Unicorn ransomware (2020 update) - Free Instructions
Unicorn virus Removal Guide
What is Unicorn ransomware?
Unicorn ransomware – file locking malware attacking Italian users via a fake coronavirus website

Unicorn ransomware is a data locker that was spotted by researchers at the end of May 2020.[1] This type of malware is considered one of the most damaging computer infections, as it can potentially result in permanent loss of personal data like pictures, music, videos, documents, databases, etc. Hackers lock all personal files using an encryption algorithm and then demand a ransom of 300 euros to be paid in exchange for Unicorn ransomware decryptor. It appends .fuckunicorn[random] to each of the affected files, drops a Read_IT.txt ransom note (written in Italian) file, and asks users to contact the attackers via the xxcte2664@protonmail.com email address.
Unicorn ransomware spreads via fake phishing websites such as www.fofl[.]it – it mimics an official coronavirus-related Italian website www.fofi.it. Users are tricked into downloading IMMUNI.exe executable file, which begins the infection and later runs a “fuckunicorn” process in the background. While the situation might seem threatening, security researchers MalwareHunterTeam claimed that the Unicorn file virus is based on open-source code and was most likely produced by a low-skilled, wannabe hacker.
| Name | Unicorn ransomware |
| Type | File locking virus, crypto-malware |
| Targets | Italian users |
| Distribution | Malware developers created a fake website mimicking a legitimate Italian, coronavirus-themed site. Users are then tricked into downloading and installing malicious installer via the site, infecting their machines with ransowmare |
| Related | IMMUNI.exe, “fuckunicorn” ransomware process |
| Ransom note | Read_IT.txt dropped into each of the affected file folders. Also, the desktop wallpaper is changed, which includes a share of a unicorn and a brief version of the message from malware authors |
| File extension | Each of the susceptible files are appended with .fuckunicorn[random] extension |
| Contact | Crooks provide xxcte2664@protonmail.com for communication purposes |
| Ransom size | 300 euro in bitcoin |
| Data return | Safest data return can be performed via backups. If no backups exist, MalwareHunterTeam [can be contacted on Twitter] claimed that they could provide a possible decryptor. Alternatively, use alternative data recovery methods provided below |
| Malware removal | Download and install powerful anti-malware software and perform a full system scan (access Safe Mode if required) |
| System fix | Unicorn ransomware is opensource-based malware that could include many bugs that could destroy Windows OS. To fix this damage, scan your system with FortectIntego after malware elimination |
Once inside the system, Unicorn ransomware does not encrypt data immediately, as it needs to prepare the system for the process. The malware only attacks Windows-based systems with the help of the PE EXE file (portable executable).[2]
As soon as IMMUNI.exe file (can be named as something else in other instances) is launched, malware would place it into one of the following folders:
- %AppData%
- %Temp%
- %User%
From there, it begins the infection routine and performs changes to Windows. For example, Unicorn virus would eliminate Shadow Volume Copies in order to prevent users from fast data recovery, would modify the Windows registry to be booted each time the computer is started, launch a “fuckunicorn” ransomware process in the background, and change the system in other ways.
Since malware is not stable, it might cause serious Windows malfunctions, even after ransomware removal is performed using security software. If you notice substantial performance drop after you eliminate the threat, also perform a scan with a repair tool FortectIntego.
An interesting fact is that Unicorn ransomware also drops a working COVID-19 map provided by the Center for Systems Science and Engineering at Johns Hopkins University. This map was previously abused by multiple campaigns and delivered such threats as AZORult banking Trojan on users' systems without them knowing anything about it.
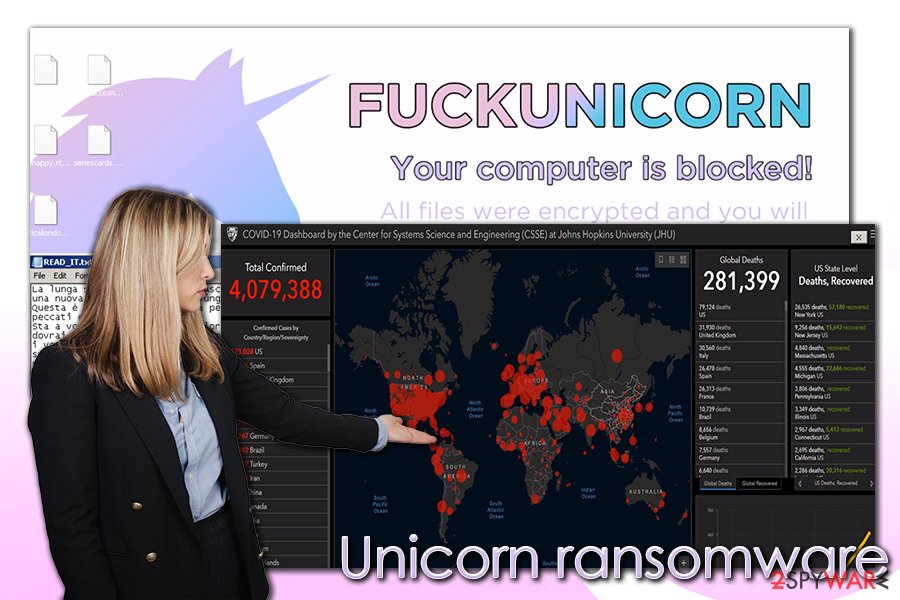
As soon as the system is prepared, Unicorn ransomware immediately encrypts all personal files on the system targeting the most commonly-used extension such as .pdf, .doc, .jpg, .mp4, .rar, and many others. As a result, victims are unable to open any of the files on their computer, since it requires a special key that is held hostage by malicious actors. Each of suchlike files will be appended with a partially random extension, for example, “picture.jpg.fuckunicornhtrhrtjrjy.”
After that, users will be presented with a changed background, which has the following text:
FUCKUNICORN
Your computer is blocked!
All files were encrypted and you will not get access to them just like that, but only break them! If you meed our conditions, you can easily decrypt your files! Think about it!
While desktop wallpaper text is written in English, the actual ransom note Read_IT.txt is in Italian, confirming that the attackers aim to infect users from this country. The message from the Unicorn ransomware authors is full of Greek mythology references, mentioning ancient gods like Asclepius:
La lunga serpe sul bastone di Asceplio si è ribellata, ed una nuova era sta per sopraggiungere!
Questa è la vostra possibilità per redimervi dopo anni di peccati e soprusi.
Sta a voi scegliere. Entro 3 giorni il pegno pagare dovrai o il fuoco di Prometeo cancellerà
i vostri dati così come ha cancellato il potere degli Dei sugli uomini. Il pegno è di solamente 300 euros, da pagare
con i Bitcoin al seguente indirizzo : 195naAM74WpLtGHsKp9azSsXWmBCaDscxJ dopo che pagato avrai,
una email mandarci dovrai. xxcte2664@protonmail.com il codice di transazione sarà la prova.
Dopo il pegno pagato riceverai la soluzione per spegnere il fuoco di Prometeo. Andare dalla
polizia o chiamare tecnici a niente servirà, nessun essere umano aiutarti potrà.
Even though Unicorn ransomware developers might be inspired by mythology and of a creative nature, it does not matter much for the infected users. Victims are asked to transfer 300 euro payment into the provided Bitcoin wallet, and that allegedly nothing else can help them.
However, security researchers highly discourage making any deals with ransomware developers, especially sine malware, is based on open-source code. The delivered Unicorn ransomware decryptor might simply fail to work, or the attackers might ignore you completely.
Therefore, rather use alternative methods for data recovery we provide below and remove ransomware instead. Keep in mind that some malware of such type is designed to exit the system after the encryption is performed. However, due to the change of secondary payloads, it is important to perform a full system scan with reputable anti-malware tools like SpyHunter 5Combo Cleaner or Malwarebytes.
Ways to prevent COVID-19 phishing attacks
COVID-19 pandemic struck many industries financially, as well as humanity as a whole. People were forced to work from home; others lost their jobs due to a difficult worldwide situation that companies are facing. While many try to help by sowing masks for free and volunteering, cybercriminals are not there to help and are trying to abuse the coronavirus crisis to their own advantage. Maze ransomware authors claimed that they would spare medical institutions from the attacks, even though they continue to infect overloaded hospitals and institutions that try to help fight the virus.[3]
As a result, coronavirus phishing attacks increased in volume exponentially, as threat actors see the pandemic as a good opportunity to earn some more of the illegal income.[4] Ransomware plays a big role in this, as even more regular users and organizations keep getting tricked by COVID-19-themed emails, fake websites, and other means of phishing.

Therefore, it is vital to be vigilant during the pandemic and ensure computer security as much as possible. Here are some tips that could be helpful:
- Employ comprehensive security software with real-time/web protection feature;
- Do not download software cracks or pirated software installers;
- When trying to download a coronavirus map, ensure that it is coming from a legitimate source;
- Check the URL address of the website you visit: the attackers often replace similarly-looking letters in order to confuse visitors, all while displaying a site identical to the original one;
- Ensure that visited sites have the padlock icon neat the address bar and are marked as “Secure”;
- Do not open suspicious email attachments that ask you to enable macro function on click on hyperlinks. If unsure, put the attachment for analysis via tools like Virus Total (you can also right-click on the link and copy its address, which can be later analyzed via Virus Total);
- Backup your files regularly.
Do not pay the attackers and remove Unicorn ransomware instead
As previously mentioned, the virus is based on open-source code and is written by low-skilled criminals. Despite this, the threat should be treated as a regular ransomware infection, and all the correct measures are undertaken. Thus, before you do anything, we recommend you back up all the encrypted data (unless you have a copy of the locked files), and only then remove Unicorn ransomware from the computer.
For that, you should employ powerful anti-malware software like SpyHunter 5Combo Cleaner or Malwarebytes and perform a full system scan. If, for some reason, you are unable to do so (malware can attempt to corrupt your antivirus software), you can access Safe Mode with Networking, as explained below. Once in Safe Mode, perform a full system scan to ensure that malware and its secondary payloads are eliminated promptly.
Once you have backups ready and you sure that ransomware removal was successful, you can begin the data recovery process. Security researchers might help with a free decryption tool since the encryption of this cryptovirus is not very strong. If that does not help, you can always resort to third-party recovery tools – we provide download links below.
Getting rid of Unicorn virus. Follow these steps
Manual removal using Safe Mode
Eliminate Unicorn ransomware in Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Unicorn using System Restore
System Restore might also be useful when trying to get rid of the infection:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Unicorn. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Unicorn from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Unicorn, you can use several methods to restore them:
Data Recovery Pro method
Recovery is much more useful if you attempt to use it shortly after the infection of ransomware occurred:
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Unicorn ransomware;
- Restore them.
Make use of the built-in Previous Version Feature in Windows
You might be able to recover files one-by-one if you had System Restore point prepared before the malware attack.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might be your answer
If Unicorn file virus failed to delete Shadow Volume copies, data recovery using ShadowExplorer should be very easy:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Contact MalwareHunterTeam for help
MalwareHunterTeam is a security research team that might be able to help you restore your files for free. Contact MalwareHunterTeam on Twitter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Unicorn and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ JAMESWT. #ransomware #italy #covid19 #fuckunicorn. Twitter. Social network.
- ^ Portable Executable. Wikipedia. The free encyclopedia.
- ^ Maze Ransomware Targets the Hospitals and Labs Fighting Coronavirus. Tripwire. News, Trends, Insights.
- ^ NetSTAR Sees Rise in Phishing Scams Related to COVID-19. PR Newswire. press release distribution, targeting, monitoring.







