Voicemail email scam (fake) - Free Guide
Voicemail email scam Removal Guide
What is Voicemail email scam?
Voicemail email scam seeks to lure out users' login details which can lead to stolen accounts
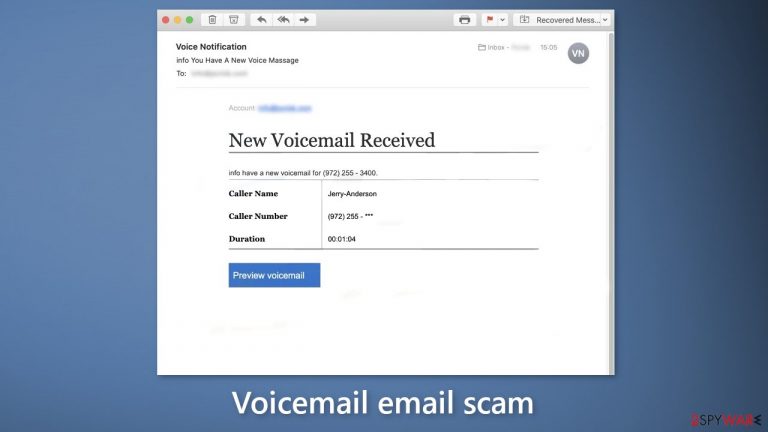
Voicemail email scam is a massive spam operation carried out by crooks. Thousands of fake emails are sent to unsuspecting users. The message in question is disguised to look like it concerns a new voicemail. However, there is no real voicemail. The full message reads as follows:
Account: [recipient's email address]
New Voicemail Receivedinfo have a new voicemail for (972) 255 – 3400.
Caller Name Jerry-Anderson
Caller Number (972) 255 – ***
Duration 00:01:04Preview voicemail
The main goal of this phishing[1] attack is to redirect users to a fake website. When users click on the “Preview voicemail” button that is exactly what happens. The bogus page is designed to record data entered into it. The page requests users to sign in using their email account log-in credentials (the email address and a password). If users enter their login information on this website, they can have their email accounts stolen.
These malicious emails and even social media messages might appear out of nowhere, and you might be tricked into revealing your details after some data leaks of other platforms. These databases that get leaked online can include usernames and passwords, so your platforms get hacked or people can blackmail you into paying by exposing your details in the email and asking for hush money and scaring you into paying with other claims.
| NAME | Voicemail email scam |
| TYPE | Phishing attempt |
| SYMPTOMS | Stolen passwords, monetary losses, identity theft |
| DISTRIBUTION | |
| DANGERS | Crooks behind the email are attempting to lure out login details |
| ELIMINATION | If you opened an email with a malicious attachment scan your computer with anti-malware tools |
| FURTHER STEPS | Use FortectIntego to clear your browsers and get rid of any remaining damage |
Email scams in general
For email scam campaigns, crooks usually use social engineering[2] methods to manipulate users. Often, they make the letters look like they are sent from well-known companies to appear legitimate and trustworthy. Different crooks have different motivations for why they create these campaigns.
Often, they seek to lure out personal information, such as login details, names, email addresses, phone numbers, credit card details, and more. However, they also create emails that are meant to infect people's devices with PUPs (potentially unwanted programs) or malware[3] such as ransomware, spyware, Trojans, etc.
For malware distribution, fraudsters include infected attachments or malicious links and craft the message in the email to urge people to open them. That is why it is best to only open attachments from senders you know. Try to always be cautious and read messages fully.
Look for any grammar or spelling mistakes as fraudsters often make them. Also, if the message feels like it's pressuring you into performing some kind of action, it is best to check if the email address is authentic and belongs to the company it supposedly came from.
Take action if you have fallen for it
If you have entered sensitive information in a phishing website, such as your login credentials, you should immediately try to change your passwords before crooks can get to your accounts. Additionally, if you entered your banking details on a shady site, you should contact your bank as soon as possible. You may make it in time and block your card before cybercriminals can use it.
Most importantly, you should follow security experts' guidelines to prevent this from happening again. It is useful to have professional security tools installed on your computer that can detect suspicious processes and eliminate them. It is also good to educate yourself about various other email scams. We previously wrote about Payroll Timetable, Windows Defender Advanced Threat Protection, Due Payment-Invoice, and many more.
Check your system for malware infections
If you suspect that you have opened an email with an infected attachment, you should take care of the threat. We recommend using SpyHunter 5Combo Cleaner or Malwarebytes security tools that will scan your machine, eliminate it, and prevent such infections in the future by giving you a warning before a malicious program can make any changes.
Crooks often disguise their malicious programs as “handy” tools so they would be more difficult to identify for the average user. People also often fail to eliminate all the related files and entries which could lead to the renewal of an infection. The program could have any name and icon, so this step is best performed by anti-malware tools.
However, if manual removal is what you prefer, we have instructions for Windows and Mac machines:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Repair the damaged operating system
Performance, stability, and usability issues, to the point where a complete Windows reinstall is required, are expected after a malware infection. These types of infections can alter the Windows registry database, damage vital bootup, and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not able to repair it.
This is why FortectIntego was developed. It can fix a lot of the damage caused by an infection like this. Blue Screen errors,[4] freezes, registry errors, damaged DLLs, etc., can make your computer completely unusable. By using this maintenance tool, you could avoid Windows reinstallation.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
- The analysis of your machine will begin immediately
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

How to prevent from getting spam tools
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Phishing. Wikipedia, the free encyclopedia.
- ^ Cynthia Gonzalez. Top 8 Social Engineering Techniques and How to Prevent Them [2022]. Exabeam. Information Security.
- ^ Malware. Malwarebytes. Cybersecurity Basics.
- ^ Tim Fisher. Blue Screen of Death (BSOD). Lifewire. Software and Apps.
