TeslaCrypt 4.0 (Removal Guide) - 2021 update
TeslaCrypt 4.0 Removal Guide
What is TeslaCrypt 4.0?
TeslaCrypt 4.0 virus is yet another version of well-known file locking ransomware
TeslaCrypt 4.0 virus is another version of TeslaCrypt ransomware. Like most threats of this kind, this ransomware encrypts confidential information and delivers a note requiring to pay the ransom in exchange for the encrypted data. It has been reported that the malware came with some updated features and fixes. Therefore, we are here to inform you about them and the options that you have after being infected with this threat.
As we have already mentioned, TeslaCrypt 4.0 ransomware is a renewed version of TeslaCrypt, which was noticed more than a few years ago. However, it seems that the creators of this virus decided to make things worse by fixing a bug that was noticed in previous versions.
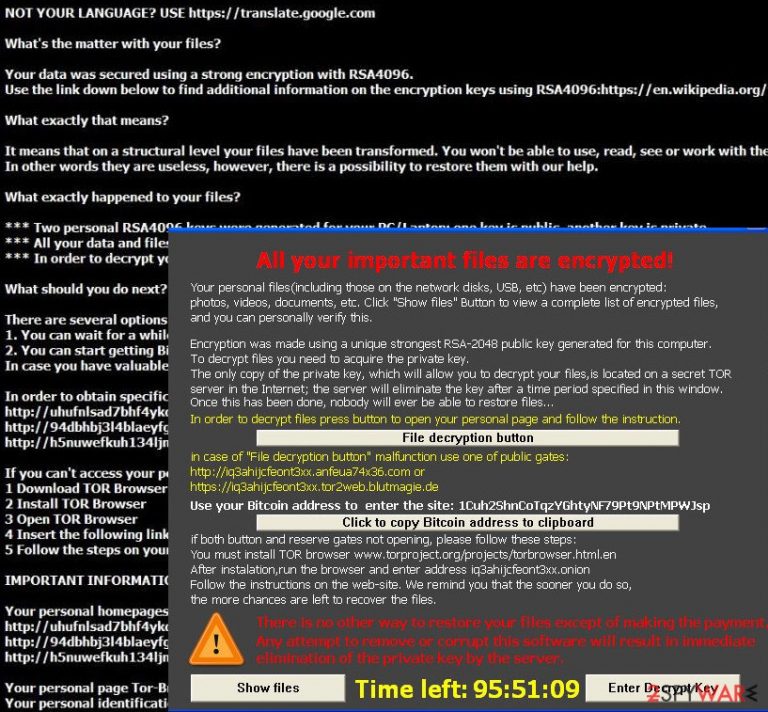
TeslaCrypt 4.0 no longer attaches an extension to the encrypted files, so you can not even know that your files are locked. Moreover, earlier the virus had a bug that corrupted files bigger than 4 GB, however, now this bug is fixed and the virus is able to encrypt all files without corrupting them. When it finishes the encryption process, it leaves these files on your system:
- Desktop: RECOVER[5_chars].html
- Desktop: RECOVER[5_chars].png
- Desktop: RECOVER[5_chars].txt
- Documents: recover_file.txt
- Documents: [random].exe
Additionally, it seems that the latest version of TeslaCrypt uses a different encryption algorithm – RSA 4096, contrary to widely used RSA 2048 code.
If this virus has already affected your files and you are looking for the decryption software, do not rush to search for your credit card. It is possible to decrypt TeslaCrypt without paying the ransom. Look for decryption software at the bottom of this article.
Also, we will try to explain to you how can you remove TeslaCrypt 4.0 virus from your computer. Please note that one of the most effective ways to terminate this threat is to run a full system scan using SpyHunter 5Combo Cleaner or Malwarebytes.
If you have already managed to delete TeslaCrypt 4.0 virus from your system, you may also need a reliable repair tool to fix system files and other problems. We recommend relying on FortectIntego.
Ransomware spreads in different ways
Though it is known that there are new features added to this ransomware, the main principle remains the same. You can get infected with this ransomware via spam containing a malicious attachment. Once you open it, the virus starts encrypting your files. Further on, it generates two keys for the encrypted data – a private and public key. The public key enables anyone to decrypt the files in other systems, but, in order to access it again, a unique private key is created. Thus, you need to acquire two different keys to retrieve your valuable information.
What is more, cybercriminals try to make a victim lose his or her temper by providing seemingly simple solutions. Certainly, all of them are seeking the same goal – trick users into thinking that paying the ransom is the only choice to retrieve the data. Nonetheless, do not behave according to their expectations and think about virus removal instead.
If you have too much money, you might try to make a transaction and hope that cybercriminals will have mercy on you. However, it is unlikely. Furthermore, beware that the virus targets computers via exploit kits, alternatively known as trojans. These files have the ability to pass themselves off as ordinary system files. Thus, when they infiltrate a system, they set free ominous ransomware.
As you can see, the consequences are significantly damaging. If you are one of the unlucky ones who have been affected by ransomware, check below to know more about its removal.
Remove TeslaCrypt 4.0 virus as soon as possible
If you are infected, we would like to introduce you elimination options that you have. First of all, we have to warn you that you should skip the idea of manual removal at once unless you specialize in IT programming. We highly discourage you from this option because manual TeslaCrypt 4.0 virus removal can lead you to additional problems. According to PC security experts, only automatic elimination should be considered the right choice in this situation, so make sure you install SpyHunter 5Combo Cleaner or Malwarebytes.
Note that when dealing with this version of ransomware you may notice that these anti-spyware programs are blocked by your virus. Thus, the only efficient solution to remove TeslaCrypt 4.0 virus might be to follow a guide given below and disable the ransomware first.
After removing the virus, be sure to fix system files with FortectIntego. Also, you CAN decrypt files locked by TeslaCrypt 4 with a help of this TeslaCrypt decryption tool. It seems that crooks have shut down the TeslaCrypt project; they have also released the master decryption key, so now it is possible to recover your data for free.
Getting rid of TeslaCrypt 4.0. Follow these steps
Manual removal using Safe Mode
If you want to get rid of ransomware, enter Safe Mode with Networking
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove TeslaCrypt 4.0 using System Restore
Some viruses could be removed with System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of TeslaCrypt 4.0. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove TeslaCrypt 4.0 from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by TeslaCrypt 4.0, you can use several methods to restore them:
Data Recovery Pro might be able to restore TeslaCrypt 4.0 files
Data Recovery can be useful if you want to restore files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by TeslaCrypt 4.0 ransomware;
- Restore them.
Data recovery using Windows Previous Version feature
This feature might allow recovering locked files too.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Trai to use Shadow Explorer for data recovery
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption method
If you want to recover your files, use the TeslaCrypt decryption tool.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from TeslaCrypt 4.0 and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.







