Zobm ransomware (Removal Guide) - Decryption Methods Included
Zobm virus Removal Guide
What is Zobm ransomware?
Zobm ransomware is malicious software that locks all personal files on the host machine and then asks for a ransom for the decryption tool

Zobm ransomware is a variant of the Djvu virus family and was first spotted by security researcher Amigo-A[1] at the end of November 2019. The malware is designed to lock all pictures, documents, videos, databases, and other files and then demand ransom to be paid for their recovery. Nevertheless, even paying criminals might not result in a successful outcome from a difficult situation Zobm ransomware victims found themselves in.
Known for being distributed via software cracks and pirated program installers,[2] Zobm ransomware launches the malicious executable immediately upon infiltration and begins the predetermined changes to the Windows system. The malware then locks all the data on the machine with the help of RSA and then appends .zobm marker to each of the files, restricting the access. Additionally, the malware drops ransom note _readme.txt, which notifies users that they need to contact hackers via datarestorehelp@firemail.cc or datahelp@iran.ir and pay a ransom of $980/$490 in order to retrieve decryption software from the attackers.
While it is true that the Zobm virus belongs to the new wave (more improved) of Djvu variants, there is a chance that malware used a hard coded key[3] to lock the data, in case of which file recovery might be possible with the help of Emsisoft's decrypter.
| Name | Zobm ransomware |
| Type | Cryptovirus, file locking malware |
| Malware family | Zobm ransomware is a variant of STOP/Djvu ransomware family |
| Infection means | Djvu malware versions are usually spread via torrent/warez sites and are disguised as software activators/cracks |
| Related files | setup.rar |
| Cipher used | All the data on the host machine is encrypted with the help of RSA encryption algorithm |
| File extension | Most personal files, such as .pdf, .doc, .mpg, .mp3, .html, and others, are appended with .zobm file extension and can no longer be accessed by the owners |
| Ransom note | _readme.txt is dropped into each of the affected files folders |
| Contact | Users are prompted to contact cybercriminals via datarestorehelp@firemail.cc or datahelp@iran.ir emails |
| Ransom size | $490 if contacted within 72 hours of the infection; later the price for Zobm doubles and users are asked $980 |
| File decryption options |
|
| Malware removal | Use powerful security software to eliminate ransomware from the machine |
| System recovery | Malware might introduce multiple modules on the system or import additional payloads (Djvu is known to be bundled with AZORult banking trojan in the past), each one might affect the system differently, and modify various Windows files. In order to recover from system damage and avoid reinstallation of the OS, we recommend scanning it with FortectIntego post-termination |
While some ransomware viruses self-delete after they perform the encryption of the data, Zobm ransomware removal is necessary as it was not spotted exiting the system post-infection. For that, users can resort to various security software tools that can recognize the infection. In some cases, accessing Safe Mode with Networking might be mandatory – we provide the instructions in the recovery section below.
Various Djvu versions were previously spotted modifying the Windows “hosts” file, which prevents them from accessing security-related websites. Thus, after you remove Zobm ransomware from your machine, make sure you delete the “hosts” file located in C:\Windows\System32\drivers\etc\ in order to access the web without restrictions again.
Note that Zobm ransomware virus might also drop additional modules on the machine – these can steal sensitive information from your computer, including banking credentials or other login details. Therefore, it is vital to scan the host machine with anti-malware software as soon as possible, although it is also important to prepare a backup of encrypted files.

Zobm ransomware operation and ransom demands
Unlike most of the other deceptive malware, the goal of Zobm ransomware is not to remain hidden from the computer owner. In fact, malware authors want to ensure that victims know what happened to their machines (some users are not aware of what ransomware is and how it works) – their only interest is to receive payments in Bitcoins.
However, before the obvious infection symptoms develop, Zobm ransomware starts from preparing the machine for the encoding process, which usually does not take that long (depending on the amount of data located on the device and its connected networks). The malware performs the following actions:
- Zobm virus is launched from an executable which is usually randomly named and placed into %AppData%, %Temp%, %LocalAppData% or another folder;
- Shadow Volume Copies deleted with “vssadmin.exe Delete Shadows /All /Quiet” command to prevent automatic data recovery;
- Windows registry altered in order to retain persistence;
- Communication with Command and Control server established;
- Windows “hosts” file deleted to prevent users from seeking help online.
Once these and few other preparations are complete, the Zobm file virus scans the system for files to encrypt and usually launches a fake Windows update window to confuse victims and avoid any suspicious due to system lag during the process. After this, the malware drops the ransom note _readme.txt, which states:
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-4NWUGZxdHc
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
datarestorehelp@firemail.ccReserve e-mail address to contact us:
datahelp@iran.ir
Your personal ID:
Zobm ransomware authors are offering various perks to those who are willing to pay, including the 50% discount if contacted early, as well as test decryption service. Regardless of this, you should remember that these people are cybercriminals and not your friends – they do not care whether you will get your data back or not. Therefore, it is possible that, even after paying the ransom, Zobm ransomware decryptor might never be obtained.
While contacting and paying hackers is not recommended by most security experts,[4] some users might use it as a last resort. Nevertheless, we highly advise you to stay away from crooks and instead choose to recover files by using alternative methods we provide below.
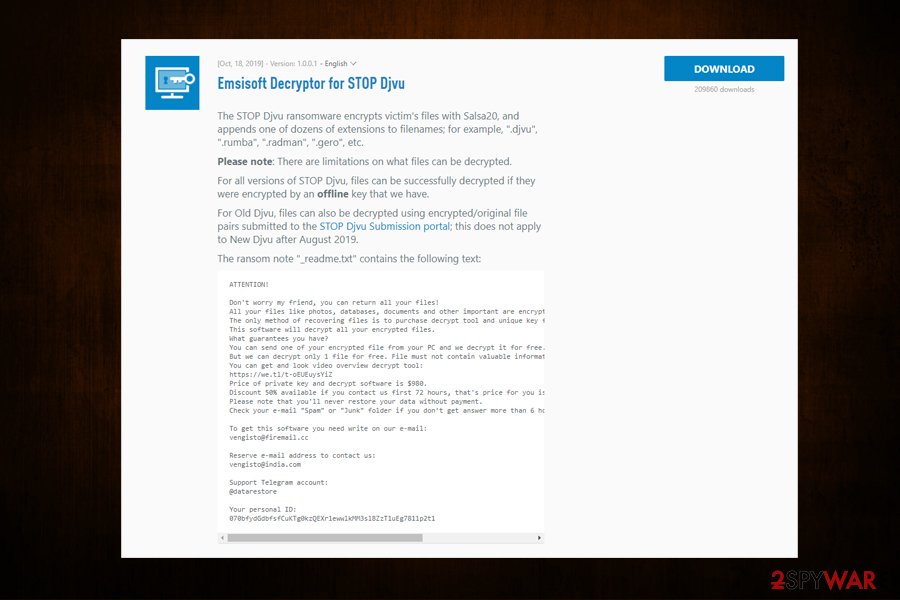
Software cracks – the main reason of Zobm ransomware infection
Peer-to-peer file sharing has been a problem for multiple industries, as it allows anyone having a legitimate copy of software/music/movie or other copyrighted material to share it online with people around the globe. While this gave an opportunity to many to access entertainment that was unavailable in their country of residence, it also initiated a variety of copyright laws. Therefore, in 2002, the file-sharing practices were banned when it comes to copyright material,[5] although there are still thousands of websites offering illegal software, pirated videos, and similar content for free (despite major sites going down and owners put to jail).[6]
Besides being an illegal activity, torrents are a hub for cybercriminals, as these sites are usually poorly regulated and allow malicious ads of being inserted directly into the sites, as well as hosting the malicious content in the first place. While the goal of websites authors is not necessarily infecting users with malware, due to inadequate protection and regulations, malicious actors can upload malware payloads, which might seem just like another executable to crack a piece of software.
Therefore, cracks are extremely dangerous, as they will most certainly be detected by anti-malware software due to their operation principle (i.e., they are designed to alter the code of the software, which is considered a malicious activity). Even after scanning the crack file, users will not be able to determine whether the tool is only designed to cheat the way into the legitimate software for free or also download and install a secondary payload of ransomware. Thus, keep that in mind, and never download pirated software installers or keygens/cracks.
Finally, you should also be aware that hackers might use various other methods for malware distribution, including:
- Exploits
- Malicious ads
- Spam emails
- Poorly-protected RDP connections
- Fake updates. etc.
Make sure you are running the most up-to-date security software and backup our files regularly if you want to avoid facing data loss due to ransomware infection in the future.
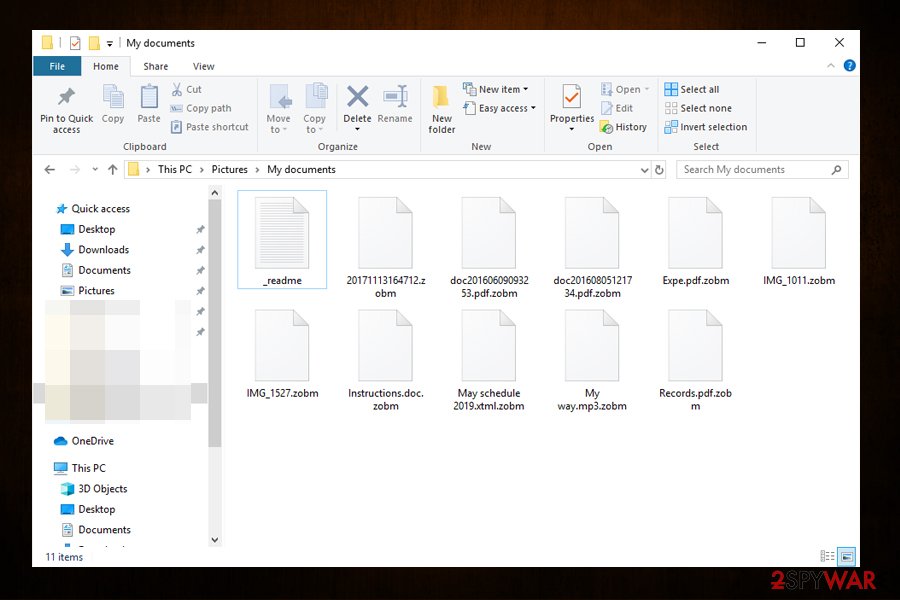
Get rid of Zobm ransomware along with all its modules or secondary payloads
Zobm ransomware removal should not be difficult to accomplish, as long as you have a reliable tool to do that. Because Djvu variants are being released in quick succession, however, be aware that not all security solutions might detect the payload in the first place. Therefore, we suggest scanning the machine with several anti-malware tools, such as SpyHunter 5Combo Cleaner and Malwarebytes. Nevertheless, it would be best to access Safe Mode with networking prior to that to enable security software to perform its actions without interruptions – we provide the details below. Note that you need to prepare backups of the encrypted files, as Zobm virus termination might render them useless permanently.
Once you remove Zobm ransomware from your machine, you can attempt to recover your data. As previously mentioned, there are several things you could do before giving up or deciding to pay the ransom – you can find all the instructions in our recovery section below.
Getting rid of Zobm virus. Follow these steps
Manual removal using Safe Mode
In some cases, the Zobm file virus might render security software unusable. To avoid that, access Safe Mode with Networking as explained below:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Zobm using System Restore
You can also try to eliminate the virus by using System Restore:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Zobm. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Zobm from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Zobm, you can use several methods to restore them:
Data Recovery Pro might be useful when trying to recover .zobm files
The less the affected machine is used post-infection, the more chances there are to recover at least some amount of data with tools like Data Recovery Pro.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Zobm ransomware;
- Restore them.
Windows Previous Versions Feature might be successful
If you had System Restore function enabled before the ransomware attack, you could use Windows Previous Versions Feature to recover files one-by-one.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer method might retrieve all your data
If the virus failed to delete Shadow Volume Copies, you should use ShadowExplorer to recover all your files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Make use of Emsisoft's decrypter
Emsisoft recently released a decryption service that helps victims who were affected by Djvu variants released before August 2019. Zobm ransomware belongs to the undecrytable versions of the virus. However, if the data was encrypted with a hard-coded key, there might be a chance of recovering files with Emsisoft's decrypter.
You can also ask Dr.Web for help if you are willing to pay for the service (only works for certain file types).
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Zobm and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Amigo-A. New variant of #STOP #Ransomware. Twitter. Social network.
- ^ Ransomware statistics for 2019: Q2 to Q3 report. Emsisoft. Security blog.
- ^ Hard coding. Wikipedia.The free encyclopedia.
- ^ NoVirus. NoVirus. Cybersecurity news and articles from the UK.
- ^ Eamonn Forde. Oversharing: how Napster nearly killed the music industry. The Guardian. International magazine.
- ^ Jon Russell. Police Finally Arrest The Third And Final Founder Of The Pirate Bay. Tech Crunch. Startup and Technology News.







