Unique ransomware (virus) - Tutorial
Unique virus Removal Guide
What is Unique ransomware?
Unique ransomware is malware that attempts to extort bitcoin from users worldwide
Unique virus is a malicious computer program that stems from a large family of Phobos and first surfaced at the end of September 2020. This malware, much like others of its kind, encrypts[1] any personal files found on an infected system and then asks for a ransom in order to regain access to said files. The hackers essentially make their victims choose between giving them a large sum of money or losing all important documents, videos, pictures, etc.
One of the main symptoms of this ransomware infection is that all files would be immediately appended with a .unique extension, along with a particular user ID and the cybercriminals' email uniqueproject@xsmail.com. The email is also used for communication between the attackers and victims, although uniqueproject@fastmail.com is also provided in the ransom notes info.txt and info.hta, which are delivered right after data encryption is finished.
Ransom notes explained
Ransom notes provide both the contact information and demands of the cybercriminals. Some criminals take their time in writing these, including any relevant detail and answering questions that victims might have. Quite often, they also attempt to be either friendly or frightening – it all depends on which route the ransomware gang chooses to go.
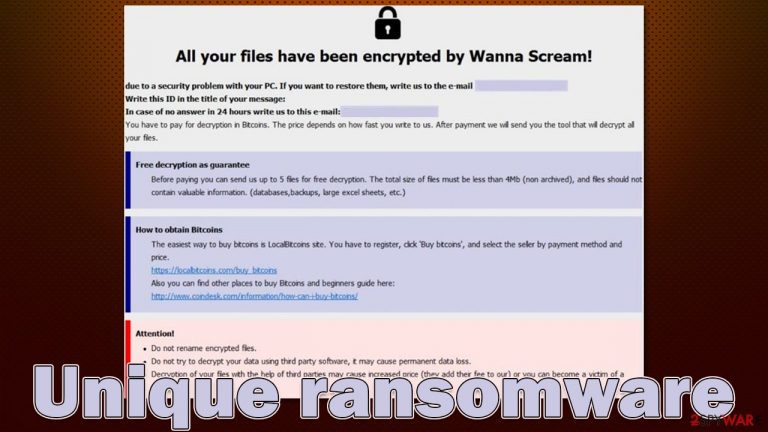
Since Unique ransomware stems from the family of Phobos, ransom notes are identical to previous versions, such as Fopra, Mmxxii, Duck, or MLF. To be more precise, this malware always drops two ransom notes, and the most visible one is the pop-up window, usually titled using the contact email of the attackers. It reads:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail uniqueproject@xsmail.com
Write this ID in the title of your message
In case of no answer in 24 hours write us to this e-mail:uniqueproject@fastmail.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 4Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Victims can also find a text file that briefly talks about what they have to do in order to restore files and provide the contact emails as well:
!!!All of your files are encrypted!!!
To decrypt them send e-mail to this address: uniqueproject@xsmail.com.
If we don't answer in 24h., send e-mail to this address: uniqueproject@fastmail.com
It is unclear why the ransomware gang delivers two notes, although it is likely to be a backup plan in case the first program window would not show up for some reason, as various applications on a PC can read text files.
Just as it is typical for various cybercriminals within the ransomware business, these ones explain in detail what users have to do to recover their files. They even promise to decrypt up to five files for free to demonstrate that decryption is possible. However, we do not recommend listening to anything that cybercriminals have to say, as they can't be trusted. Even after payment, they may fail to deliver the decryption tool. While alternatives are very limited, we still recommend them instead of paying the Unique virus authors.
| Name | Unique ransomware |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .id[random].[uniqueproject@xsmail.com].unique |
| Malware family | Phobos |
| Ransom note | info.hta and info.txt |
| Contact | uniqueproject@xsmail.com and uniqueproject@fastmail.com |
| File Recovery | The only secure way to recover data is through backups. If such isn't accessible, or if it has been encrypted, recovery alternatives are extremely limited; we'll go over all of them below |
| Malware removal | Remove the computer from the network and the internet, then run a comprehensive system scan using SpyHunter 5Combo Cleaner security software |
| System fix | If malware is installed on your system, it could potentially delete or damage vital system files, which often leads to crashes, errors, and other stability issues. You can use PC repair FortectIntego to fix any of these problems automatically |
How to deal with ransomware
Most individuals infected with ransomware have never encountered anything like it before, which makes them understandably perplexed. Following the proper procedures while combating ransomware is critical since it may affect the chances of recovering data back to normal functioning. Your first job when dealing with malware is to eliminate it, copy encrypted data, and only then attempt data restoration.
1. Disconnect your device from the network and perform a full system scan
Ransomware may establish communication to a remote server controlled by the attackers during the infection process. It is important to make sure that the computer is not connected to any networks or the internet whenever the removal process is taking place. Please follow these steps:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
While most ransomware infections self-destruct after they encrypt files, there is no assurance that no harmful modules will be left behind. Some ransomware is also bundled with other parasites, so additional malware may be present.
To ensure that Unique ransomware is removed completely, scan your system with SpyHunter 5Combo Cleaner, Malwarebytes, or another dependable security software. If the virus hampers removal efforts while in regular mode, restart your computer in Safe Mode[2] with Networking and run the scan from there:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
- Select Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
2. Attempt the .unique file recovery without paying
There are several risks associated with paying cybercriminals, as it could encourage them to target you again in the future. Additionally, even if you remove the ransomware from your system, your data will remain locked – making backups an essential way to protect yourself against this type of malware.
Unfortunately, most users fail to prepare proper backups and instead have to face the full consequences of a ransomware attack. The chances of restoring files without a decryptor are quite low, although never zero, so you should not give up immediately. Specialized data recovery software might be able to help here, although the virus should have failed to delete backup systems in Windows. Before proceeding, make sure you make backups of any encrypted files to avoid permanent data corruption.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
3. Fix damaged system files
Malware can wreak havoc on Windows systems, potentially requiring a full reinstallation to fix. For example, an infection can alter the Windows registry database, damage vital bootup and other files, delete or corrupt DLL[3] files, etc. Antivirus software often cannot repair damaged files; instead, you'll need to use a specialized app.
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Encryption. Investopedia. Sharper insight, better investing.
- ^ Safe Mode. Computer Hope. Free computer help.
- ^ What is a DLL. https://learn.microsoft.com/en-us/troubleshoot/windows-client/deployment/dynamic-link-library.
