Trojan.Win32.Generic (Virus Removal Guide) - Virus Removal Instructions
Trojan.Win32.Generic Removal Guide
What is Trojan.Win32.Generic?
Trojan.Win32.Generic – a generic AV alert flagging an unknown software caught due to malicious activities
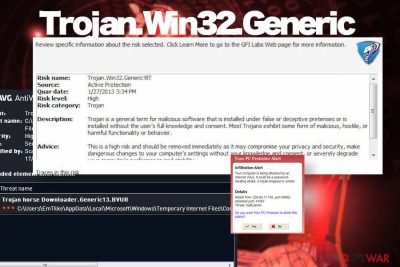
Trojan.Win32.Generic is a heuristic detection[1] by multiple antivirus programs, which may refer to a Trojan or another previously unknown virus infection. Multiple cybersecurity websites associate this detection with a Trojan, though, in fact, it can be related to any other malware type, including ransomware, spyware, keylogger, adware, and etc. In most of the cases, this alert may be accompanied by long system boot time, high CPU usage, and software freezes. This applies if Trojan.Win32.Generic determines respectability towards a particular system's threat. Nevertheless, in some of the cases, this detection may be false-positive or a false alarm indicating a non-existent threat.
Also known as HEUR.Trojan.Win32.Generic, the Trojan.Win32.Generic virus may indicate a newly released virus that exhibits never-seen-before activities that an AV engine recognizes as malicious. However, it may also denote a new variant of a virus that is already spreading in the wild. This particular detection can be possibly related to Zeus and Andromeda Trojans.
| Name | Trojan.Win32.Generic |
| Also known |
|
| Classification | Generic AV detection, possibly Trojan or other malware infection |
| Symptoms | Trojan.Win32.Generic alert, if it denotes a malware infection, can be accompanied by high CPU usage, Windows freezes, prolonged bootup time, web browser's corruption, error messages, and regular AV popups warning about suspicious activities on the system |
| Danger level | High. Suchlike generic AV detections are usually triggered by Trojans[2] or Spyware, meaning that the system may be infected with a malicious virus that may try to steal your credentials, personally identifiable information or lock/leak data stored on the hard disk |
| Distribution | The Trojan.Win32.Generic related virus can be distributed via pirated software, malicious websites, freeware additions, software cracks, spam email attachments, and other methods exploited by cybercriminals |
| Removal | Trojan.Win32.Generic removal is possible with a professional AV tool only. This detection signals a malicious infection, which may root into Windows registries and hack the core system's files. Nevertheless, the AV program may only be able to quarantine the infection, but the removal may require launching updates of databases and modules |
| Repair virus damage | The repair of any damage caused to the inner Windows system files and registries will not be obtained by Trojan.Win32.Generic removal. A powerful recovery tool, such as FortectIntego is required |
There are many ways of Trojan.Win32.Generic malware infiltrating the system. Typically, PC owners are tricked into downloading malicious entries on email messages, which often look harmless and reliable. In addition, the Trojan may be injected using the drive-by-download method, when a Trojan-carrying program automatically gets downloaded onto the system without user's granted permission for the download.
Apart from the mentioned methods, malware can be installed along with pirated software, game cracks or fake updates. In these cases, the user is more or less aware of the risks that he or she takes relying on illegal/compromised software.
The criminals behind the Trojan.Win32.Generic virus may try to initiate a multitude of malicious activities, such as:
- diminish the system's protection to open a backdoor for other cyber infections;
- connect to remote servers and download malware without user's awareness;
- initiate tracking activities with an intention to collect confidential information, including credit card details, passwords, login data, etc.
- compromise web browser's settings in a way to trigger redirects to phishing websites;
- generate aggressive pop-ups, hyperlinks, banners, and another context that may expose a potential victim to dangerous viruses or offensive material;
As pointed out by dieviren.de[3] cybersecurity team, Trojan.Win32.Generic virus detection by any reputable anti-virus program may be triggered by a newly released ransomware variant of such infamous families as Djvu, STOP, CryptoMix, Dharma, and many others. Therefore, the emergence of regular popups by your AV engine that flag a malicious activity by Trojan Win32 Generic should be treated seriously.
To prevent data encryption, loss of important documents, financial information, the system's crash, and similar activities, an immediate Trojan.Win32.Generic removal is required. Even though the antivirus engine is powerful enough to detect and quarantine the malicious entry, it may not be able to finish up the removal process. That's because the antivirus database may not contain the signature of the detected infection. In this case, you may need to install the latest AV definition updates.
Moreover, security software may fail to remove Trojan.Win32.Generic virus because its scanner is terminated once launched. to bypass the block, try to restart the system into Safe Mode.
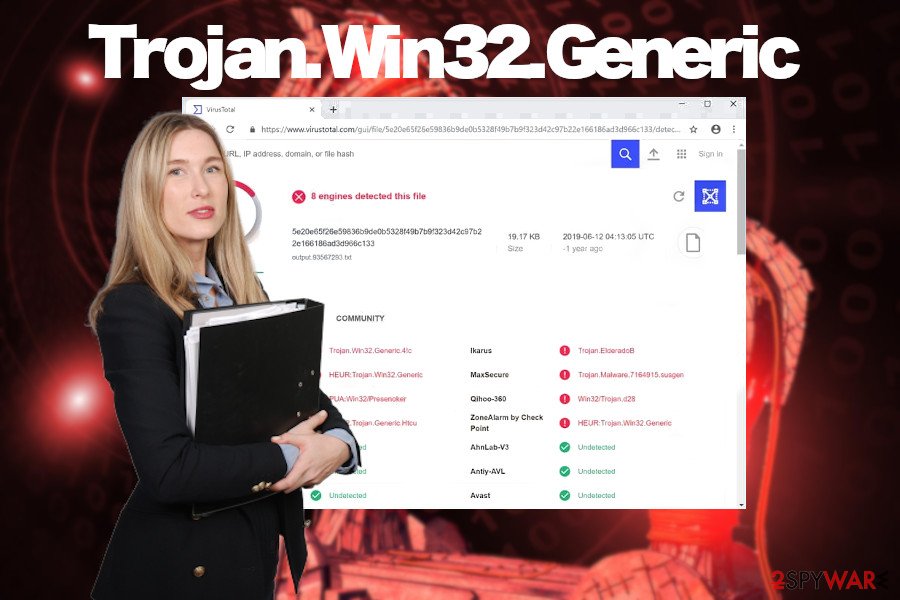
If, however, the system does not exhibit abnormal behavior, but the AV that you are currently using keeps reporting Trojan.Win32.Generic malware, try an alternative anti-virus engine and compare their findings. Since such heuristic detections can sometimes be false-positive, you may be looking for a non-existent virus.
Malicious files and programs are distributed via deceptive sites, software, and spam emails
Although there are more techniques for virus/malware distribution, the most common places where people get tricked into installing malicious pieces of malware are infected websites, pirated software or freeware download websites, and leaked email accounts.
Despite the fact that potential victims are not aware of a possible virus attack, the installation of Trojan, spyware or other malware is seldom possible with the user's intervention. In most of the cases, people are redirected to phishing websites or websites with hacked URLs after clicking on a questionable popup, hyperlink or visiting adult content websites intentionally.
The same applies to the software that carries malware. Apart from some exclusions, legitimate software distributed on official websites or other reliable sources is checked and signed as safe to download. However, if the user relies on freeware download websites that are publicly described as a source for malware, as well as searches shady forums for cracks and keygens, the user takes the responsibility for a possible virus infection.
The best piece of advice is to raise consciousness about dangers online. Do not rely on freeware just because they are offered for free. Keep in mind that these sites get monetized in other ways, for example, receive commissions for distributing malware.
However, the biggest malware download source remains malicious spam emails. Criminals take advantage of botnets to send thousands of infected emails to leaked email addresses. Typically, these emails are poorly written, contain many mistakes and are received from suspicious senders. Therefore, email filters typically send such emails to a spam folder by default. However, there are many “successful” spam campaigns that mimic well-known organizations like Red Cross or FedEx. Such messages may contain reliable information, well-developed style, convincing details, trustful sender, and so on. It's advisable to double-check the sender or set the AV engine to scan the attachment of the email to make sure that it's not infected. Otherwise, it's best to delete such a message from the inbox.
Eliminate Trojan.Win32.Generic virus from the system immediately to prevent possible damage
Having Trojan.Win32.Generic malware on the system poses a high risk of cyber attacks. Criminals may be using this infection for the distribution of ransomware, spyware, keyloggers and similar viruses that may cause money loss or identity theft.
Even though the machine that is said to encounter this generic infection is not exhibiting suspicious activities and does not seem to be infected, beware that Trojans and likewise malware are exceptionally persistent. Malicious files may be dispersed in various system areas and block AV engines to remain unnoticed.
To ensure successful Trojan.Win32.Generic removal, go to the Safe Mode with Networking, a thorough guide on how to do that is given down below, and try to download the latest virus definition updates for the security software that you are using. After that, while still in Safe Mode, run a deep system scan.
To remove Trojan.Win32.Generic completely, we recommend relying on programs like SpyHunter 5Combo Cleaner or Malwarebytes. The mentioned programs are capable of detecting malware and eliminated all related malicious entries. In addition to elimination of the malware, you should also take care of the system's stability, which may be breached. FortectIntego can help in fixing corrupted registry entries, deleting duplicates, and eliminated other side effects caused by virus infection.
Getting rid of Trojan.Win32.Generic. Follow these steps
Manual removal using Safe Mode
Since your anti-virus may be blocked malicious processes, boot the system into Safe Mode to remove Trojan.Win32.Generic once and for all
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Trojan.Win32.Generic using System Restore
Elimination of viruses can be initiated with the help of the Windows Previous Version feature. To enable it, please follow this guide
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Trojan.Win32.Generic. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Trojan.Win32.Generic and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ What is Heuristic Analysis?. Kaspersky. Cyber security solutions.
- ^ Trojan. Panda Security. IT security solutions.
- ^ SICHERHEIT- UND SPYWARE-NEUIGKEITEN. Dieviren. Virus and spyware news.





















