Trojan:win32/fuery.b!cl (Virus Removal Guide) - Free Instructions
Trojan:win32/fuery.b!cl Removal Guide
What is Trojan:win32/fuery.b!cl?
Trojan:win32/fuery.b!cl – malicious program that is spread through third-party downloads
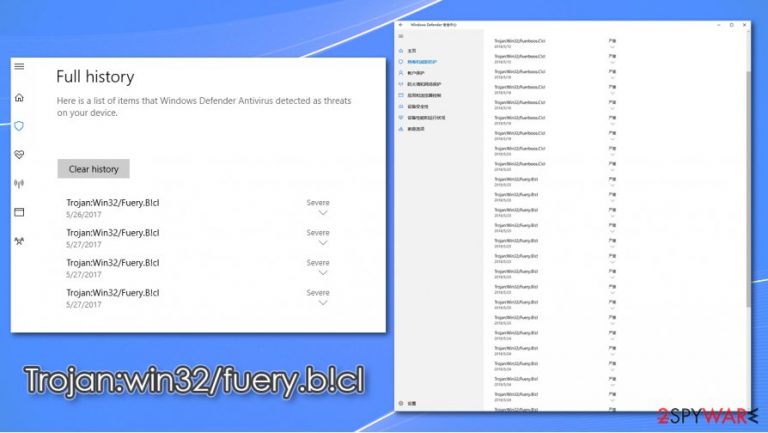
Trojan:win32/fuery.b!cl is a heuristic detection name a particular computer threat, typically assigned by Windows Defender. Trojans can represent a wide variety of different functions, depending on what the hackers programmed it to do. Essentially, these types of infections are defined by their distribution method rather than functionality. Thus, there could be different tasks that the malicious program that you are dealing with was designed to do, for example, steal personal or sensitive information, redirect traffic, inject other malware, etc.
In some cases, however, Trojan:win32/fuery.b!cl virus detection might indicate a false positive,[1] as it sometimes happens with generic detection threats. If your security software flagged a download as malicious, you should always investigate and never ignore these warnings.
| Name | Trojan:win32/fuery.b!cl |
| Type | Trojan |
| Distribution | These malicious programs are typically downloaded when users believe that the file is safe and legitimate. Users can download a Trojan through fake updates, software cracks, software bundles, malicious spam email attachments, deceptive ads, and similar |
| Symptoms | Symptoms might vary, depending on what the malicious program was designed to do. For example, a crypto-mining malware would run CPU/GPU at its full capacity, traffic hijacking apps would change homepage and other browser settings. In some cases, symptoms would be completely lacking |
| Dangers | Installation of other malware, personal data theft, account compromise, personal file loss, identity theft |
| Elimination | If you are unsure whether the detection is legitimate and not a false positive, you can scan your machine with alternative anti-malware software, such as SpyHunter 5Combo Cleaner or Malwarebytes |
| System fix | In case malware managed to break into your PC, you might start suffering from various stability issues (crashes, errors, lag) after the elimination. We recommend using repair software FortectIntego to fix post-infection problems |
Since Trojan:win32/fuery.b!cl is a generic Trojan, it appears on users' systems when they attempt to download something that they believe to be legitimate. There are several different ways how this can occur, as malicious actors come up with various ways to make users download and execute malicious files on their computers. Here are a few examples:
- Fake Flash update prompts;
- Malicious spam email attachments;
- Software bundles;
- Pirated software installers, software cracks;
- Malicious advertisements.
Initially, Windows Defender will show a popup and remove Trojan:win32/fuery.b!cl from the active files by placing it into quarantine. However, many users reported that the detection might come back, so they were worried whether the threat was actually deleted fully.
In case malware manages to bypass defenses, it can cause significant issues to users and their computers. Quite often, Trojans perform registry changes in order to run with every system boot, inject hundreds of malicious files, terminate and spawn new processes, etc. These modifications can impact Windows in various negative ways and later cause significant performance issues. If that is the case for you, we recommend using FortectIntego to attempt to fix virus damage an remediate the system automatically.
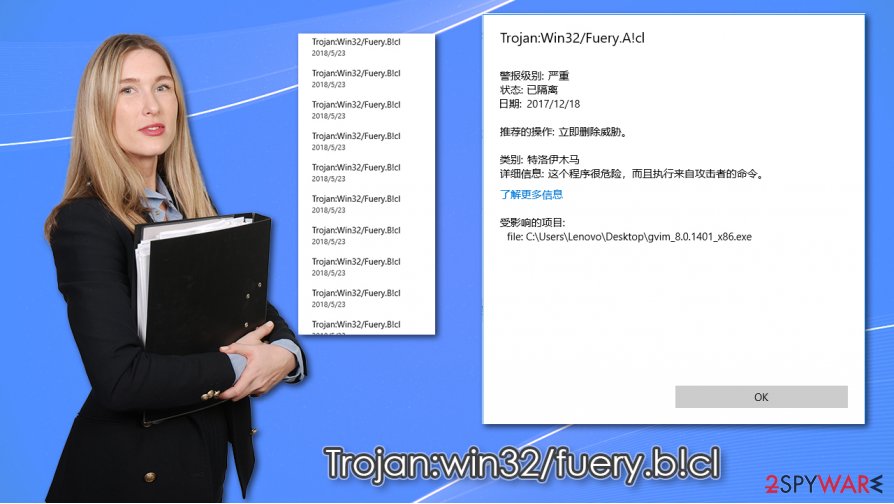
If Trojan:win32/fuery.b!cl removal is not performed on time, it can allow the attackers to achieve whatever goals they set. In most cases, the malicious program might alter the web browser settings and redirect traffic to malicious websites or perform clicks on behalf of the user. This proves to be a lucrative business model, as bots can make thousands of clicks every minute.
However, if the Trojan:win32/fuery.b!cl virus is programmed to steal information in the background, you are less likely to see any infection symptoms at all, which makes the whole situation a lot more complicated. Since malware remains stealthy and is not detected by security software (or the lack of it), it can remain operational for weeks or years, stealing banking details, logins, financial, and other types of sensitive data. This way, the infection can result in serious consequences, including identity theft, monetary losses, and much more.
Therefore, we highly advise you to employ a powerful third-party security solution that could work along with Windows Defender or replace it entirely. For that, we recommend using SpyHunter 5Combo Cleaner or Malwarebytes. Scanning the device with a different anti-malware would also help you to determine whether the Trojan:win32/fuery.b!cl detection is a false positive or not.
You can protect your computer from most of the infections
As already mentioned, Trojans are not defined by their functionality as they can possess an array of different capabilities. The classification comes from their distribution techniques – these types of threats are injected into systems after users attempt to install something they believe to be secure. In most cases, distribution techniques rely on social engineering and phishing tactics, so users get convinced easier.
One of the most common Trojan distribution methods is fake Flash Player update prompts (or other popular software such as Google Chrome or Mozilla Firefox). Since the plugin was widely used by various websites to play multimedia, it got embedded in users' minds, and they still believe that it is required – hackers are well aware of that. Thus, it is very easy to trick the general population to download the alleged updates. In most cases, users will not even know that they let a Trojan into their systems and believe they installed an actual Flash update.
Another reason why users get infected with Trojans – spam emails. These are typically comprised of a fake message that urges recipients to open the attachment. As soon as the file is opened and the macro function allowed, a set of commands are executed, and malicious payload downloaded in the background. Thus, never open suspicious attachments, even if they seem legitimate and the email address of the sender seems to match the original one – it can be easily spoofed.
Finally, some users ignore anti-virus software warnings during the attempts to download pirated programs or software cracks. These installers should never be used, as it is the easiest way to infect your machine with malware.
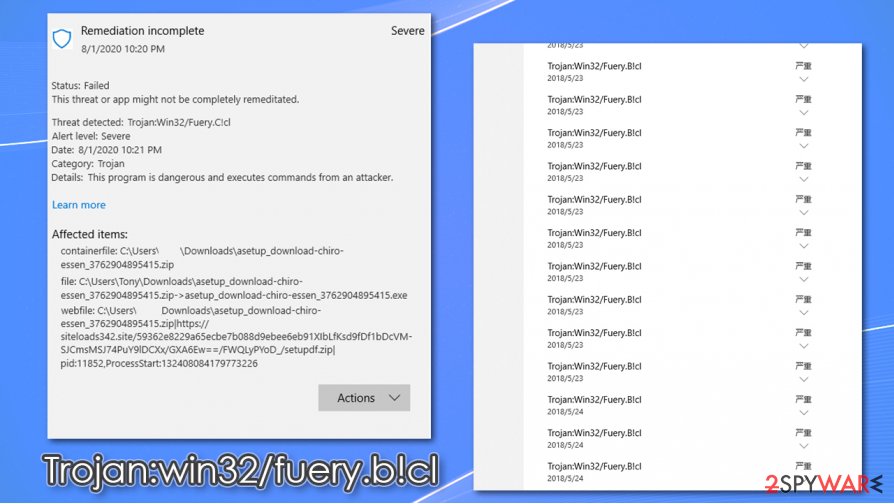
Delete Trojan:win32/fuery.b!cl and perform additional checks to ensure computer safety
Some people said they were not convinced that the threat was completely dealt with after Trojan:win32/fuery.b!cl removal. In some cases, users even found a suspicious app installed on their machines after the termination was seemingly completed. Therefore, it is always worth checking the system with an alternative security tool to ensure that no more threats are present – experts[2] recommend using SpyHunter 5Combo Cleaner or Malwarebytes. In case malware is preventing your security software from working correctly, access Safe Mode with Networking and perform a scan from there.
However, if you were downloading a legitimate application and Windows Defender flagged it as malicious, you should perform several checks before you remove Trojan:win32/fuery.b!cl. Scanning it with an alternative security tool could help with this as well; or, you could upload the file to sandbox analysis[3] platforms such as Virus Total.
Getting rid of Trojan:win32/fuery.b!cl. Follow these steps
Manual removal using Safe Mode
Access Safe Mode with Networking if malware is tampering with your security app:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Trojan:win32/fuery.b!cl and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting trojans
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Chris Hoffman. How To Tell If a Virus Is Actually a False Positive. How-To Geek. Site that explains technology.
- ^ Lesvirus. Lesvirus. Cybersecurity news and malware insights.
- ^ Sandbox (computer security). Wikipedia. The free encyclopedia.
