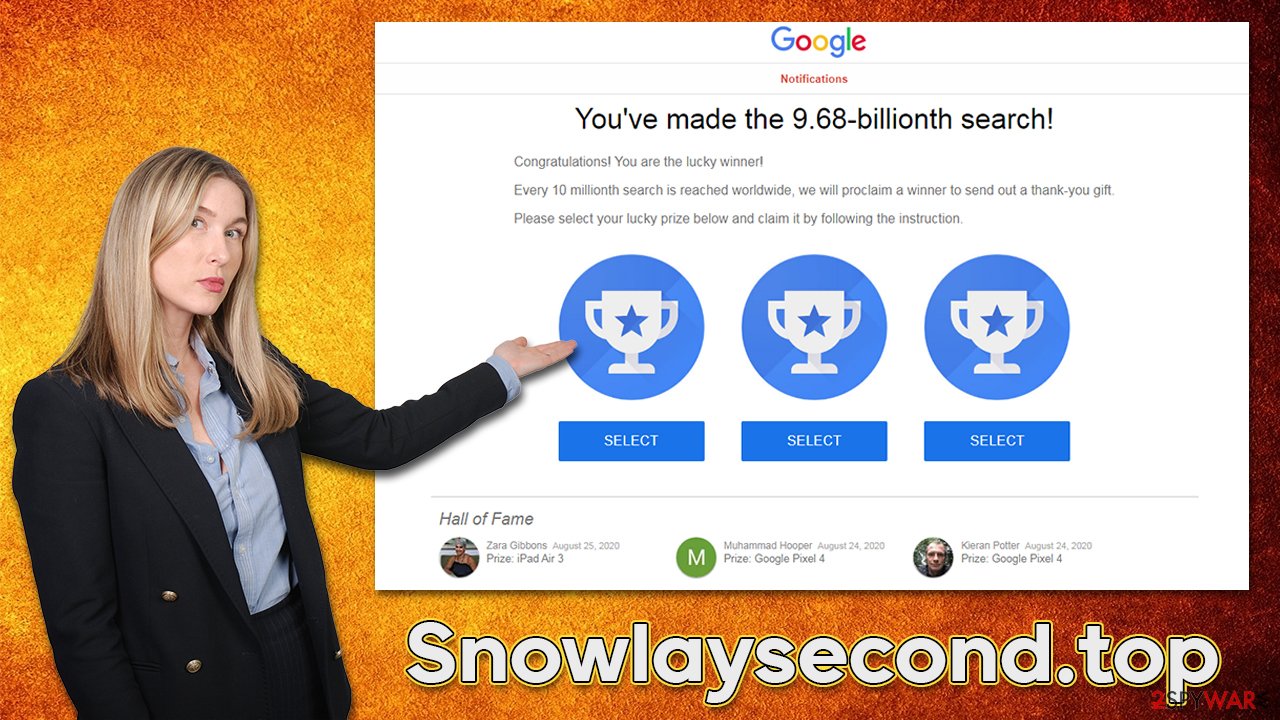
One of the most common scams you might be shown once on this page is “You've made the 16.39-billionth search” or “You've made the 9.68-billionth search!“. In these misleading messages, users are trying to be convinced that Google has selected them to receive an expensive gift due to mere luck of being X-th visitor of this alleged giveaway. Here's a message you could expect after accessing the Snowlaysecond.top scam site:
You've made the 9.68-billionth search!
Congratulations! You are the lucky winner!
Every 10 millionth search is reached worldwide, we will proclaim a winner to send out a thank-you gift.
Please select your lucky prize below and claim it by following the instruction.
Do not get fooled by such empty promises, as the message is fully fabricated, and it has nothing to do with Google or any other legitimate company. These are cybercriminals that create phishing messages and populate them on the internet for users to fall victims to. If you provide your personal details, you will never receive the promised gift because it simply doesn't exist.
Remove adware from your system
Since adware could be one of the main reasons for malicious ads and redirects, we recommend checking the system thoroughly. Uninstalling programs from the system level, getting rid of suspicious extensions, and scanning the system with SpyHunter 5Combo Cleaner, Malwarebytes, or another anti-malware are all advised steps for a safer and better computing experience.
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till the uninstallation process is complete and click OK.

Mac
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To thoroughly remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

It is important to note that adware may also be installed as a browser extension. While this type of software is much less impactful as it can't have high permissions on the system, there are plenty of malicious extensions that could be tied to a program installed on the system. Thus, it is vital to remove all the potentially malicious browser add-ons as well.
To do that, open your web browser and go to Settings, then find the Extensions section (the easier way is to click the “Extensions” button next to the settings menu of the browser). From there, remove everything you find suspicious and if you are not sure, simply remove all add-ons.
How to ensure your security and privacy
Once you are sure that adware and all the other unwanted or malicious programs/extensions are removed, your job is not done yet. Be aware that, when dealing with online scams, there are plenty of things you can do to secure your privacy. This step might not be necessary, depending on whether or not you interacted with any of the Snowlaysecond.top ads and download links.
For example, you might have been asked to provide personal information, such as email, phone number, or even credit card details. If you did, beware that your contact details will likely be used for further scam attempts against you, so be wary of suspicious calls or emails. Likewise, you should always monitor your online banking and change your passwords on all your accounts if you have disclosed it on a malicious website.
Another important step to recovery is to ensure that adware or other unknown parties no longer gather information about you passively. Every time you visit a website or download adware-type software, trackers such as cookies may be used to follow your online activities. To prevent this from happening, we recommend you clean your browser caches at once. You can either employ FortectIntego to do it more efficiently or perform the manual steps shown below:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

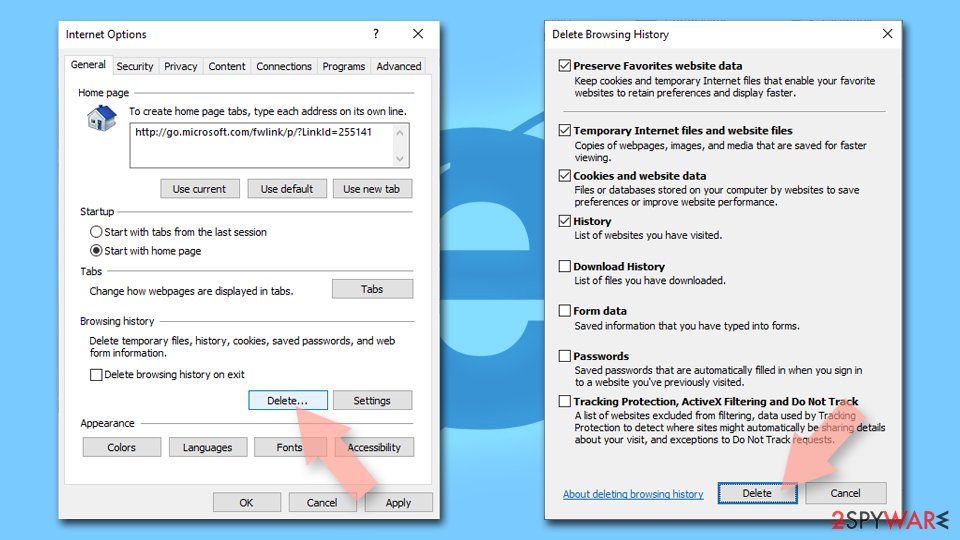
Internet Explorer
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
