“Due Payment-Invoice” email scam (fake) - Free Guide
“Due Payment-Invoice” email scam Removal Guide
What is “Due Payment-Invoice” email scam?
“Due Payment-Invoice” email scam attempts to steal your email login details
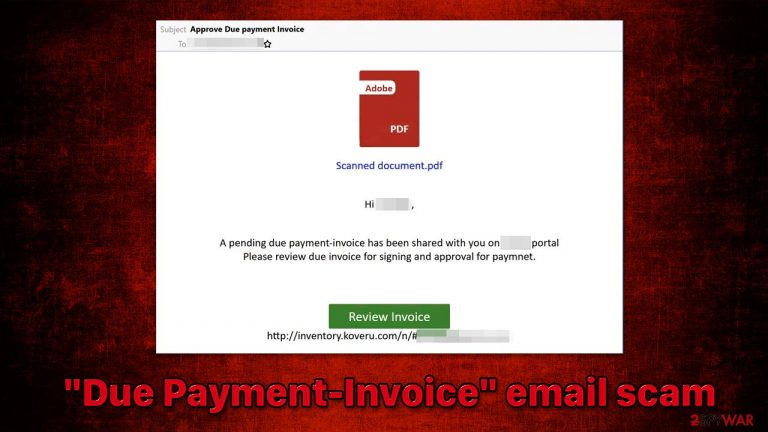
“Due Payment-Invoice” is a phishing email you may receive one day in your inbox. With the subject line “Approve Due payment Invoice,” the message itself claims that an invoice has been shared with the user on a website, which needs to be reviewed. After users click the “Review Invoice” button, they are redirected to a spoofing page, where they are asked to enter their email credentials.
Please do not trust anything that's shown within the “Due Payment-Invoice” email or links that lead to the rogue website. The main goal of cybercriminals is to make sure that you provide your email login data so that it could later be misused in various ways. If you enter your credentials, they might be stolen by cybercriminals as you may receive additional phishing messages or infected attachments, the opening of which would result in malware infection.
| Name | “Due Payment-Invoice” |
| Type | Phishing, scam, fraud, fake email |
| Distribution | Malspam – the attackers send thousands of emails in bulk to steal as many email credentials as possible |
| Operation | Claims that users have received an invoice in a PDF format that has to be reviewed via the provided link. Asks people to enter their email login details |
| Dangers | Personal information disclosure to malicious parties, virus infections |
| Removal | As a precautionary measure, scan your device with SpyHunter 5Combo Cleaner anti-malware software |
| Other tips |
The email message in detail and what to look out for
Operators of the “Due Payment-Invoice” email scam message run a relatively simple scheme – they provide a reason for users to follow the malicious link and hope that some would get tricked.
Subject: Approve Due payment Invoice
Scanned document.pdf
Hi [name],
A pending due payment-invoice has been shared with you on [name] portal
Please review due invoice for signing and approval for paymnet.Review Invoice
http://inventory.koveru.com/n/#[string]
Quite often, phishing emails use logos and other attributes of well-known companies, such as Netflix or Webmail, to make the whole scheme more believable. This time, the scammers didn't bother to provide any of that and simply explain that there is an invoice to be “reviewed” by the user. Except that it's a ridiculous claim in the grand scheme of things.
While private documents might be shared on various cloud storage services for security or other reasons, there are several “buts” here. For example, you should always check the “From” field, which would point to who sent you the email. If you see your own email there, it is not legitimate. Likewise, random email addresses are likely to be malicious.
However, there are quite a few question marks that would arise for users. For example, how did the crooks know their name? Even though it is true that spam emails usually fail to identify users by their name, some might easily do it if the email address they are sending the message to was previously compromised.
For example, whenever you enter your email address and some other information on a particular website, it may be stored on the online database by that website. Unfortunately, not every website uses adequate security measures to secure these databases, and they get hacked and user information stolen. Usually, credentials and other personal data are stored ciphered so that hackers cannot access them easily, although many websites still resort to easily bypassable encryption.[1]
This tactic is commonly used in very widespread email scams like “I regret to inform you about some sad news for you” or “It's Unpleasant To Start The Conversation With Bad News,” which are known for their bitcoin extortion techniques.
How malicious emails are operated
Email spam, otherwise known as malspam,[2] remains one of the most prevalent methods of distribution of malware and phishing attempts. What makes it so convenient is that cybercriminals do not send these emails one by one to users but rather use a botnet[3] – numerous infected computers that continue to send spam without their owners knowing anything about it. This is precisely how you have received the “Due Payment-Invoice” scam email.
While in most cases, advanced email provider security scanners are capable of filtering spam and placing it into the Junk section of your email account, it is not always the case. Likewise, while sometimes legitimate messages could end up in Junk, too, you should always treat them with extreme caution, as more often than not, they are actually malicious.
What to do after receiving the “Due Payment-Invoice” email scam
It's best not to click anything on the scam email you receive since there may be booby-trapped links or harmful payloads included as attachments. Even clicking the inserted hyperlink may not get you into trouble (as long as you have reputable security software installed on your system), but filling out your account information, clicking links, or downloading files from the rogue website might.
If you have been unfortunately tricked by the scam and entered your email credentials into the spoofing website, you should be extremely cautious. Here are a few tips that should help you to stay safe:
- If you entered your email and password into the fake page, you should change your password right now;
- If you reuse the same password on any other accounts (which you should never do, by the way!), you should change the password there as well;
- Expect to receive other fake emails filled with malicious content – do not interact with them;
- If additional information was stolen during a data breach, your phone or other details might also be known to crooks, so remember that they may use other methods to contact you, such as your phone number;
- Scan your system with powerful SpyHunter 5Combo Cleaner or Malwarebytes anti-malware to be sure it's not infected with viruses; if so, employ FortectIntego after malware removal to make sure your system's integrity is not damaged and you are not suffering from random crashes, errors, and other stability issues.
How to prevent from getting spam tools
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ What is Data Encryption?. Kaspersky. Resource Center.
- ^ Malspam: A simple and traditional attack technique that continues to be favorite among bad actors. Cyware. Threat Intelligence Solution Company.
- ^ Botnet. Wikipedia. The free encyclopedia.
